Web applications often interact with APIs, resources, and services hosted on different domains. This cross-domain communication, however, is restricted by browsers for security reasons. Developers frequently encounter issues like the “CORS policy error” or messages such as “No “Access-Control-Allow-Origin‘ header present.” These occur due to the Access-Control-Allow-Origin header-a critical component of Cross-Origin Resource Sharing (CORS).
According to Chrome DevTools data, CORS-related errors are among the top five most common browser console warnings during web development. Understanding this header and configuring it correctly is essential for both security and functionality.
Overview
- The browser sends an Origin header to indicate the request’s source.
- Simple requests (GET, POST, HEAD) are sent directly; the browser checks for a valid Access-Control-Allow-Origin in the response.
- Preflighted requests (like PUT, DELETE, or with custom headers) use an OPTIONS request first; the server must return valid CORS headers before the main request proceeds.
- If the origin and headers match, the browser grants access; otherwise, it blocks the response.
This article explains about what Access-Control-Allow-Origin is and its significance.
Understanding the Same-Origin Policy and CORS
The Same-Origin Policy (SOP) is a security mechanism enforced by browsers to prevent scripts from one origin (combination of scheme, host, and port) from accessing resources on another origin. For instance, a web page served from https://example.com cannot fetch data from https://api.example.org unless explicitly allowed.
While this policy protects users from malicious sites, it also restricts legitimate cross-domain API requests. This is where CORS (Cross-Origin Resource Sharing) comes into play.
CORS defines a set of HTTP headers that determine whether a browser should allow a web page to access resources from a different origin. The browser acts as the enforcer, checking the server’s response headers before making the resource accessible to the client script.
Key headers involved in CORS include:
- Access-Control-Allow-Origin
- Access-Control-Allow-Methods
- Access-Control-Allow-Headers
- Access-Control-Allow-Credentials
Among these, Access-Control-Allow-Origin is the fundamental directive that explicitly grants or denies permission for cross-origin access.
What Is the Access-Control-Allow-Origin Header?
The Access-Control-Allow-Origin header is a response header that indicates whether a resource can be accessed by web pages from a different origin.
Syntax:
Access-Control-Allow-Origin: | *
Allowed values:
- * – Permits access from any origin. This is suitable for public APIs but unsafe for requests involving credentials.
- Specific origin (e.g., https://example.com) – Grants access only to the listed origin.
- null – Used in sandboxed environments such as file URLs or data URLs.
If a server omits this header, browsers automatically block cross-origin requests, resulting in a CORS error.
When combined with other headers like Access-Control-Allow-Credentials: true, developers must avoid using the wildcard (*) and instead specify explicit origins.
How Access-Control-Allow-Origin Works in CORS
When a browser sends a request to a different origin, it includes an Origin header in the request to indicate where the request originated. The server examines this header and determines whether to allow the request.
There are two main types of CORS requests:
1. Simple Requests: These are requests that use methods like GET, POST, or HEAD and contain only safe headers. The browser sends the request directly and checks the server’s response for Access-Control-Allow-Origin.
Example:
Origin: https://client.example.com
Server response:
Access-Control-Allow-Origin: https://client.example.com
If the origin matches, the browser allows access to the response data.
2. Preflighted Requests
For non-simple requests (e.g., those using PUT, DELETE, or custom headers), the browser first sends an OPTIONS request-known as a preflight request. This ensures that the server supports the intended method and headers.
Example preflight sequence:
OPTIONS /data HTTP/1.1 Origin: https://client.example.com
Access-Control-Request-Method: PUT
Access-Control-Request-Headers: Content-Type
Server response:
Access-Control-Allow-Origin: https://client.example.com Access-Control-Allow-Methods: PUT, DELETE
Access-Control-Allow-Headers: Content-Type
Access-Control-Max-Age: 86400
Only after receiving a valid response does the browser proceed with the actual request.
Common Use Cases and Security Risks of Access-Control-Allow-Origin
Here are some common use cases and security risks of access-control-allow-origin:
Use Cases:
- Public APIs: Services like weather APIs or currency converters often use Access-Control-Allow-Origin: * since the data is public and doesn’t require authentication.
- Private or Internal APIs: For restricted systems, a dynamic origin configuration allows only trusted domains, such as an admin dashboard or partner application.
- Microservices and SPAs: Single Page Applications often communicate with multiple microservices. Proper CORS configuration ensures seamless integration without compromising security.
Security Risks:
- Wildcard with Credentials: Allowing * while sending cookies or authorization headers exposes sensitive data.
- Improper Dynamic Origin Handling: Reflecting the Origin header without validation creates a vulnerability for CORS misconfiguration attacks.
- Lack of Vary Header: When using dynamic origins, not setting Vary: Origin can lead to cache poisoning in CDN layers.
Read More:How to test redirect with Cypress
How to Configure Access-Control-Allow-Origin in Different Environments
Configuring the header depends on the server or framework being used.
1. Node.js (Express Example):
const express = require(‘express’);const app = express();
app.use((req, res, next) => {
res.header(‘Access-Control-Allow-Origin’, ‘https://example.com’);
res.header(‘Access-Control-Allow-Methods’, ‘GET, POST, PUT, DELETE’);
res.header(‘Access-Control-Allow-Headers’, ‘Content-Type’);
next();
});
2. Spring Boot (Java):
@CrossOrigin(origins = “https://example.com”)@RestController
public class ApiController {
@GetMapping(“/data”)
public String getData() {
return “Hello from server!”;
}
}
3. Apache Configuration:
Header set Access-Control-Allow-Origin “https://example.com”
Header set Access-Control-Allow-Methods “GET, POST, OPTIONS”
4. Nginx Configuration:
location /api/ { add_header ‘Access-Control-Allow-Origin’ ‘https://example.com’;
add_header ‘Access-Control-Allow-Methods’ ‘GET, POST, OPTIONS’;
}Each approach must align with the authentication model and caching behavior of the application.
Read More: What Is API Automation Testing?
Debugging Access-Control-Allow-Origin Errors
CORS errors can be subtle and frustrating. Common issues include missing headers, mismatched origins, or invalid configurations.
Frequent errors include:
- No “Access-Control-Allow-Origin’ Header Present: Indicates the server did not send the required header.
- Credential Error: Occurs when credentials are sent but the origin is set to *.
- Preflight Fails: If the server does not correctly respond to the OPTIONS request.
Debugging tips: - Use browser developer tools (Network tab) to inspect headers.
- Verify both request and response headers.
- Ensure server-side frameworks don’t override or strip CORS headers.
Testing and Modifying Access-Control-Allow-Origin with HTTP Interceptor Tools
Why Intercepting HTTP Headers Aids CORS Debugging
During development, developers may not have control over backend headers. HTTP interceptors make it possible to inspect, modify, or inject response headers dynamically without altering server code. This helps reproduce CORS scenarios and test fixes rapidly.
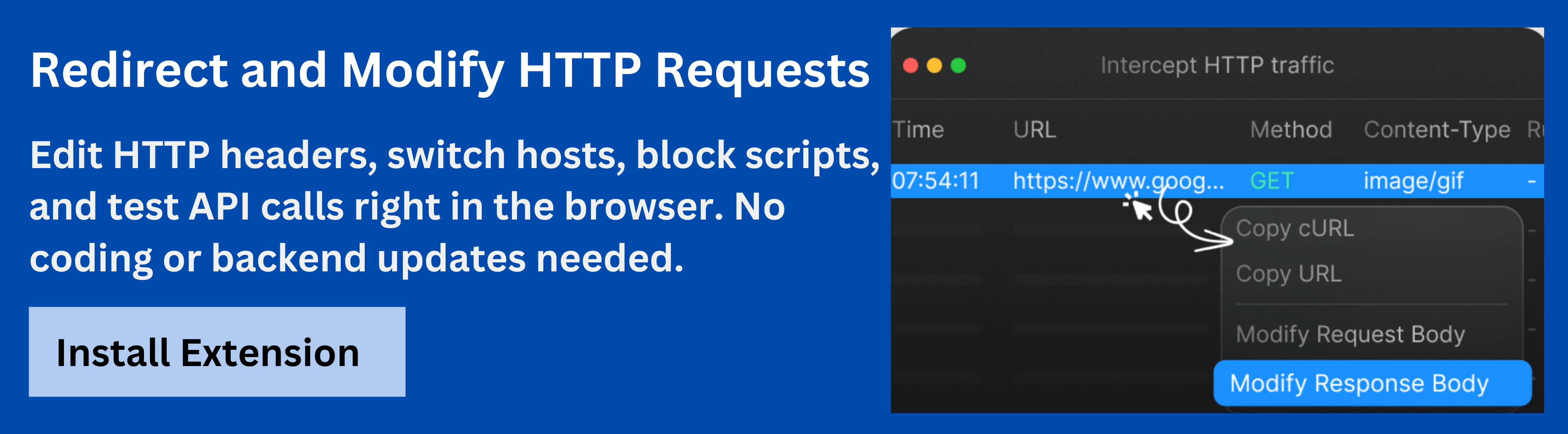
Using Requestly HTTP Interceptor to Simulate or Modify Access-Control-Allow-Origin Rules
The Requestly HTTP Interceptor provides an intuitive interface for capturing, modifying, and testing HTTP requests and responses directly from the browser. Developers can use it to:
- Add or modify Access-Control-Allow-Origin headers to test client behavior.
- Simulate responses from different origins to validate security restrictions.
- Bypass or troubleshoot CORS errors without redeploying server code.
For example, you can create a rule in Requestly to automatically add:
Access-Control-Allow-Origin: https://testclient.local
This allows developers to validate whether the frontend logic handles authorized domains correctly.
Best Practices for Implementing Access-Control-Allow-Origin
To ensure security and maintain compatibility:
- Avoid wildcard origins for endpoints that handle credentials or sensitive data.
- Include Vary: Origin when dynamically setting origins.
- Whitelist only trusted domains and keep the list updated.
- Ensure consistent headers across distributed services.
- Monitor for misconfigurations using HTTP debugging tools like Requestly HTTP Interceptorand automated tests.
Summary
The Access-Control-Allow-Origin header is central to enabling controlled cross-origin resource sharing. While it simplifies data access across domains, incorrect implementation can create security loopholes.
Understanding the browser’s role in enforcing CORS, validating configurations with tools like Requestly HTTP Interceptor ensures secure, efficient, and reliable web applications. Properly applied, this header strikes the perfect balance between openness and protection in modern web architecture.