BrowserStack SSO with Azure AD (aka Microsoft Entra ID) | SAML
Integrate your Azure AD directory with BrowserStack to set up Single Sign-On.
Single Sign-on integrates an external user directory with your BrowserStack Group. This document describes how to configure Single Sign-on when Azure AD is your identity provider.
In this tutorial, you’ll learn how to integrate BrowserStack with Azure Active Directory (Azure AD). When you integrate BrowserStack with Azure AD, you can:
- Control in Azure AD who has access to BrowserStack.
- Enable your users to be automatically signed-in to BrowserStack with their Azure AD accounts.
- Manage your accounts in one central location - the Azure portal.
To learn more about SaaS app integration with Azure AD, visit single sign-on with Azure AD documentation.
Prerequisites
To set-up and use Azure AD and BrowserStack Single Sign-on (SSO) feature:
- An Azure AD subscription. If you don’t have a subscription, you can get a free account.
- A user account in Azure AD with permission to configure provisioning (for example, Application Administrator, Cloud Application administrator, Application Owner, or Global Administrator).
- Enterprise plan on BrowserStack.
- By default, a user account with Owner permissions can setup SSO on BrowserStack.
Supported features
The BrowserStack & Azure AD Single Sign-on integration currently supports the following features:
| Description | |
|---|---|
| SP-initiated SSO: | End users of organization can sign in using BrowserStack Login page and then sends an authorization request to the Identify Provider. Once the IdP authenticates the user identity, the user is logged into BrowserStack. |
| IdP-initiated SSO: | End users of organization can log into the Identity Provider’s SSO page and then click on BrowserStack application icon to log into and open the BrowserStack. |
Configuration steps
A. Adding the BrowserStack app on Azure AD
To configure the integration of BrowserStack into Azure AD, you need to add BrowserStack from the gallery to your list of managed SaaS apps.
- Sign in to the Azure portal using either a work or school account, or a personal Microsoft account.
- On the left navigation panel, select the Azure Active Directory service.
- Navigate to Enterprise Applications and then select All Applications.
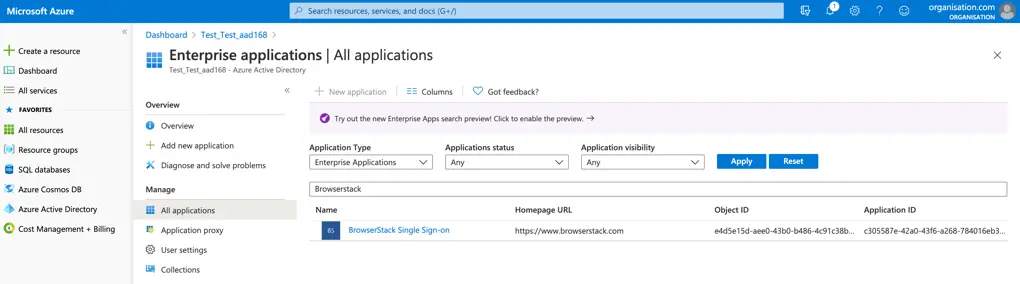
- To add a new application, select New application.
- In the Add from the gallery section, type BrowserStack in the search box.
- Select BrowserStack from the results panel and then add the app. Wait for a few seconds while the app is added to your tenant.
B. Setting up the BrowserStack app on Azure AD app
-
Click on Set up Single Sign-on card under Getting Started.
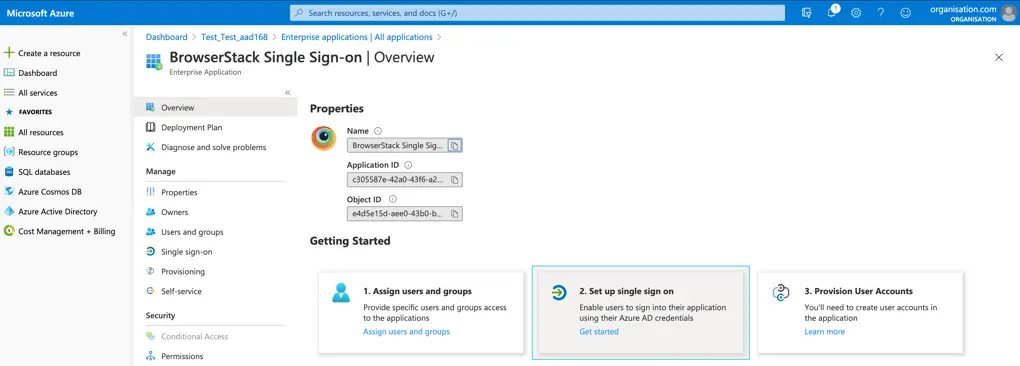
-
Sign-In to BrowserStack account as Owner.
-
Go to Account > Security and select Authentication from the side-nav menu. Click Configure under Single Sign On (SSO).
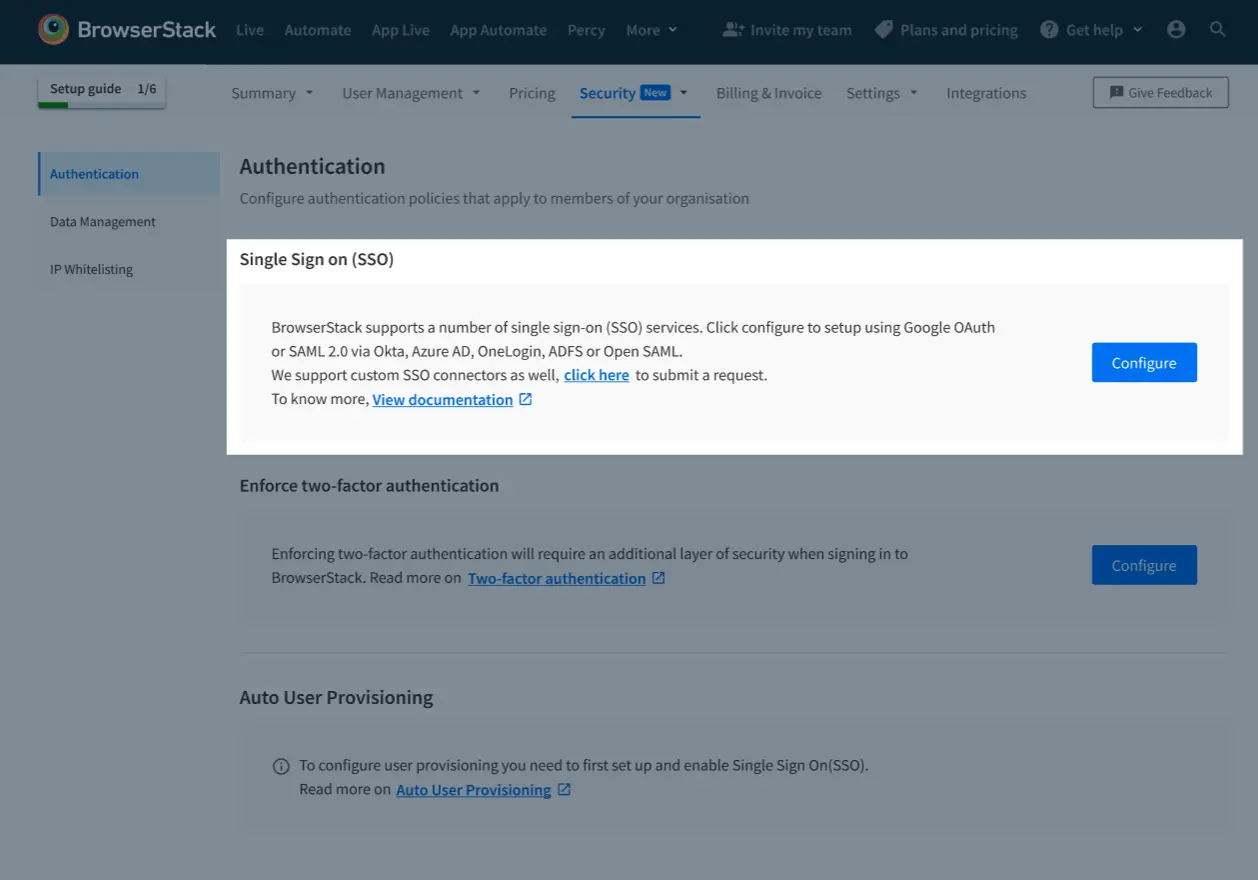
-
On the next screen, you will be shown all the Authentication services that BrowserStack supports, select SAML 2.0 and click Next.
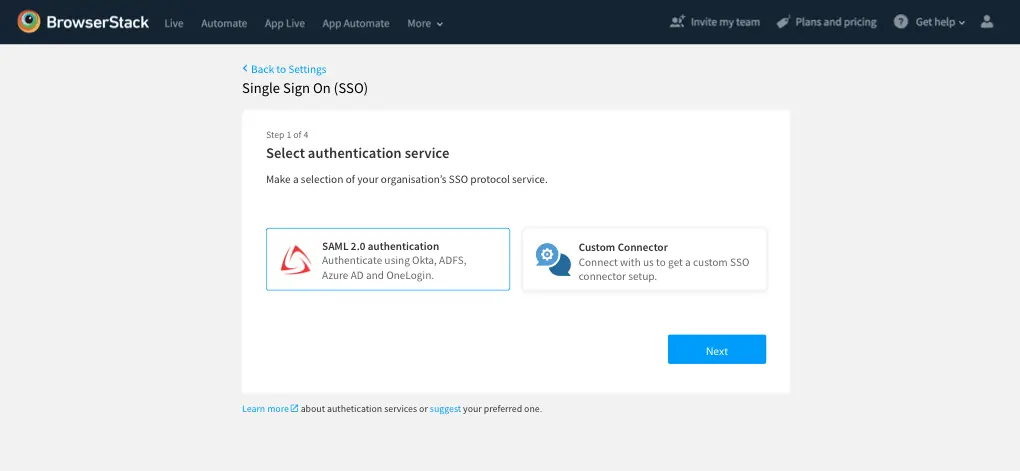
-
Choose Azure AD from the list of Identity Providers, and click Next.
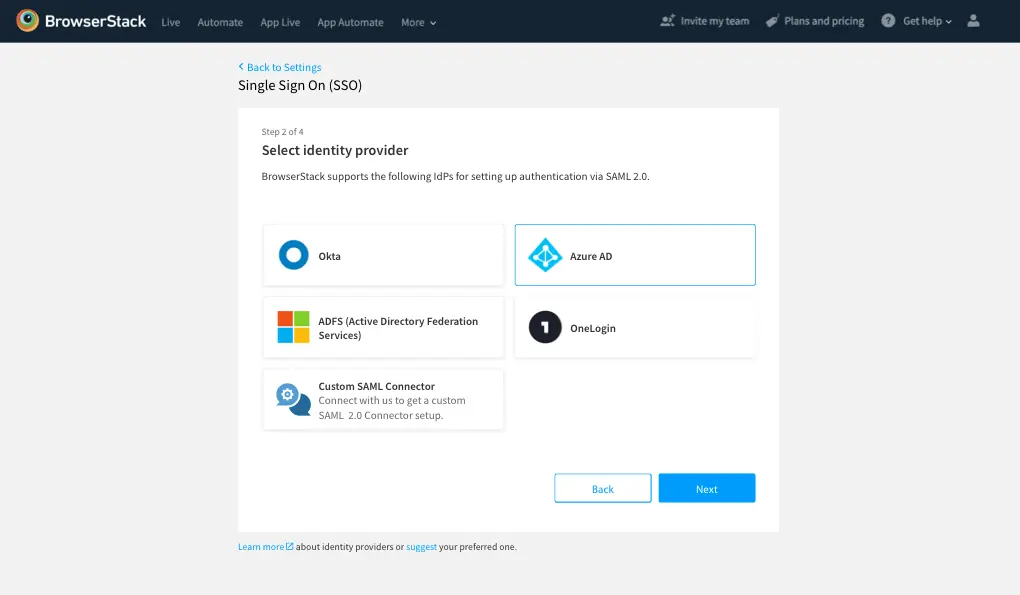
-
Copy the following from this screen:
a. SP initiated ACS URL
b. IdP initiated ACS URL
c. Entity ID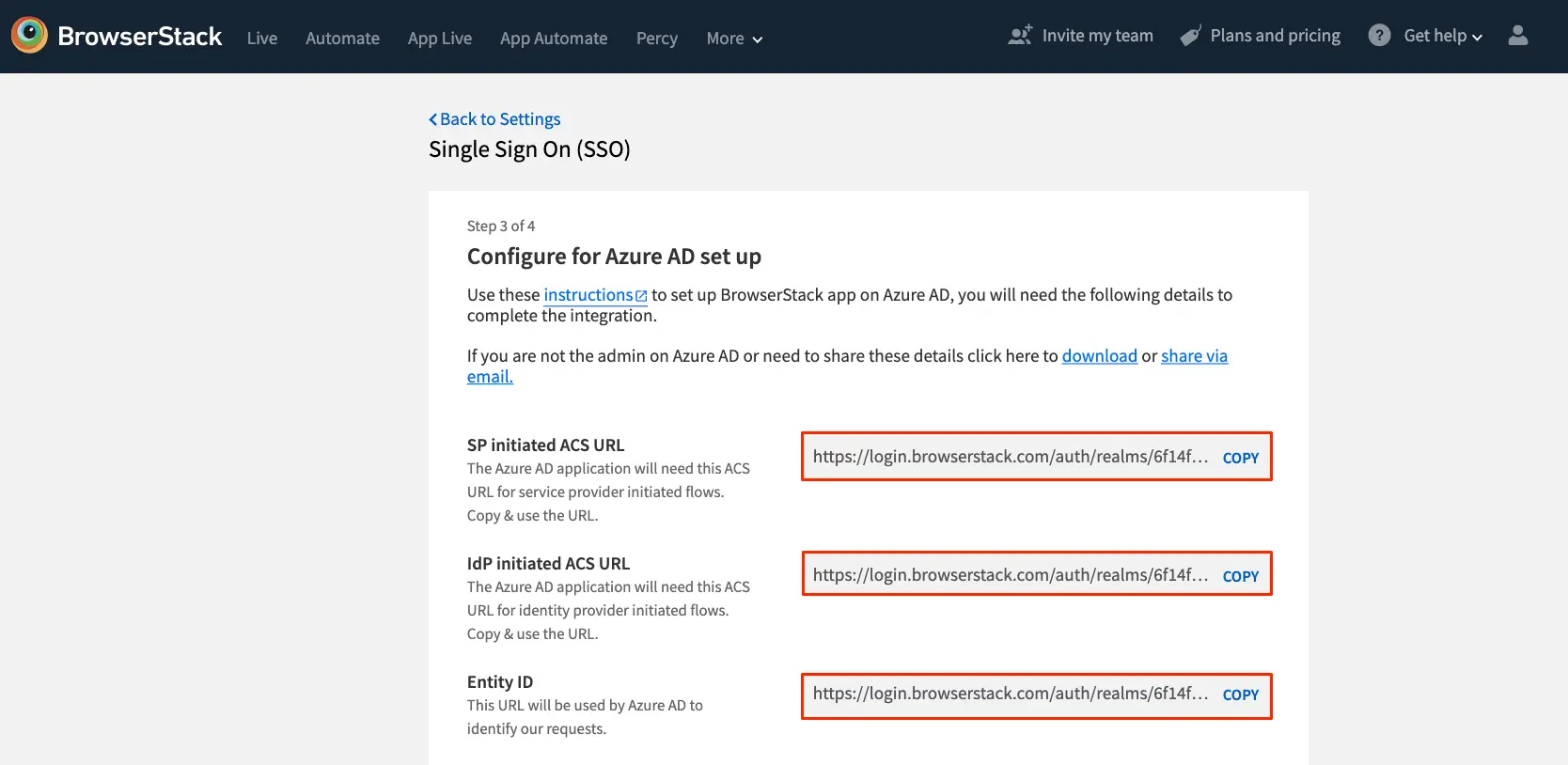
-
Head back to Azure AD application, and edit Basic SAML Configuration.
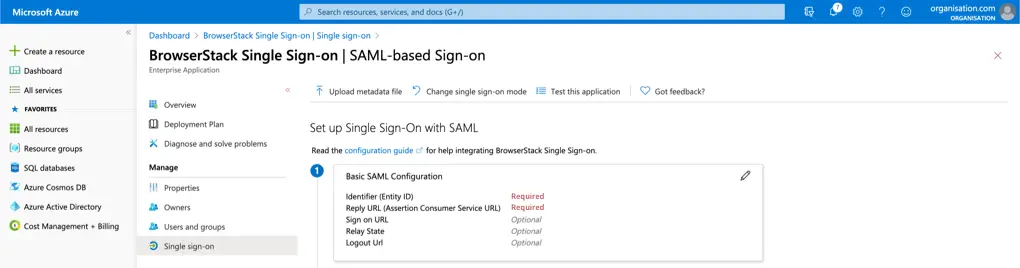
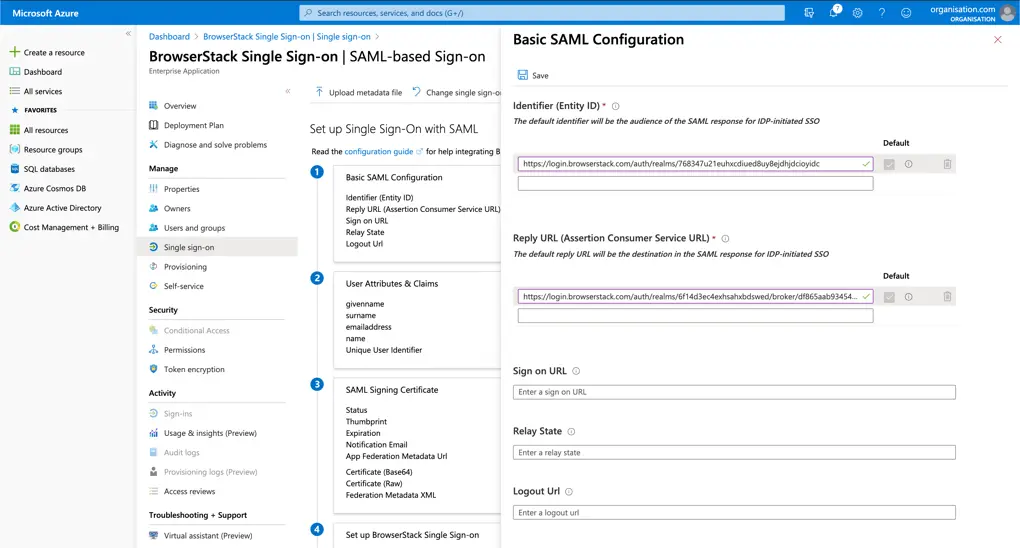
- Paste the values from BrowserStack’s SSO Configuration page, as below:
- Paste IDP initiated ACS URL under Reply URL (Assertion Consumer Service URL) and default check is set. Please note, this is for IdP Initiated SSO. You should leave this blank if you do not intend to set up IdP Initiated flow.
- Paste SP initiated ACS URL under Reply URL (Assertion Consumer Service URL) and default check is false.
- Paste Entity ID under Identifier (Entity ID).
-
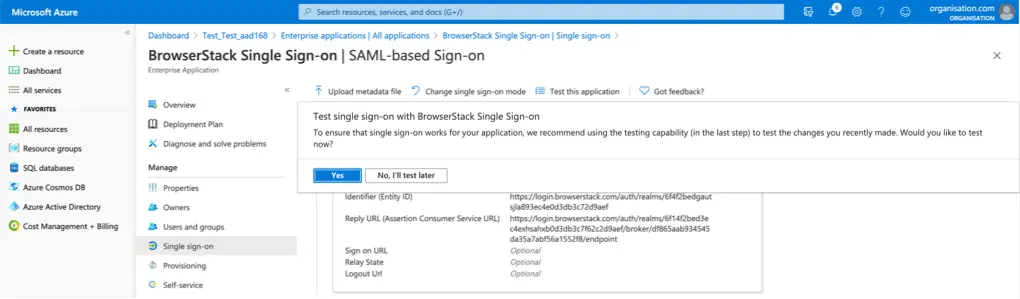
Save and Close.
-
When you get a prompt, click on No, I will test later.
-
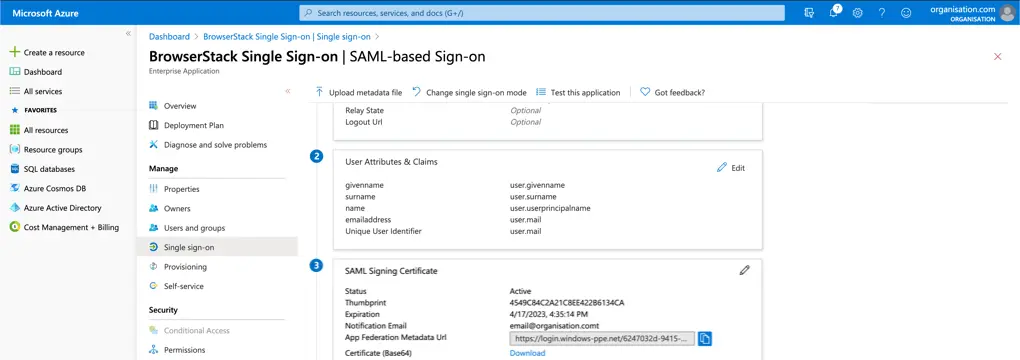
Next, edit User Attributes & Claims
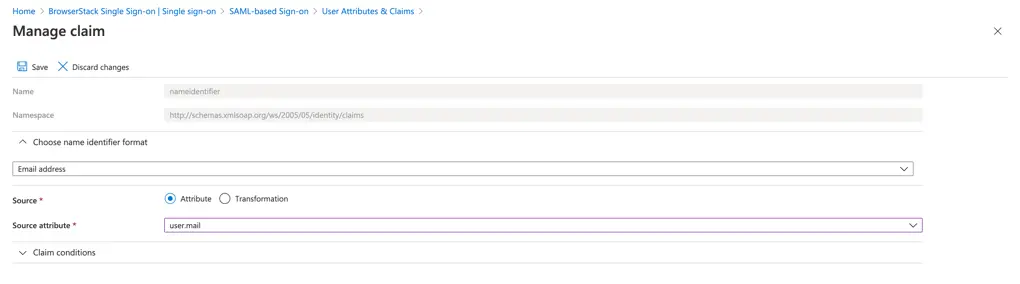
- Under Choose name identifier format
- Select Attribute
- Enter user.mail (or whatever is the attribute for email address)
- Click Save
- Copy the following from Set up BrowserStack Single Sign-on
- Login URL
- Logout URL
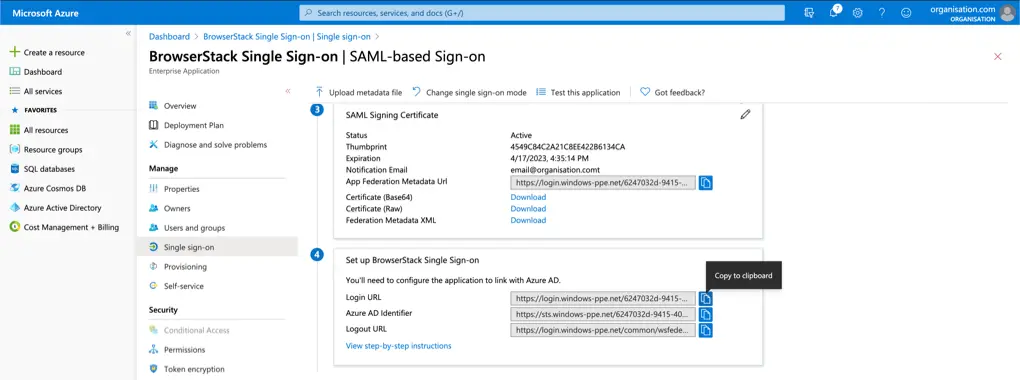
- Click on Download next to Federation Metadata XML, present in the SAML Signing Certificate.
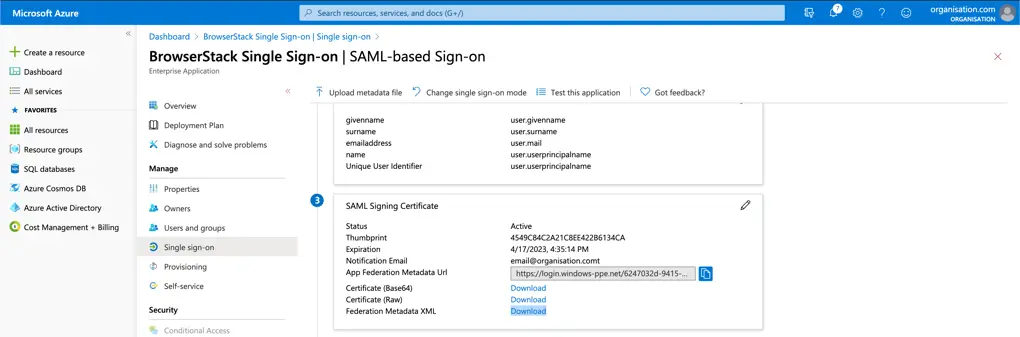
- Open the file and copy the following
-
Public Certificate
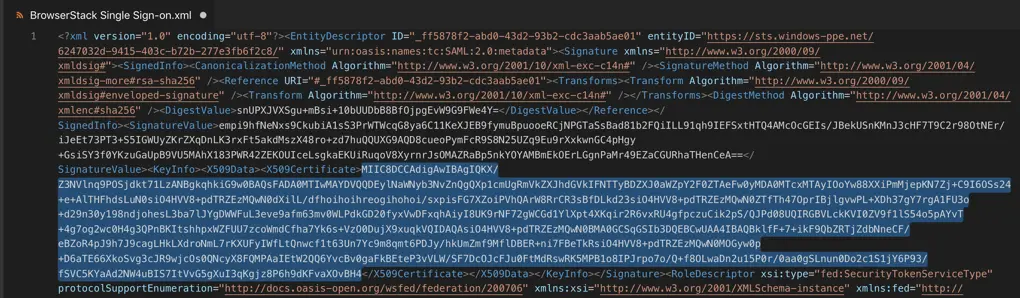
-
Navigate back to BrowserStack configuration page and paste the following details:
a. Login URL
b. Logout URL
c. Public Certificate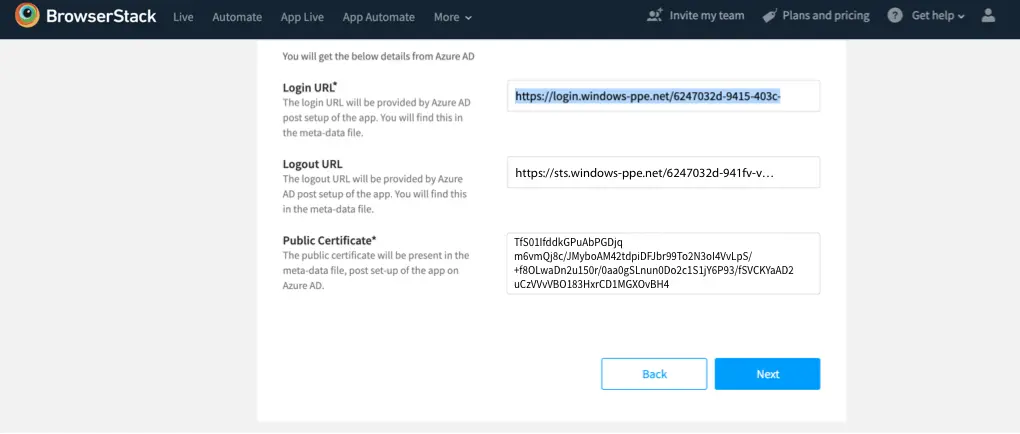
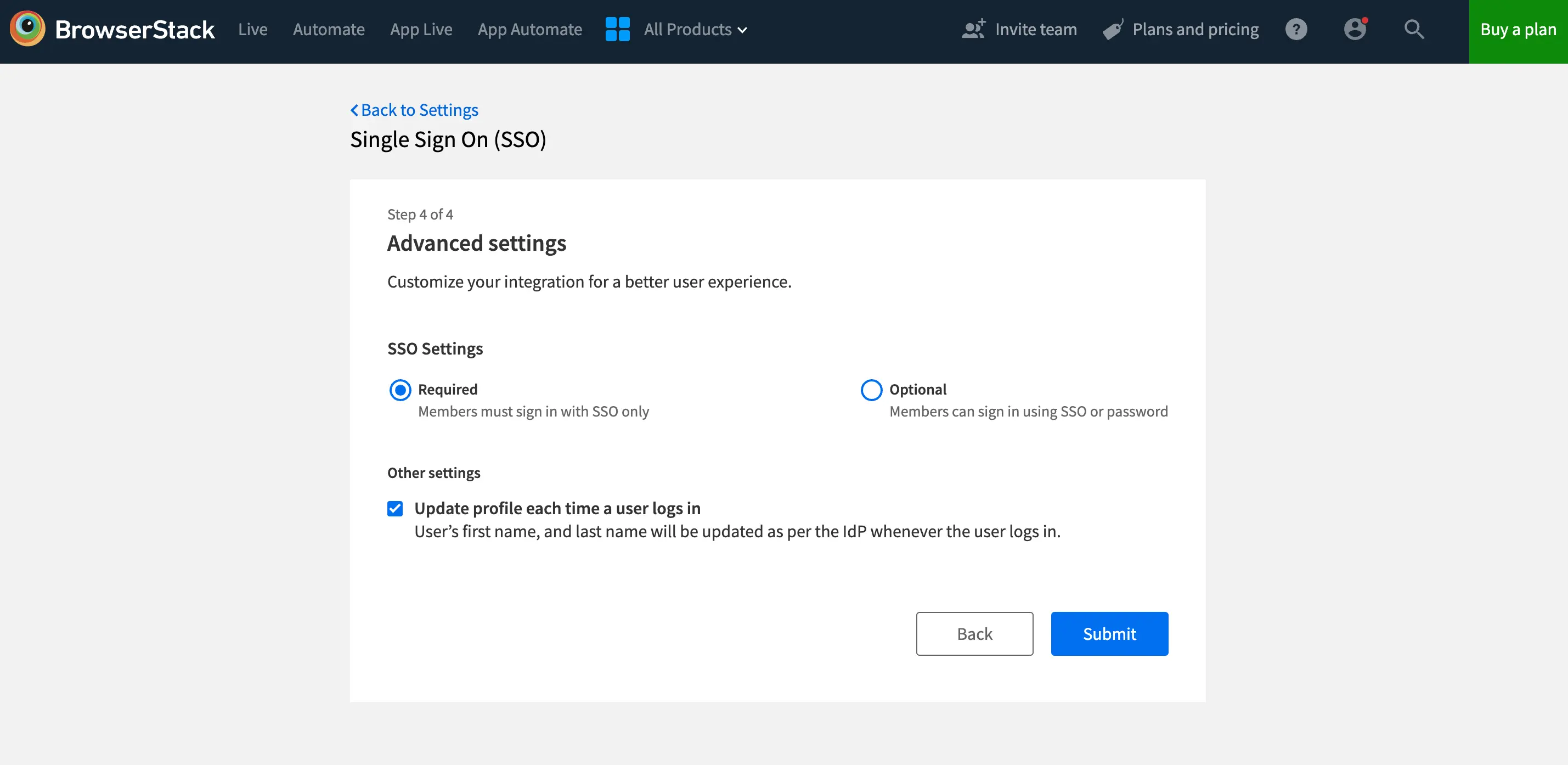
- Click Next to proceed to the Advanced options section. Here, you will be able to configure your SSO settings as either Required or Optional. This allows you to choose the level of SSO enforcement that suits your organization’s needs.
-
Required (default): Choose this option if you want to ensure that your team members must sign in to BrowserStack using SSO. Their BrowserStack credentials will no longer work. However, owners can still sign in using either of their SSO or BrowserStack credentials.
-
Optional: Opt for this setting if flexibility is your priority. With SSO configured as Optional, your team members can sign in using either their SSO or BrowserStack credentials. Additionally, you can choose to extend this flexibility only to some team members. Simply specify domains of members to exclude from Optional setting and all users from those domains will be required to login using SSO only.
-
- Click Submit to save your changes
Test and enable
-
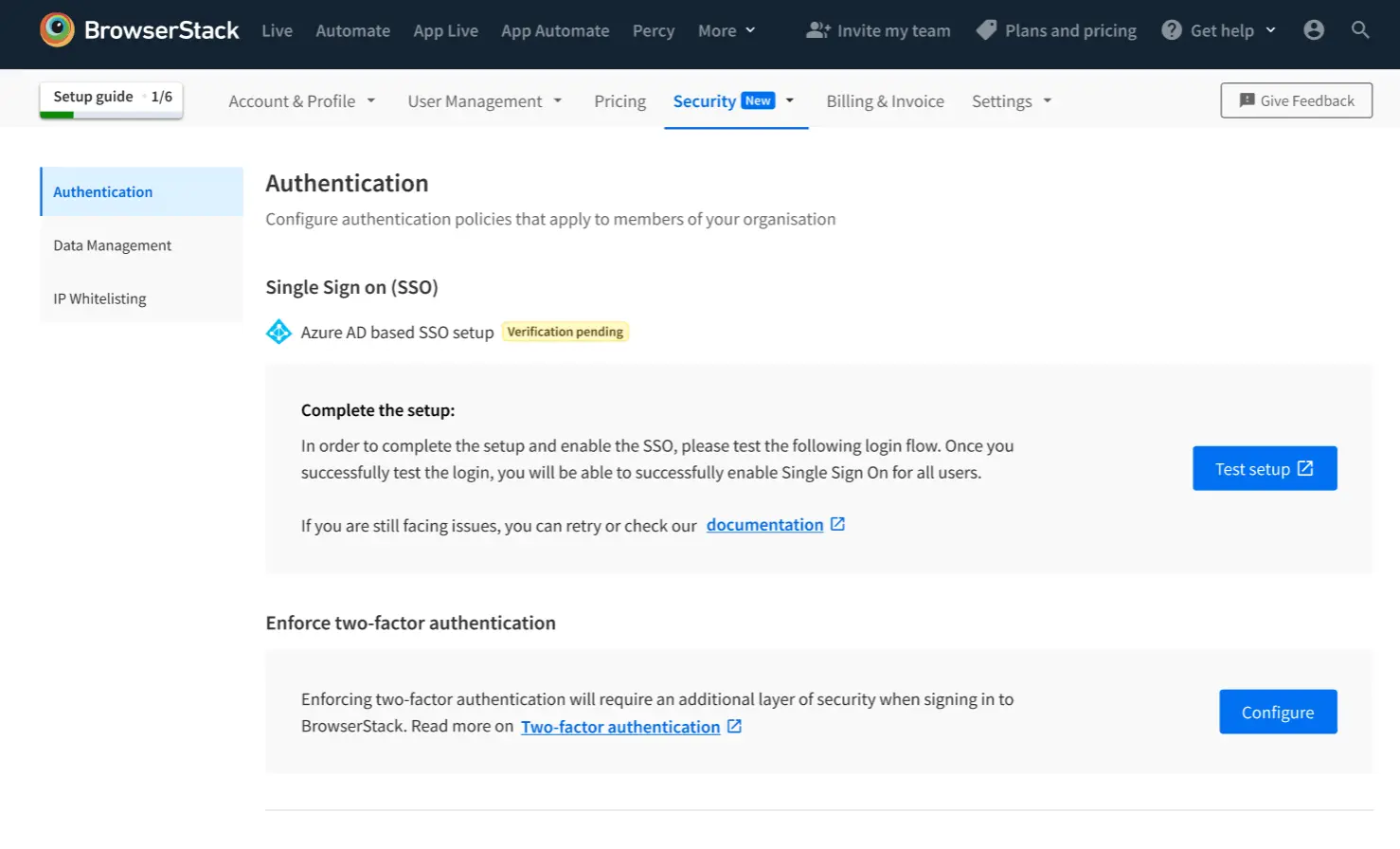
Test the integration via Test Setup.
-
You will be prompted towards Service Provider flow and your user will be authenticated via Azure AD. Test is successful upon completion of the SSO Authentication flow.
-
Upon successful test, you can enable the Single Sign-on feature for your Organization.
You have the option of sending out a mail to all the members on BrowserStack, to inform them about this change, and a link to the new login URL.
Click Enable to enable the feature.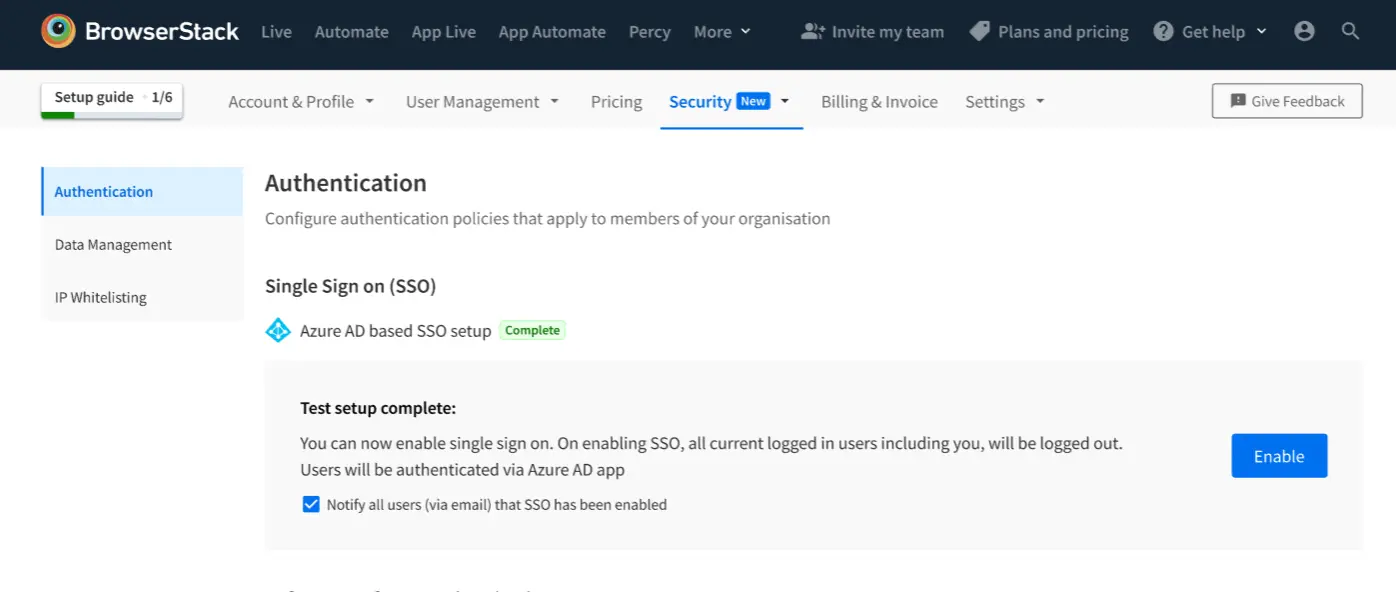
-
You will automatically be logged out of the BrowserStack, and redirected to log-in via SSO.
Troubleshooting
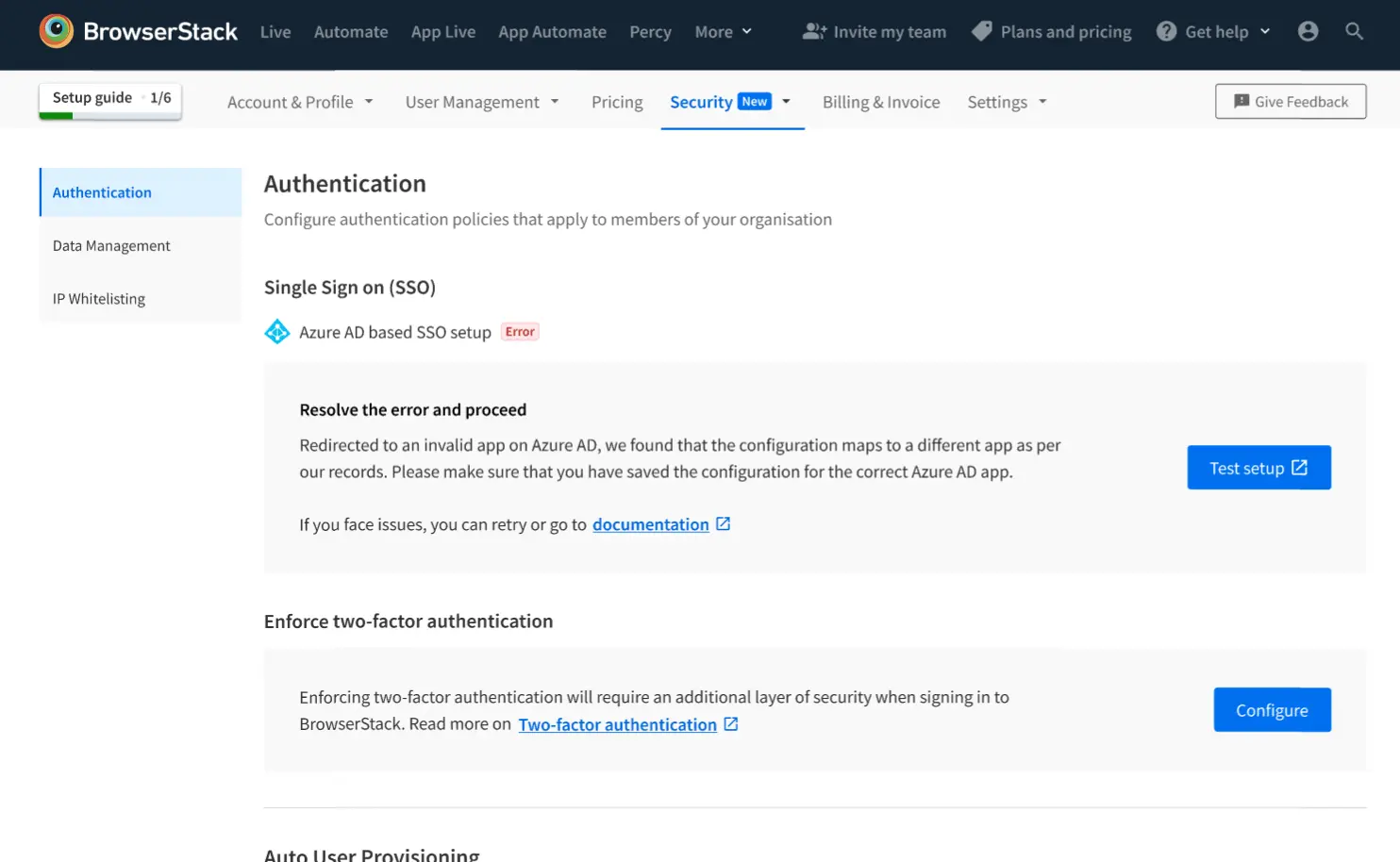
Error while testing (Type 1)
The user saved the configuration of the connection on the other application. Please make sure that the correct configuration is saved on the Azure AD app.
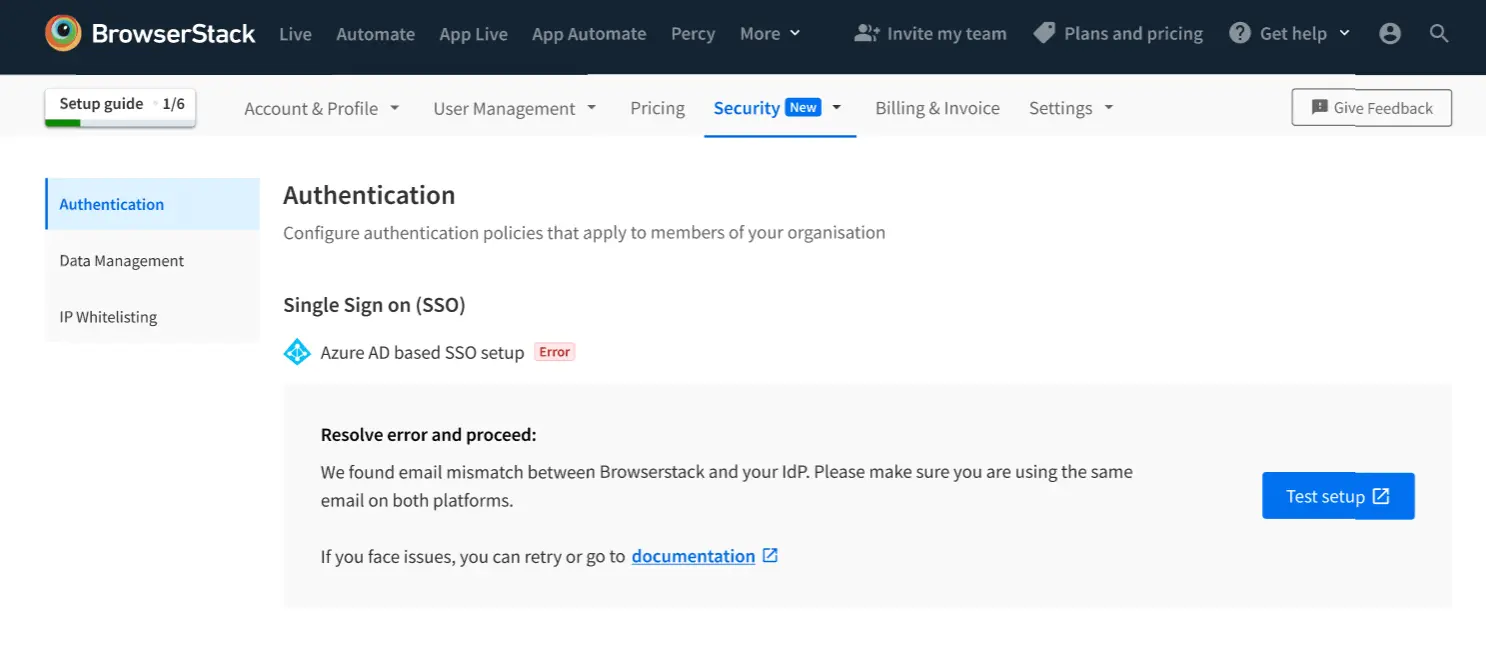
User mismatch
The user logged in on Azure AD and BrowserStack is different. Please make sure that you are using the same email to login on BrowserStack as well as the Azure AD.
Internal error
In case of this error, contact us.
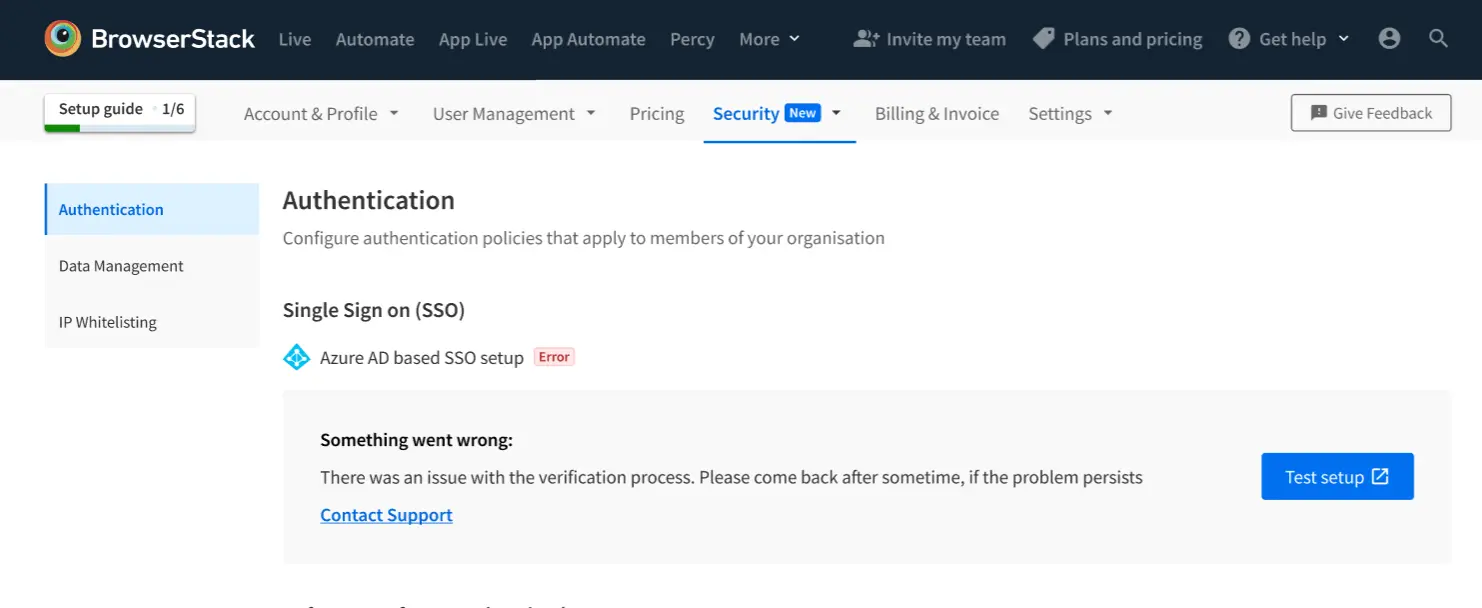
Misconfigured ACS URL
The ACS URL submitted in the configuration is incorrect.
We're sorry to hear that. Please share your feedback so we can do better
Contact our Support team for immediate help while we work on improving our docs.
We're continuously improving our docs. We'd love to know what you liked
We're sorry to hear that. Please share your feedback so we can do better
Contact our Support team for immediate help while we work on improving our docs.
We're continuously improving our docs. We'd love to know what you liked
Thank you for your valuable feedback!