The X-Forwarded-Host header is a critical component in modern web applications, commonly used in reverse proxy setups. However, if not properly secured, it can expose web infrastructure to various security risks, such as header injection attacks or misrouting of traffic.
Overview
What is the X-Forwarded-Host Header?
The X-Forwarded-Host header is used in HTTP requests to identify the original host requested by the client in cases where the request passes through a proxy or load balancer.
Security Risks Associated with X-Forwarded-Host:
- Header Injection Attacks: Malicious users can manipulate the header to inject unwanted values, leading to potential redirects or security breaches.
- Domain Spoofing: Attackers can alter the host header to impersonate a trusted domain, bypassing security filters.
- Open Redirect Vulnerabilities: Misconfigured applications may inadvertently redirect users to malicious sites if the X-Forwarded-Host header is trusted without validation.
- Session Fixation: The header can be used to trick applications into using incorrect session data by manipulating the host values.
Best Practices for Handling X-Forwarded-Host:
- Validate Host Header: Always validate the X-Forwarded-Host value against a trusted list of domains to prevent spoofing.
- Disable Trust in Unverified Proxies: Only accept the X-Forwarded-Host header from trusted proxies and not from client-side requests.
- Sanitize Input: Ensure that any input from X-Forwarded-Host is sanitized before being used in routing or redirects.
- Use Secure HTTPS Headers: Configure strict security headers such as Strict-Transport-Security (HSTS) to minimize the impact of any header manipulation.
- Monitor for Suspicious Activity: Implement monitoring to detect unusual or unauthorized modifications to the X-Forwarded-Host header.
This article explores the importance of securing the X-Forwarded-Host header in web applications, highlighting its security risks and best practices for safe handling.
What is the X-Forwarded-Host Header?
The X-Forwarded-Host (X-FH) header is an HTTP header commonly used in web applications where requests pass through a reverse proxy, load balancer, or other intermediary servers. It is used to indicate the original host requested by the client before the request reached the proxy or load balancer.
This header allows the backend server to identify the domain or subdomain that the client initially intended to reach, even though the request may have been routed or modified by proxies in between.
The X-Forwarded-Host header is particularly important in scenarios where multiple services or domains are handled by the same backend infrastructure, or when the application is behind a reverse proxy that terminates the client’s connection.
Without this header, the backend server would only know about the proxy or load balancer’s hostname, potentially leading to incorrect routing or misidentification of the client’s original request.
How X-Forwarded-Host Works in Web Infrastructure?
The X-Forwarded-Host header plays a critical role in web infrastructure, especially in environments that involve reverse proxies, load balancers, or multiple application services. It enables the backend server to understand the original host requested by the client, even if the request passes through intermediary servers. Here’s how it works:
- Client to Proxy: When a client makes an HTTP request, it often interacts with a reverse proxy or load balancer, which forwards the request to a backend server. The client’s initial request may contain the “Host” header indicating the domain they intend to reach, but this is replaced or modified when the request passes through the proxy. To preserve the original domain requested by the client, the proxy includes the X-Forwarded-Host header.
- Proxy to Backend: The reverse proxy or load balancer forwards the request to the backend server, adding the X-Forwarded-Host header. This header contains the host name from the original client request, allowing the backend server to know which domain was intended, even though the request was routed through the proxy.
- Backend Processing: The backend server reads the X-Forwarded-Host header to properly process the request. This is essential when the backend hosts multiple domains or services. The server uses this information to handle routing, authentication, and authorization, ensuring the client is directed to the correct service.
- Routing and Redirection: The X-Forwarded-Host header also helps with managing redirects. If the backend server needs to redirect a client to another domain or subdomain, it can use the information in the header to ensure that the redirection is consistent with the original client request, avoiding potential issues such as domain misrouting or trust problems.
- Multiple Layers of Infrastructure: In a complex web application with multiple proxies or load balancers, the X-Forwarded-Host header helps maintain the correct routing context throughout the entire request lifecycle. The header ensures that each layer in the network stack has access to the necessary information about the original client request, which is vital for security, performance, and correct service handling.
Security Risks Associated with X-Forwarded-Host
The X-Forwarded-Host header is a valuable tool for routing traffic in web applications, but if not managed carefully, it can expose the system to several significant security risks. Understanding these risks is crucial for preventing vulnerabilities in web infrastructure.
Header Injection Attacks
One of the primary security risks comes from malicious users injecting harmful data into the X-Forwarded-Host header. Attackers can modify the header to include unauthorized values, which could lead to a range of security issues such as redirecting users to malicious websites, performing cross-site scripting (XSS) attacks, or bypassing security controls. This is particularly dangerous if the header is trusted without proper validation by the backend server.
Domain Spoofing
If the X-Forwarded-Host header is not adequately validated, attackers can modify it to impersonate a legitimate, trusted domain. This technique, known as domain spoofing, can deceive the web server into trusting an incorrect host, potentially granting unauthorized access to sensitive parts of an application. In some cases, this could lead to privilege escalation or unauthorized access to user data.
Open Redirect Vulnerabilities
An application that blindly trusts the X-Forwarded-Host header might inadvertently create an open redirect vulnerability. This happens when the server, based on a manipulated host header, redirects users to malicious or untrusted external sites. Attackers can exploit this to trick users into visiting phishing sites, where they could fall victim to scams or credential theft.
Session Fixation
The X-Forwarded-Host header could be exploited in session fixation attacks, where attackers modify the host value to force the backend server to use an existing session ID or hijack an active session. If the application doesn’t correctly validate the X-Forwarded-Host header, attackers could gain unauthorized access to a user’s session, potentially compromising the user’s account or sensitive data.
Cross-Site Scripting (XSS)
If the value of the X-Forwarded-Host header is not sanitized or validated, attackers can inject malicious scripts into the header. This could result in cross-site scripting (XSS) vulnerabilities, allowing attackers to execute arbitrary scripts in a user’s browser. These scripts could steal cookies, session tokens, or perform actions on behalf of the user without their knowledge.
Due to these security risks, it is essential to handle the X-Forwarded-Host header carefully, applying appropriate validation and security controls to mitigate the potential for exploitation.
Best Practices for Handling X-Forwarded-Host
To properly secure the X-Forwarded-Host header, it’s important to follow best practices that prevent malicious manipulation and ensure the header is handled safely within your web infrastructure.
- Validate Host Header: One of the most effective ways to secure the X-Forwarded-Host header is to validate its value against a list of trusted domains or subdomains. This ensures that only legitimate, pre-approved values are processed. By doing so, you can prevent domain spoofing or hijacking attempts where attackers may try to forge the host header to impersonate a trusted domain.
- Disable Trust in Unverified Proxies: Not all proxies or load balancers should be trusted to send the X-Forwarded-Host header. It’s crucial to only accept the header from verified and trusted proxies that are part of your infrastructure. Accepting the header from untrusted or client-controlled proxies could open up the possibility of an attacker modifying the header to their advantage.
- Sanitize Input: Even if the X-Forwarded-Host header is coming from a trusted source, it is important to sanitize the value before using it in routing decisions or redirects. This includes stripping out any potential malicious characters, ensuring that the value is appropriately encoded, and filtering out any content that could trigger security vulnerabilities such as cross-site scripting (XSS).
- Use Secure HTTPS Headers: Enforcing secure communication is vital in preventing man-in-the-middle (MITM) attacks or header tampering. Configuring your application to use security headers like Strict-Transport-Security (HSTS) ensures that all communication is forced over HTTPS, protecting the integrity of the X-Forwarded-Host header and preventing it from being intercepted or modified during transmission.
- Monitor for Suspicious Activity: Implementing continuous monitoring to track any anomalies or suspicious modifications to the X-Forwarded-Host header can help detect and mitigate potential attacks before they cause damage. Look out for unexpected changes in header values or unusual patterns in the requests that could indicate exploitation attempts.
By adhering to these best practices, you can significantly reduce the security risks associated with handling the X-Forwarded-Host header and ensure that your web infrastructure remains secure.
How to Test and Validate X-Forwarded-Host Configurations
Testing and validating the configuration of the X-Forwarded-Host header is essential for ensuring that your web application handles requests securely and correctly, especially when traffic passes through reverse proxies or load balancers. Below are steps to effectively test and validate X-Forwarded-Host configurations:
1. Check for Header Presence and Correctness: Ensure that the X-Forwarded-Host header is being correctly forwarded by the proxy or load balancer. Test if the header is present in requests sent to the backend server.
2. Validate the Host Value: Verify that the backend server is properly reading and using the X-Forwarded-Host value to make routing decisions. Perform tests with different domains or subdomains to ensure that the backend correctly processes requests based on the X-Forwarded-Host header.
3. Check for Header Injection Vulnerabilities: Test for potential header injection vulnerabilities by attempting to manipulate the X-Forwarded-Host header. Try adding unexpected characters or malicious values to the header (e.g., injecting newlines, special characters, or URLs) and observe how the server reacts.
4. Test for Domain Spoofing: Test whether the backend server improperly trusts the X-Forwarded-Host header by setting it to a different domain or subdomain and checking if the server processes the request as if it came from the legitimate host. Confirm that only a predefined set of trusted domains or subdomains are allowed, preventing unauthorized or spoofed host values from being accepted.
5. Verify Handling of Redirects: Ensure that any redirects initiated by the backend server use the correct host from the X-Forwarded-Host header. Test different scenarios where the application would issue redirects and check whether the URLs in the redirects are consistent with the original client request.
6. Monitor Logs for Anomalies: Review the server logs for any unusual patterns or errors related to the X-Forwarded-Host header. Look for instances where the header is missing, misconfigured, or manipulated in unexpected ways. Ensure that your application’s logging mechanisms capture relevant details to detect potential issues with the header.
7. Simulate Real-World Traffic: Set up load testing or simulated traffic to replicate real-world conditions where requests pass through multiple proxies or load balancers. This helps ensure that the X-Forwarded-Host header is consistently and correctly handled across different layers of your infrastructure.
8. Automated Security Testing: Use automated security testing frameworks to regularly test for security vulnerabilities related to the X-Forwarded-Host header. This includes running penetration tests to identify issues with trust, validation, and sanitization of the header.
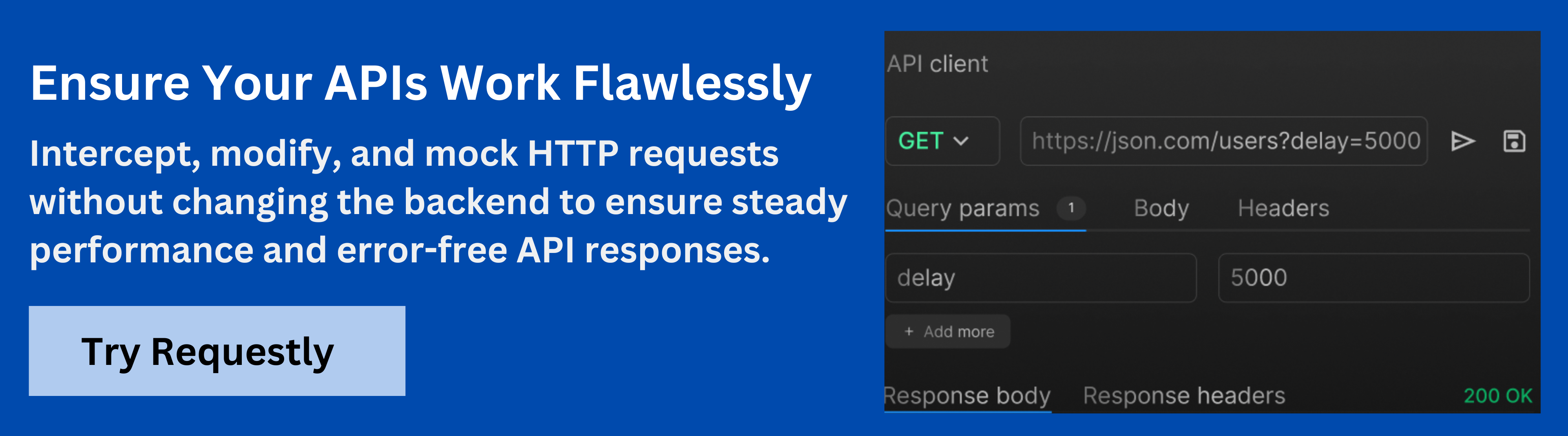
Streamline Security Testing with Requestly
Requestly by BrowesereStack is a versatile tool that enhances security testing by enabling real-time modification, interception, and inspection of HTTP requests and responses. When working with headers like X-Forwarded-Host, Requestly simplifies testing for vulnerabilities such as header injection and domain spoofing. Here’s how it can streamline your security testing:
- Intercept and Modify Requests: Easily modify the X-Forwarded-Host header to simulate various attack scenarios, such as header manipulation or domain spoofing, helping you test how your backend handles altered values.
- Mock Responses for Testing: Simulate different scenarios by mocking responses and testing how your server reacts to various X-Forwarded-Host configurations, including invalid or unexpected header values.
- Real-time Inspection and Debugging: Inspect incoming and outgoing HTTP headers in real time, making it easy to verify that the X-Forwarded-Host header is processed correctly and monitor the impact of any changes made.
- Automate and Reproduce Security Scenarios: Automate the testing process by creating custom rules and scripts to reproduce common security risks, enabling faster detection and mitigation of vulnerabilities.
- Enhanced Debugging for Misconfigurations: Quickly spot misconfigurations related to the X-Forwarded-Host header, making it easier to fix issues like improper routing, incorrect redirects, or domain spoofing.
By integrating Requestly into your security workflow, you can streamline the process of validating X-Forwarded-Host configurations, ensuring a more secure and resilient web application.
Conclusion
Securing the X-Forwarded-Host header is crucial in maintaining the integrity of web applications, especially in environments that rely on reverse proxies or load balancers. Improper handling of this header can expose applications to various security risks, including domain spoofing, header injection, and open redirects. By following best practices such as validating host values, limiting trust to verified proxies, and using security headers like HSTS, you can mitigate these risks effectively.
Additionally, leveraging tools like Requestly simplifies the testing and validation process, enabling you to simulate real-world attack scenarios and ensure that your configurations are secure. By regularly testing and monitoring X-Forwarded-Host handling, you can safeguard your web infrastructure against potential vulnerabilities and maintain a secure, reliable user experience.