The X-Forwarded-For header is widely used in web applications to track the original client IP address, especially when requests pass through proxies or load balancers.
Overview
What is X-Forwarded-For HTTP Header?
The X-Forwarded-For (XFF) HTTP header identifies the originating IP address of a client connecting to a web server through an HTTP proxy or load balancer. It helps servers recognize the actual source of requests rather than the intermediary device.
Why is X-Forwarded-For HTTP Header Important?
- Security monitoring: Helps detect suspicious traffic or potential attacks by identifying the true client IP.
- Accurate logging: Ensures server logs reflect the real client, aiding debugging and analytics.
- Rate limiting: Supports IP-based throttling or blocking even when requests pass through proxies.
- Geolocation tracking: Enables correct mapping of users’ locations for personalization and analytics.
X-Forwarded-For HTTP Header Use Cases
- Proxy and load balancer setups: Tracks original client IP when multiple intermediaries handle requests.
- Content personalization: Delivers tailored content based on client IP instead of proxy IP.
- Fraud detection: Identifies unusual request patterns from masked IPs for security measures.
- Access control: Enforces IP-based restrictions accurately behind reverse proxies.
Format of X-Forwarded-For
The header lists client IPs in a comma-separated format, with the originating IP first, followed by proxy IPs. For example:
X-Forwarded-For: client1, proxy1, proxy2
This article explains X-Forwarded-For functionality, use cases, testing methods, and best practices in web applications.
What Is the X-Forwarded-For Header?
The X-Forwarded-For (XFF) header is an HTTP header that carries the original client IP address when a request passes through one or more proxies or load balancers. Without XFF, a server only sees the IP of the last intermediary, not the client that initiated the request.
The header can include multiple IP addresses, listed in a comma-separated format, showing the chain of proxies the request traversed. It is added by proxies or load balancers and may not be present if intermediaries are not configured to include it. Servers that rely on XFF should handle it carefully, as untrusted values can be manipulated by clients.
Why Is X-Forwarded-For Crucial for Web Applications?
Web applications often operate behind proxies, load balancers, or CDN networks, which can obscure the client’s real IP address. The X-Forwarded-For header ensures that the original client IP is accessible, allowing web applications to make accurate decisions for security, analytics, and traffic management.
Here are some reasons why X-Forwarded-For header is important:
- Threat detection and mitigation: Identify malicious or automated requests by analyzing the original client IP. This allows web applications to block or flag suspicious traffic even when attackers route requests through multiple proxies.
- Precise logging and audit trails: Maintain detailed and reliable logs that reflect the actual source of requests. This is essential for troubleshooting, forensic analysis, and compliance requirements where accurate IP tracking is mandatory.
- Intelligent rate limiting and throttling: Implement IP-based throttling accurately by using the client’s real IP instead of the proxy’s. This prevents legitimate users from being blocked due to proxy-based IP aggregation.
- Accurate geolocation and personalization: Enable correct mapping of users to their geographical locations for personalized content delivery, targeted marketing, or regulatory compliance that depends on user location.
- Secure access controls and firewall rules: Apply IP-based access restrictions or allowlists with confidence, ensuring that only legitimate clients can reach sensitive endpoints, even when the request passes through multiple network layers.
X-Forwarded-For HTTP Header Use Cases
In complex web architectures, requests often pass through proxies, load balancers, or CDN networks, which can hide the original client IP. The X-Forwarded-For header allows applications to reliably identify the true client IP, enabling better security, monitoring, and traffic management.
Here are some common use cases for the X-Forwarded-For header:
- Maintain proxy and load balancer transparency: Track the client’s original IP across multiple intermediary devices, ensuring servers can distinguish between actual client requests and proxy traffic.
- Deliver personalized content: Serve location-specific content, language preferences, or region-based services accurately by using the client’s real IP.
- Detect fraud and automated bots: Identify suspicious request patterns hidden behind shared or masked IPs by analyzing the complete chain of IPs in the XFF header.
- Apply precise access control: Enforce IP-based allowlists, blocklists, or role-based restrictions reliably, even when traffic passes through multiple proxies.
- Ensure regulatory compliance: Maintain accurate records of client IPs for audits and compliance frameworks such as GDPR or PCI-DSS.
How X-Forwarded-For Works in Proxy and Load Balancer Environments
When a client sends a request directly to a web server, the server can easily identify the client’s IP address from the TCP connection. In real-world architectures, however, requests typically pass through intermediaries such as reverse proxies, load balancers, or CDNs.
These components forward the request to the server but replace the original source IP with their own, which prevents the server from knowing who actually initiated the request.
The X-Forwarded-For header solves this by preserving the chain of IP addresses as the request moves through different layers. Each intermediary that handles the request appends its own IP address to the existing list while retaining the original client IP at the beginning.
Step-by-step process of how X-Forwarded-For works:
- Client initiation: The client sends a request to a proxy or load balancer instead of directly to the web server. For example, the request originates from IP 203.0.113.45.
- Proxy handling: The proxy adds an X-Forwarded-For header with the client’s IP address. The header now appears as X-Forwarded-For: 203.0.113.45.
- Multiple intermediaries: If the request passes through several proxies, each proxy appends its own IP to the header. The chain might look like X-Forwarded-For: 203.0.113.45, 198.51.100.20, 192.0.2.10.
- Server reception: The final server receives the request and reads the first IP in the header (203.0.113.45) to identify the actual client that initiated the request.
This mechanism allows web servers to maintain end-to-end visibility of client origins even when operating behind complex network infrastructures. The first IP always represents the original client, while the subsequent IPs represent the intermediary proxies or gateways.
Key technical considerations:
- Trust boundaries: Servers should only trust X-Forwarded-For headers inserted by known proxies or load balancers to prevent spoofing.
- Order of IPs: The header is sequential, with the leftmost IP as the original client and subsequent entries as intermediaries.
- Proxy configuration: Some reverse proxies, such as NGINX or HAProxy, require explicit configuration to append and forward XFF headers properly.
Troubleshooting X-Forwarded-For Header Issues
Misconfigurations or incorrect assumptions about trust boundaries can lead to inaccurate or missing X-Forwarded-For data. When the header fails, it affects analytics, rate limiting, and security enforcement. Identifying and resolving these issues requires checking both network and application layers.
Here are some common causes and solutions for X-Forwarded-For header issues:
1. Header not appearing in requests
This usually occurs when the proxy or load balancer is not configured to append or forward the XFF header. Verify that the intermediary explicitly adds X-Forwarded-For in its configuration. For example, in NGINX, use:
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
2. Incorrect or missing client IPs
When the header shows only proxy IPs, ensure that the original client IP is being captured before the header is appended. This might require adjusting load balancer settings to pass the client’s connection details.
3. IP spoofing through client-injected headers
Some malicious clients add fake X-Forwarded-For values to bypass security filters. To prevent this, strip any incoming XFF headers at the network edge and reinsert a trusted version only from known proxies.
4. Duplicate or out-of-order IP addresses
Multiple intermediaries can sometimes re-add the header incorrectly. Review your proxy chain configuration to ensure only one trusted layer appends new IPs while others forward the header as-is.
5. Application-level parsing errors
Applications may misinterpret the IP list if they do not parse commas or whitespace correctly. Always validate and sanitize XFF header values in backend logic before logging or decision-making.
Best Practices for Implementing X-Forwarded-For
The effectiveness of the X-Forwarded-For header depends on consistent and secure implementation across all intermediaries. Adhering to these practices ensures reliability and prevents manipulation.
Here are some best practices for implementing the X-Forwarded-For header:
- Trust specific proxy layers: Configure servers to accept and trust XFF headers only from known load balancers or gateways. This prevents unverified sources from injecting spoofed IPs.
- Standardize proxy configuration: Ensure all proxies in the network use a consistent format for appending XFF values. Use environment-specific variables such as $proxy_add_x_forwarded_for in NGINX or ForwardedRequestHeader in IIS.
- Strip and reinsert headers at network edges: To maintain authenticity, remove any pre-existing XFF headers at the network boundary and generate a new one from the trusted edge proxy.
- Log both client and intermediary IPs: Capture the entire IP chain for better visibility, debugging, and compliance reporting.
- Validate IP formats in application code: Implement server-side validation to handle malformed or suspicious IP entries. Avoid using untrusted header values for security-critical logic without sanitization.
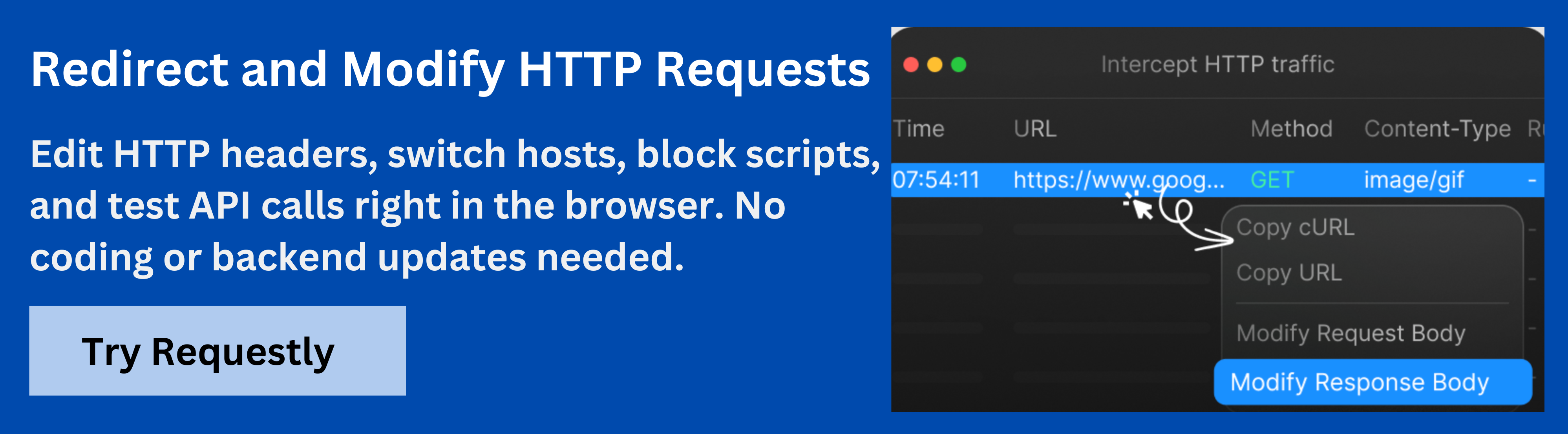
How Requestly Assists in Testing X-Forwarded-For Headers
Requestly by BrowserStack is a browser-based tool and desktop app designed for developers and testers to modify, inspect, and simulate network requests in real time. It allows users to intercept HTTP traffic, manipulate headers, and test how applications behave under different request conditions without needing to modify server code.
When testing the X-Forwarded-For header, Requestly helps simulate various client IPs and proxy chains, making it easier to verify how a server interprets and logs incoming requests. This ensures that XFF-based logic for rate limiting, access control, or analytics functions correctly.
Here are the key features of Requestly that simplify X-Forwarded-For testing:
- Add custom X-Forwarded-For headers: Inject different client IPs into outgoing requests to test how the application processes multiple IP scenarios.
- Rewrite existing header values: Modify or replace existing XFF headers in intercepted requests to validate proxy handling and trust boundary configurations.
- Simulate multi-proxy chains: Append multiple IPs in sequence to emulate layered proxy environments and verify how the server interprets the IP order.
- Debug header behavior in real time: Inspect and confirm that the server logs, analytics tools, or security filters read the correct originating IPs during testing.
- Automate test scenarios: Create reusable header modification rules to simulate consistent client IPs across multiple requests during automated or regression testing.
Conclusion
The X-Forwarded-For header is crucial for identifying the true client IP in environments with proxies or load balancers. It ensures accurate logging, security enforcement, rate limiting, and geolocation services. Missing or misconfigured headers can cause incorrect analytics, failed access controls, and vulnerability to spoofed requests.
Requestly allows testers to inject and modify X-Forwarded-For headers in real time. It enables simulation of multi-proxy chains, verification of access rules, and reproduction of client scenarios without changing server configurations. Using Requestly ensures that applications correctly interpret forwarded IPs, improving security, monitoring, and reliability in distributed web systems.