With the constant threat of data breaches and cyberattacks, organizations must proactively assess their systems and applications to identify security risks. A penetration test provides a structured assessment to uncover vulnerabilities and evaluate the effectiveness of existing controls, with the findings documented in a penetration test report.
Overview
A penetration test report summarizes the results of a simulated security assessment designed to identify vulnerabilities within systems or applications. It provides actionable insights to help organizations strengthen their security posture.
Key components to include:
- Executive Summary: Brief overview of objectives, scope, and overall security posture.
- Key Findings: Summary of critical vulnerabilities and their impact.
- Engagement Summary: Scope, timeline, and targets of the test.
- Test Results: Detailed list of all identified vulnerabilities.
- Ratings and Risk Scores: Severity levels to prioritize remediation.
- Vulnerability Details: Technical descriptions and evidence.
- Remediation Recommendations: Clear steps to address issues.
- Testing Methodology: Outline the tools and processes used.
- Limitations: Any constraints impacting the test.
- Compliance References: Relevant industry standards and regulations.
- Acronym Appendix: Definitions of technical terms.
- Conclusion: Overall security assessment and next steps.
Benefits of a Penetration Test Report
- Identifies security vulnerabilities clearly
- Prioritizes risks by severity
- Guides informed security decisions
- Supports regulatory compliance
- Provides documented evidence for stakeholders
- Enhances communication between teams
- Offers actionable remediation steps
- Drives continuous security improvement
This article covers the purpose, key components, and benefits of a penetration test report, along with best practices for interpreting its findings.
What is a Penetration Test Report?
A penetration test report is a detailed document that presents the results of a security assessment aimed at identifying vulnerabilities in an organization’s systems, networks, or applications.
It summarizes the methods used during the test, the weaknesses discovered, their potential impact, and recommendations for remediation. This report is essential for guiding organizations in strengthening their security posture and reducing the risk of cyberattacks.
Read More: What is Mobile App Security Testing?
What is the Penetrating Testing Report format?
The penetration testing report format is a standardized structure designed to clearly communicate the findings and insights from a penetration test. It organizes information logically to ensure both technical teams and business stakeholders can understand and act on the results.
Consider the following elements prior to writing a pentest report:
- Specify the objectives of penetration testing
- Understand the plausible effects of a breach
- Describe the assessment procedure and any pertinent techniques
Key Components of Penetration Test Report
A penetration test report must deliver both strategic and technical insights, allowing organizations to understand vulnerabilities, assess their impact, and take informed steps toward remediation. The following sections should be included:
Executive Summary
The report should begin with a non-technical summary aimed at company executives. This section highlights key findings, the overall risk posture, and the next steps for remediation, written in plain language so that non-security stakeholders can grasp the implications.
Key Findings
Summarize the most critical vulnerabilities and their potential impact on the organization. This high-level overview helps prioritize what needs immediate attention.
Engagement Summary
Detail the scope of the engagement, including the systems, applications, and networks tested, the testing timeline, and any exclusions or constraints.
Test Results
Provide a comprehensive breakdown of all vulnerabilities identified during the assessment. Include technical descriptions of how each issue was discovered and how it could be exploited.
Ratings and Risk Scores
Assign severity levels to each vulnerability using a standardized framework like CVSS. This helps teams prioritize remediation based on risk level and potential business impact.
Vulnerability Details
Explain the nature of each vulnerability, the testing method used to find it, and how an attacker could exploit it. Use precise language that’s accessible to security teams, developers, and business stakeholders alike.
Remediation Recommendations
The most essential aspect of a pentesting report is its remediation recommendations, which explain how to fix the vulnerabilities you discovered to the organization. The primary reason a company invests in penetration testing is to determine how to address its most serious vulnerabilities. Testers must provide detailed remediation instructions for all affected systems.
To improve the efficacy of the recommendations, testers should conduct research to determine the most effective solution for each situation. For instance, one system’s vulnerability can be readily patched, whereas another system may not support patching and must be isolated from the network.
Strategic Recommendations
Beyond specific fixes, include broader suggestions to strengthen the organization’s overall security posture. For example, if the penetration test went undetected, recommend enhancing monitoring. If accounts have excessive privileges, suggest revising access control policies.
Testing Methodology
Describe the tools, frameworks, and techniques used during the test. This section promotes transparency and helps validate the credibility of the findings.
Limitations
Outline any restrictions that may have impacted the depth or breadth of the test. This includes systems excluded from scope, time constraints, or technical challenges.
Compliance References
Document findings to relevant regulatory or industry standards such as PCI DSS, ISO 27001, or NIST, supporting audit readiness and compliance reporting.
Acronym Appendix
Provide definitions for technical terms and abbreviations used throughout the report to ensure accessibility for non-technical stakeholders.
Conclusion
Conclude with a brief summary of the overall risk posture, key areas of concern, and recommended next steps for improving security.
How to write Penetrating Testing Report efficiently: Example
To write an efficient penetration testing report, it is important to follow a clear structure and include detailed, relevant information. Here is an example illustrating how to present key sections effectively.
1. The Executive Summary
The executive summary must contain an overview of the engagement and the high-level test outcomes. It can also provide an overall risk rating dependent on a particular risk matrix, and some risk recommendations.
- Overview
Client X contracted company Y to perform Penetration testing for the security controls in their IT systems to understand how effective those controls are. The company will also provide estimates of how susceptible the system is to data exploitation or breach.
- High-Level Test Outcomes
The purpose of the internal penetration test is to simulate the network-level actions of a malicious actor who has obtained access to the internal network zone.
Overall, CLIENT’s critical infrastructure presents a high-risk attack surface with major critical vulnerabilities that enable complete root access to multiple systems.
Both the EPO server and the Remote Desktop Server were vulnerable to EternalBlue; a remote terminal was opened on both by exploiting the SMBv1 vulnerability with a publicly available exploit module that remotely attacked the spoolsv.exe service over port 445 (SMB).
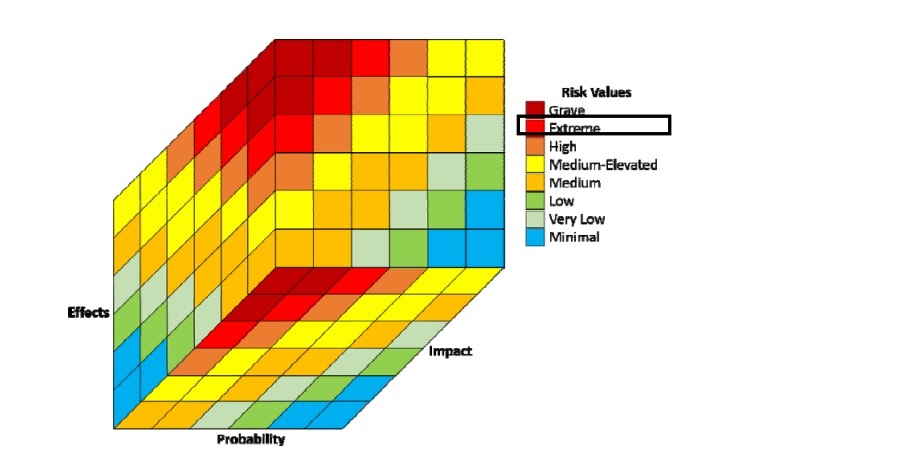
- Overall Risk Rating
It can be represented using risk matrix as shown below:
- Recommendations
Have a point-wise, prioritised list of recommendations, for e.g
- Patch essential systems (Microsoft Security Bulletin MS17-010 – Essential).
- Conduct Vulnerability Scans at least monthly (scan-patch-scan)
- Change passwords (10+ complex characters) on all systems containing ePHI.
2. Test Scope and Method
This section details the scope of the penetration tests carried out as well as the exact methods followed.
- Extent of Testing
The Client commissioned the Testing Company to perform the following penetration testing services:
- Technical pen testing at the network level against nodes in internal networks.
- Technical network-level penetration testing of internet-facing hosts.
- Social Engineering and phone-based phishing against CLIENT staff.
- Social Engineering and email phishing directed at CLIENT employee accounts.
- Test Scope Summary
Within the parameters of the penetration test were the following information environment zones:
- Internal Network: Example, the general internal networks of the Client
- External Network: The publicly accessible networks of the Client
Internal Phase Summary and Actions Taken
The ISA of TEST COMPANY conducted various reconnaissance and enumeration operations. Scanners for ports and vulnerabilities, along with other reconnaissance operations, uncovered significant security flaws.
The most worrisome vulnerabilities allow complete system takeover on critical servers, most notably the McAfee Security server, which if compromised could render the endpoint security for the entire internal network inoperable or ineffectual.
After compromising the server, a directory traversal was performed to seek for crucial data. The analyst was able to identify a large number of directories containing private patient information as well as a large number of other data that would fall under HIPAA and PCI compliance.
External Phase Summary and Actions Taken
The external phase of the penetration test focused on publicly accessible assets. Reconnaissance and monitoring were performed to identify potential entry points and malicious modifications to the systems.
Using Burp Suite and the network scanner NMAP, attacks were launched from the TEST COMPANY network over the Internet against CLIENT’s externally accessible assets.
3. Conclusions
The Conclusions section will contain a summary of the most likely scenarios for security compromise, and the implications of the same.
For example, represented below is a likely scenario and its implication to the client:
- Scenario: Most likely, an assailant would initiate an attack against CLIENT using social engineering techniques. Given that ETERNALBLUE is readily exploitable and that this is the most successful type of attack, this is the most likely compromise of the entire system. An ideal first target would be the McAfee Security Server; once an attacker has gained root access to this system, they can disable all the security controls and systems in place, allowing for much more evasive traversal of the internal network and potentially creating more targets without the hindrance of security systems.
- Implication: Based on the preceding testing activities, the overall average risk level is EXTREME. On critical security and file servers, it is trivial to compromise the entire system. These servers contain a plethora of important and confidential files that, if compromised, place the CLIENT at risk for hefty fines and significant business impact.
What is Penetration Testing?
A penetration test, also known as a pen test, is a simulated cyber attack against a computer system to identify exploitable flaws. In the context of web application security, penetration testing is typically employed to complement a web application firewall (WAF).
These vulnerabilities may exist for a variety of reasons, including misconfiguration, insecure code, inadequately designed architecture, or disclosure of sensitive information. The output is an actionable report that describes each vulnerability or chain of vulnerabilities exploited to obtain access to a target, along with the exploit steps, details on how to fix the vulnerabilities, and additional recommendations. Each discovered vulnerability is designated a risk rating that can be used to prioritise remediation tasks.
Read More: Website Accessibility Checklist
Why is Penetration Testing Important?
Understanding the importance of penetration testing helps organizations recognize its critical role in strengthening security and managing risks effectively. Key reasons why penetration testing matters include:
- Identifies Hidden Vulnerabilities: Penetration testing uncovers security weaknesses that automated tools like vulnerability scanners may miss, thanks to detailed manual analysis.
- Filters False Positives: Human expertise ensures only genuine vulnerabilities are reported, reducing false alarms and focusing remediation efforts.
- Demonstrates Real-World Risk: By attempting to exploit vulnerabilities as actual attackers would, penetration testing reveals the true extent of potential damage and data exposure.
- Tests Cyber Defense Effectiveness: It evaluates the responsiveness and capability of security controls such as firewalls, intrusion detection systems, and internal security teams during simulated attacks.
- Supports Security Investment Decisions: Provides tangible evidence of risk, helping management justify cybersecurity budgets and prioritize security improvements.
- Addresses Risks for All Organizations: Even businesses outside high-risk sectors, like manufacturing or construction, face threats from automated and opportunistic cyberattacks.
- Adapts to Changing Technology and Practices: Identifies risks introduced by trends such as remote working and Bring Your Own Device policies.
- Shifts Cybersecurity Responsibility to Management: Cyber risk is now a critical business risk that management teams must actively manage alongside legal, operational, and financial risks.
- Creates a Competitive Advantage: Strong security and regulatory compliance enhance reputation and trust with customers and partners.
- Mitigates Legal and Financial Consequences: Helps organizations comply with regulations like the Australian Privacy Act, which mandates breach disclosure and can impose significant penalties.
Best Practices to write Penetration Testing Report
The following practices help teams create clear, effective, and credible penetration testing reports:
- Understand the System Architecture: Gain a thorough understanding of how the system operates, how it processes and manages data, interacts with other services, and handles user requests before beginning the test.
- Highlight Both Strengths and Weaknesses: Include notes on well-secured areas and instances where security controls successfully blocked attacks, in addition to detailing vulnerabilities. This helps organizations recognize which defenses are effective.
- Document Findings During Testing: Write the report progressively as testing proceeds. Capture screenshots and record important events in real time to ensure a comprehensive and accurate final report.
- Clearly Document Testing Methods: Share the methodologies used during the test, such as reconnaissance techniques, attack selection rationale, and frameworks followed (e.g., NIST or SANS). This adds transparency and credibility to the findings.
- Define the Scope Precisely: Clearly outline the agreed-upon scope of the penetration test to meet client expectations and avoid legal or ethical issues. Testing outside the defined scope can lead to liability concerns.
Conclusion
A well-prepared penetration test report is essential for organizations to understand and address security vulnerabilities effectively. Clear documentation of findings, impact analysis, and remediation guidance supports informed decision-making and strengthens overall security.
Following best practices in report writing ensures that the results are accessible to both technical teams and business leaders, promoting ongoing security improvements.
While penetration testing focuses on identifying security weaknesses, comprehensive quality assurance across devices and browsers remains critical for delivering secure and reliable applications.
BrowserStack provides a robust cloud-based platform for cross-browser and cross-device testing, enabling development teams to verify functionality and performance different environments, supporting a strong foundation for secure software delivery.