BrowserStack user provisioning using Open SCIM
Connect your IdP with BrowserStack’s SCIM connector
Introduction
BrowserStack’s Open SCIM connector, based on System for Cross-domain Identity Management (SCIM) standard, enables end-users to enable Auto User Provisioning for their account. This document describes how to configure Auto User Provisioning.
Prerequisites
- Enterprise plan on BrowserStack.
- You need to have administrator access to your organisation’s IdP.
- Your SSO needs to be enabled before User Provisioning. Follow the instructions to set up SSO .
- User with Owner permissions can setup user provisioning on BrowserStack.
Supported Features
The BrowserStack’s User Provisioning integration currently supports the following features:
- User provisioning & de-provisioning
- Attribute assignment for users on BrowserStack:
- Role assignment
- Product access
- Team assignment
Open SCIM Endpoints
Service Provider Configuration
The Service Provider Config endpoint provides metadata indicating the BrowserStack Server’s authentication scheme and its support for optional or configurable SCIM features. Service Provider Config objects are defined by RFC 7643, section 5.
GET https://www.browserstack.com/scim/v2/ServiceProviderConfig
Resource Types
The Resource Types endpoint lists all of the SCIM resource types configured for use on this BrowserStack Server. Clients may use this information to determine the endpoint, core schema, and extension schemas of any resource types supported by the server. This endpoint does not provide resource type information about SCIM sub-resources.
The response is formatted as a list response, with one or more resource type objects in the Resources field. Resource type objects are defined by RFC 7643, section 6.
GET https://www.browserstack.com/scim/v2/ResourceTypes
User Resource Type
The Resource Type endpoint retrieves a specific SCIM resource type, specified by its ID (we only support User resource). Resource type objects are defined by RFC 7643, section 6. This endpoint does not provide resource type information about SCIM sub-resources.
GET https://www.browserstack.com/scim/v2/ResourceTypes/User
- In order to update an existing user resource, make use of the
PUTendpoint. - If your IdP does not support the
PUTendpoint, you can make use of thePATCH /scim/v2/Users/{id}endpoint.
PATCH request:
{
"schemas": [
"urn:ietf:params:scim:schemas:core:2.0:User"
],
"Operations":[{"op": "add", "path" : "urn:ietf:params:scim:schemas:extension:Bstack:2.0:User:bstack_product", "value" : "App-Live-Testing,App-Automate-Testing"}]
}
Schemas
The Schemas endpoint lists the SCIM schemas configured for use on this BrowserStack Server, which define the various attributes available to resource types. This endpoint does not provide schema information about SCIM sub-resources.
The response is formatted as a list response, with one or more schema objects in the Resources field. Schema objects are defined by RFC 7643, section 7.
GET https://www.browserstack.com/scim/v2/Schemas
Individual Schema
The Schema endpoint retrieves a specific SCIM schema, specified by its ID (we only support User Schema), which is always a URN. Schema objects are defined by RFC 7643, section 7, section 7. This endpoint does not provide schema information about SCIM sub-resources.
GET https://www.browserstack.com/scim/v2/Schemas/urn:ietf:params:scim:schemas:core:2.0:User
Get your access keys
-
Sign In to BrowserStack account as Owner.
-
Go to Account > Security and select Authentication from the side-nav menu.
-
Under Auto User Provisioning, select Configure.
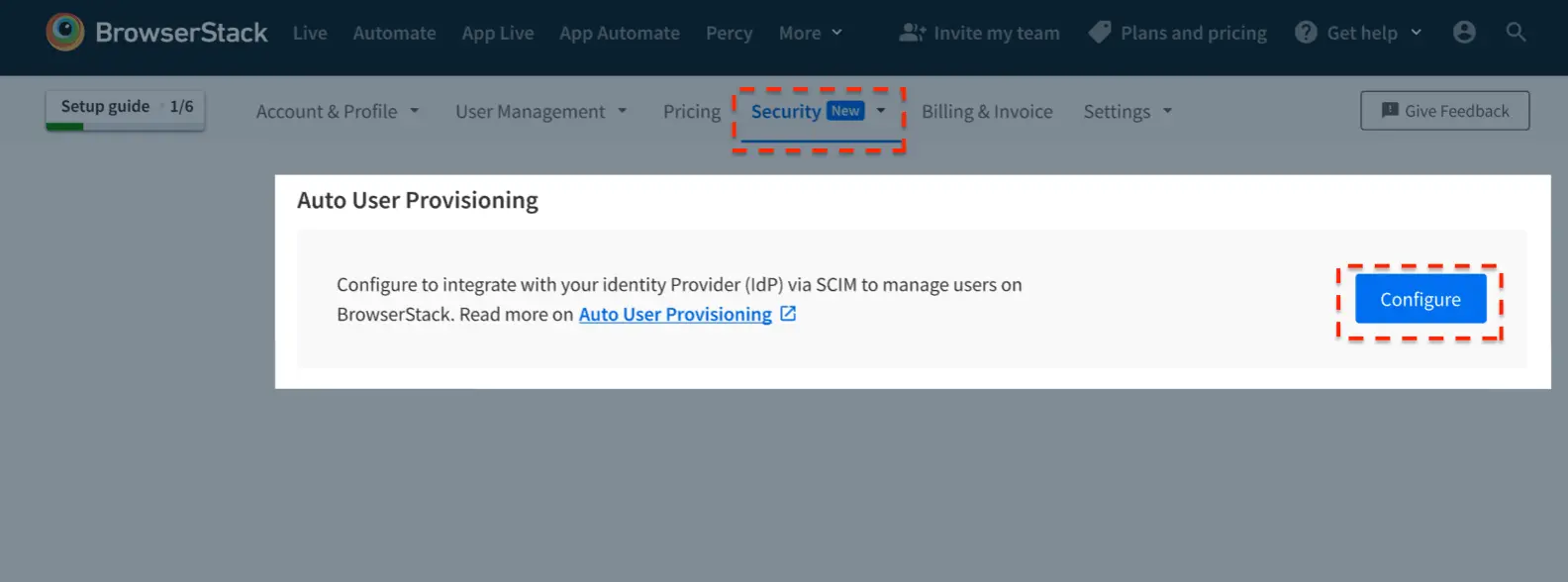
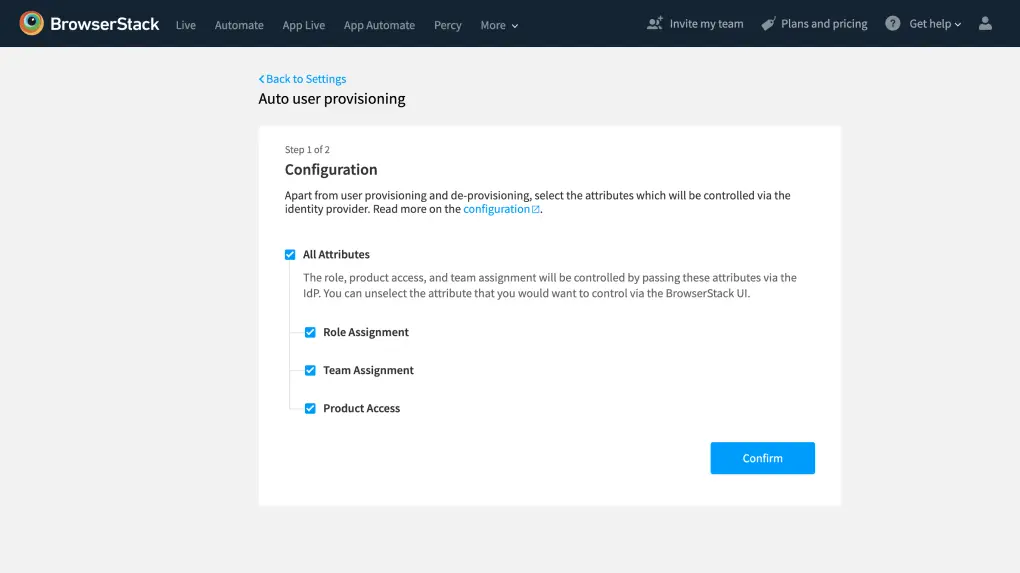
-
Select the user attributes that you want to control via IdP. Ensure that these attributes are supported by your IdP. Go to the next screen:
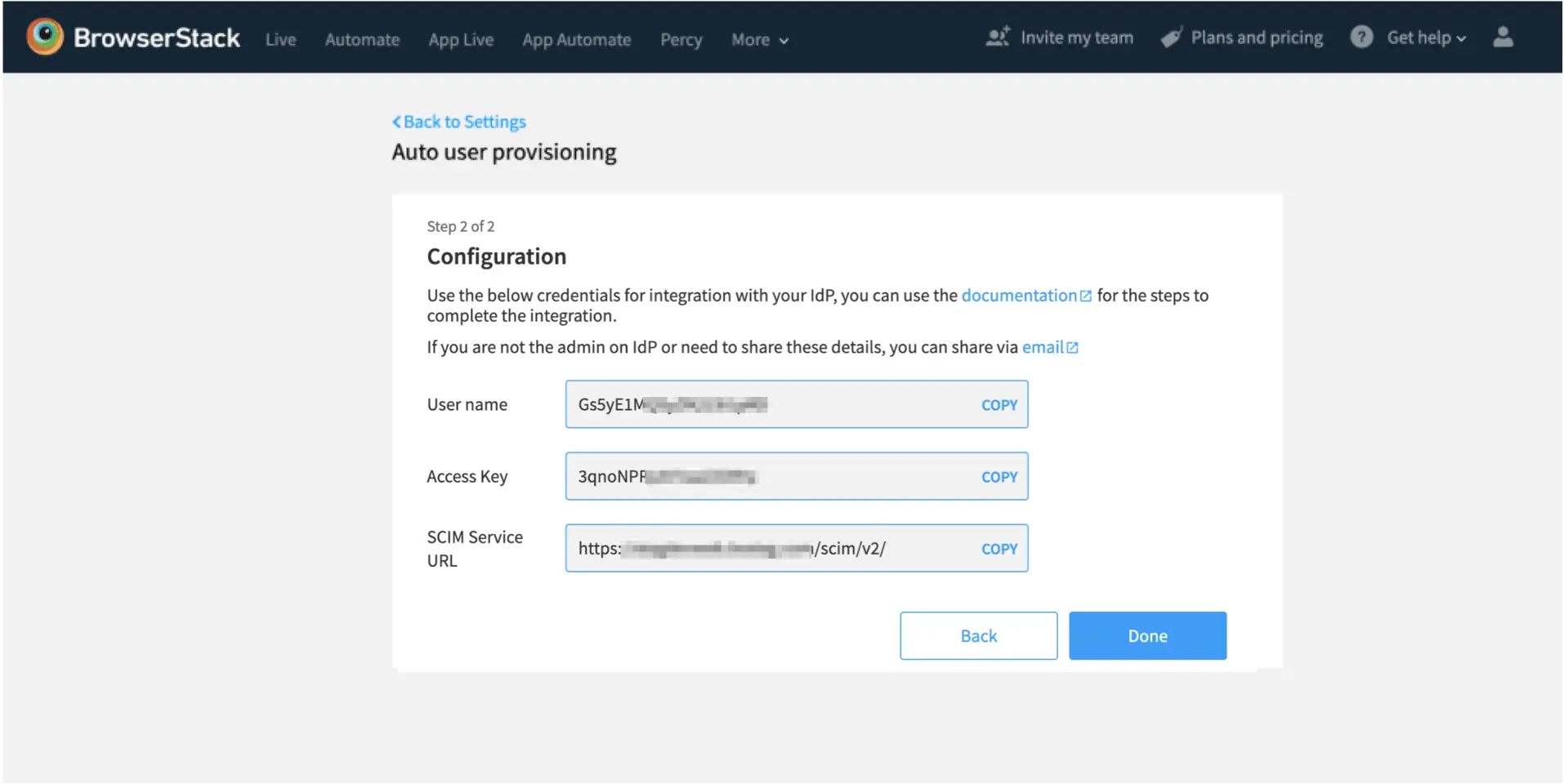
- Copy the credentials, will be used on your IdP for authentication
-
SCIM Base URL: The SCIM URL of BrowserStack server
https://www.browserstack.com/scim/v2 -
Authorization Details: We support Authorization Header as authorization type with Basic as well Bearer token method for authorization and does not enforce specific methods for authorization.
- For basic authorization: Copy User name and Access key from the BrowserStack and configure it on the connector.
-
For bearer token authorization: Copy Access key from the BrowserStack and configure it on the connector.
-
SCIM Base URL: The SCIM URL of BrowserStack server
-
Save and Enable on BrowserStack, once you have set it up on your Identity Provider
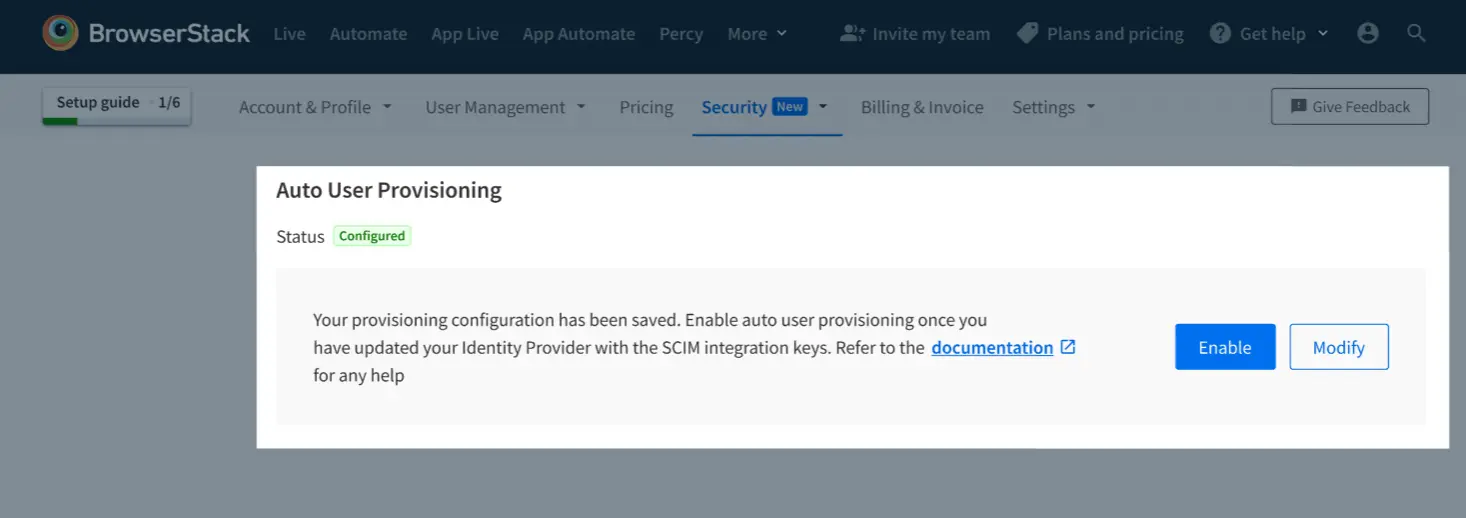
- Verify/Test on your identity provider (IdP) to check the configuration.
Set-up on your Identity Provider
- Find SCIM Connector on your IdP.
- Follow the steps to configure it, or use the details in Open SCIM endpoints section to configure it.
- Make sure that you configure the following in the connector:
a. SCIM Base URL: The SCIM URL of Browserstack serverhttps://www.browserstack.com/scim/v2
b. Authorization Details: We support Authorization Header as authorization type with Basic as well Bearer token method for authorization and does not enforce specific methods for authorization.
- For basic authorization: Copy User name and Access key from the Browserstack and configure it on the connector.
- For bearer token authorization: Copy Access key from the Browserstack and configure it on the connector.
- Click on Verify / Test to check the configurations.
Custom Attributes
In order to control Role, Team and Product Access from IdP, add the following attributes on IdP’s end:
-
Attribute Name:
primary_role -
External Name:
bstack_role - Default role assigned is
User. This is possible in two scenarios:- Unexpected, empty or no value specified
- Role attribute is controlled from Account section
- Expected values when attribute controlled by OpenSCIM:
| Attribute Value | Role Update |
|---|---|
| User | User will be assigned |
| Admin | Admin will be assigned |
| Owner | Owner will be assigned. The current owner will be replaced with the new owner. The current owner will become a user. |
|
No Value Empty or Any other value |
The user is created as User by default. |
-
Attribute Name:
primary_team -
External Name:
bstack_team - By default a user is added to Group/Organization on BrowserStack with role as
User. This is possible in two scenarios:- Empty or no value specified
- Team attribute controlled from Account section
- Supported attribute values (when attribute controlled by OpenSCIM)
| Attribute Value | Team Update |
|---|---|
| team_name | The user gets added to the existing team if a team exists with the same name. Otherwise, a new team will be created with the passed attribute value. |
| No value/Empty | The user is assigned as part of Group |
-
Attribute Name:
primary_product -
External Name:
bstack_product - By default, no product access is assigned. This is possible in two scenarios:
- Unexpected, empty or no value specified
- Product attribute is controlled from Account section
- Supported attribute values (when attribute controlled by OpenSCIM):
| Attribute Value | Product Update |
|---|---|
| Browser-Testing | Live Automate |
| Visual-Testing | Percy |
| Automate-Testing | Automate |
| Live-Testing | Live |
| Mobile-App-Testing | App Live App Automate |
| App-Automate-Testing | App Automate |
| App-Live-Testing | App Live |
| App-Percy | App-Percy |
| Accessibility-Testing | Accesssibility Testing |
| Test-Management | Test Management |
| Test-Observability | Test Observability |
Browser-Testing,Visual-Testing
To know the structure of the custom attributes, hit the following endpoint:
GET https://www.browserstack.com/scim/v2/Schemas
Troubleshooting
We would suggest that as a first step, please put all the users you currently have on the BrowserStack account into the IdP connector app via the assignment tab. This would avoid any discrepancies between the user lists on your IdP and Browserstack.
User Already Present On BrowserStack
Resolution: User already presents on BrowserStack under a different organization, please get the account deleted before provisioning the user.
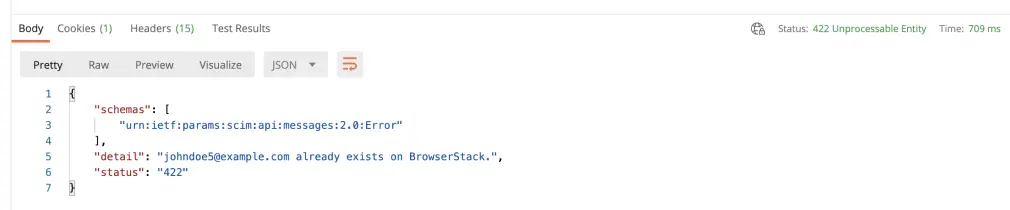
Invalid parameter/attribute values passed for Role or Product
Resolution: Role/Product is not a valid use-case, please use the attribute values provided above.
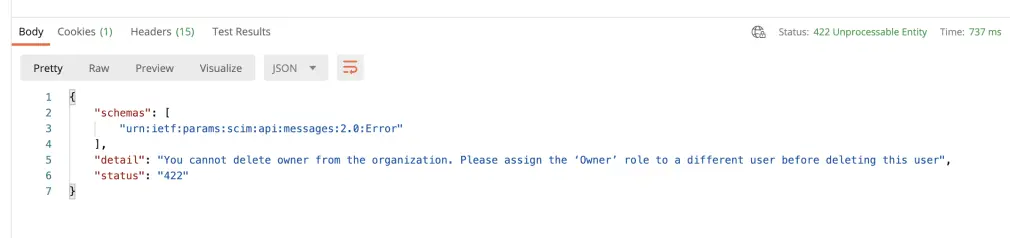
Owner Deletion
Resolution: Assign ownership to a different user before deletion of this user. The owner cannot be deleted, BrowserStack account needs a user to have Owner role assigned.
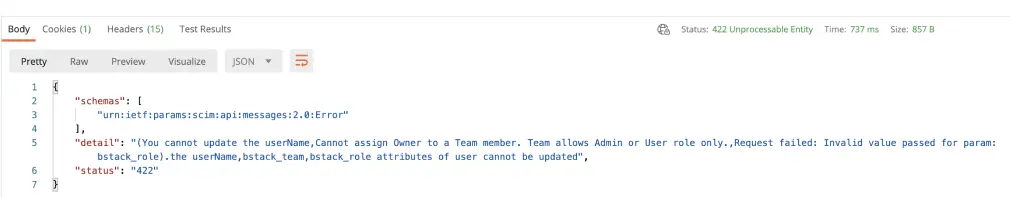
Incompatible Attributes
Resolution: You are assigning incompatible user attributes, for example, the Owner cannot have a team assigned.
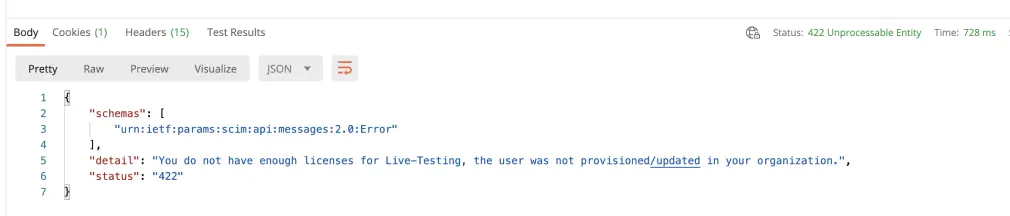
Licenses Not Available
Resolution: You have used up all your licenses for the product, please unassign users or add more licenses. Contact your Account Executive to get information on adding licenses.
Escalation/Support
Please connect with support@browserstack.com for any escalations or support.
We're sorry to hear that. Please share your feedback so we can do better
Contact our Support team for immediate help while we work on improving our docs.
We're continuously improving our docs. We'd love to know what you liked
We're sorry to hear that. Please share your feedback so we can do better
Contact our Support team for immediate help while we work on improving our docs.
We're continuously improving our docs. We'd love to know what you liked
Thank you for your valuable feedback!
