Secure cookies are a critical part of web security, ensuring that sensitive data like session tokens and user preferences are transmitted securely over HTTPS.
Overview
What it Does
- The “Secure” flag ensures cookies are sent only over HTTPS, encrypting the communication.
- It prevents interception by ensuring cookies are only transmitted over secure connections.
- Secure cookies stop attackers from intercepting or modifying cookies during transmission.
How it Works
- Setting the Attribute: The “Secure” flag is added to a cookie by the server in the Set-Cookie header.
- Browser Behavior: Browsers will only send cookies marked as “Secure” over HTTPS, ensuring the cookie’s protection.
This article explores the importance of secure cookies, common issues developers face, and best practices for implementing them to enhance user privacy and prevent security vulnerabilities.
What are Secure Cookies?
Secure cookies are cookies that are marked with the Secure flag, ensuring they are only sent over HTTPS connections. This attribute tells the browser to transmit the cookie only when the communication is encrypted, reducing the risk of the cookie being intercepted during transmission.
Secure cookies are typically used to store sensitive information, such as session tokens or user authentication details, and are a key part of web security practices.
By enforcing the Secure flag, cookies are protected from being exposed on unencrypted (HTTP) connections, minimizing the risk of man-in-the-middle attacks.
Why Secure Cookies are Important for Web Security
Secure cookies play a critical role in protecting user data and maintaining the security of web applications. Here’s why they matter:
- Prevents Cookie Theft: Without the Secure flag, cookies can be intercepted by attackers on unsecured connections, especially in public or untrusted networks. Secure cookies ensure data is encrypted, making it harder for attackers to steal sensitive information.
- Reduces Session Hijacking: By ensuring that session cookies are only sent over secure channels, the Secure flag helps prevent session hijacking attacks, where attackers steal session cookies to impersonate a legitimate user.
- Maintains Data Integrity: When cookies are sent over HTTPS, the integrity of the data is maintained, ensuring that cookies cannot be tampered with in transit.
- Regulatory Compliance: Using secure cookies is a fundamental aspect of web security standards and compliance regulations like GDPR and PCI DSS, which require the use of secure transmission for sensitive data.
Also Read: Maximizing Web Security with Cypress
How to Set the Secure Flag in Cookies
The Secure flag is set by including it in the Set-Cookie header when the server sends a cookie to the browser. This instructs the browser to only send the cookie back to the server over an HTTPS connection.
Here’s how to set the Secure flag in the Set-Cookie header:
Set-Cookie: sessionId=abc123; Secure; HttpOnly; SameSite=Lax
- Secure: Ensures the cookie is only sent over HTTPS.
- HttpOnly: Prevents JavaScript from accessing the cookie, adding extra protection against XSS attacks.
- SameSite: Controls when cookies are sent with cross-site requests (e.g., Strict, Lax, None).
Important: The Secure flag can only be used with HTTPS connections. If a cookie is set with the Secure flag on a non-HTTPS page, the browser will not send the cookie.
Secure Cookies and HTTPS: The Role of the Secure Flag
The Secure flag works in tandem with HTTPS (HyperText Transfer Protocol Secure) to protect cookies during transmission.
- Role of HTTPS: HTTPS encrypts the communication between the client and server, ensuring that data sent (including cookies) cannot be easily intercepted by malicious actors. However, simply using HTTPS is not enough. Cookies must also be marked as Secure to ensure they are sent exclusively over encrypted connections.
- Ensuring Safe Transmission: When a cookie is marked as Secure, the browser only transmits the cookie over a secure, encrypted connection (HTTPS), ensuring that any sensitive data (like session identifiers or user credentials) is not exposed over HTTP.
- Preventing Man-in-the-Middle (MITM) Attacks: Without the Secure flag, cookies can be sent over unencrypted connections, making it easier for attackers to intercept or manipulate the cookies in transit, leading to data theft or session hijacking.
Learn More: How to Select the Right HTTPS Method
How Secure Cookies Protect Session Data
Secure cookies play a vital role in protecting session data by ensuring that session cookies, which store user-specific information like login credentials, are transmitted securely between the browser and the server.
- Prevents Session Hijacking: By marking session cookies with the Secure flag, the data is transmitted only over HTTPS, which encrypts the connection. This prevents attackers from intercepting session cookies over insecure connections (HTTP), which could lead to unauthorized access.
- Mitigates Man-in-the-Middle (MITM) Attacks: With secure cookies, even if a user is on an untrusted network (like public Wi-Fi), the cookie data remains encrypted and safe from being stolen or altered by malicious actors.
- Protects Authentication Information: Cookies used for maintaining authentication states (such as login sessions) are often the target of attackers. The Secure flag ensures these cookies are only sent over encrypted channels, safeguarding user sessions from being hijacked.
Secure Cookies and SameSite Attribute
The SameSite attribute works alongside the Secure flag to control when cookies are sent with cross-site requests, providing an additional layer of security.
- SameSite and CSRF Protection: SameSite helps prevent Cross-Site Request Forgery (CSRF) attacks by restricting cookies from being sent with requests initiated by third-party websites. This ensures that cookies marked as SameSite=Strict or SameSite=Lax are not included in cross-origin requests, thus protecting user sessions from unauthorized actions.
- Enhancing Secure Cookie Behavior: When combined with SameSite=Lax or SameSite=Strict, Secure cookies offer protection not only by encrypting the cookie’s transmission but also by preventing it from being exposed in scenarios that could lead to data leakage or malicious actions from third-party sites.
- SameSite=None and Secure Cookies: For cross-site use, cookies must be marked as SameSite=None and must also be Secure. This ensures that cookies are sent only over HTTPS and only when absolutely necessary in cross-origin requests.
Must Read: How to handle Cookies in Selenium WebDriver
Common Use Cases for Secure Cookies
Secure cookies are essential in various web application scenarios, particularly when dealing with sensitive data. Here are some common use cases:
- User Authentication: Secure cookies are widely used to maintain user sessions and login states. Marking session cookies as Secure ensures they are only transmitted over encrypted connections, reducing the risk of session hijacking.
- Shopping Cart Persistence: E-commerce websites use Secure cookies to store items in a shopping cart, ensuring that the data is safely transmitted and preventing exposure to attackers.
- Personalization: Websites that store user preferences, such as language settings, themes, or display options, can use Secure cookies to ensure the privacy of such preferences during transmission.
- Third-Party Services: For third-party integrations (like ad networks or analytics services), Secure cookies are used to store user data and tracking information securely when cross-site cookies are necessary.
These use cases demonstrate the importance of Secure cookies in managing sensitive data and providing secure user experiences.
Security Risks Without Secure Cookies
Failing to use Secure cookies presents several significant security risks:
- Session Hijacking: Without the Secure flag, session cookies can be transmitted over insecure HTTP connections, leaving them vulnerable to interception by attackers through man-in-the-middle (MITM) attacks.
- Data Leakage: Cookies containing sensitive data, such as authentication tokens, are at risk of being exposed or stolen when sent over unencrypted channels, especially in public or untrusted networks.
- Increased Risk of XSS Attacks: Without proper cookie security settings (e.g., using HttpOnly and Secure), cookies can be accessed by client-side JavaScript, increasing vulnerability to cross-site scripting (XSS) attacks.
- Privacy Violations: If cookies are transmitted in insecure ways, user tracking data and preferences can be intercepted, leading to privacy violations and potential misuse of personal information.
Best Practices for Implementing Secure Cookies
To ensure cookies are secure and protect user data effectively, developers should follow these best practices:
- Always Use the Secure Flag: Ensure that cookies containing sensitive data (such as session tokens) are set with the Secure flag to guarantee they are only transmitted over HTTPS.
- Set HttpOnly for Session Cookies: Mark cookies with the HttpOnly flag to prevent JavaScript from accessing them, reducing the risk of cross-site scripting (XSS) attacks.
- Use the SameSite Attribute: Protect against cross-site request forgery (CSRF) by setting the SameSite attribute to Strict or Lax, restricting cookies to be sent only with same-site requests.
- Limit Cookie Scope with Path and Domain: Define appropriate Path and Domain attributes to limit the cookies’ accessibility, ensuring they are only used by the relevant parts of your website
- Ensure Cookies Are Expiring Appropriately: Set an appropriate expiration for cookies, especially session cookies, to minimize the risk of data exposure if they are not cleared.
Testing and Debugging Secure Cookies
Testing and debugging secure cookies is essential for ensuring they function as expected. Properly configured cookies can prevent security vulnerabilities, while incorrect configurations can expose sensitive data.
Testing tools like DevTools and Request Interceptors simplify this process, enabling developers to quickly identify and resolve issues.
1. Using DevTools to Inspect Secure Cookies
DevTools provides an efficient way to inspect Secure cookies by checking their attributes, such as Secure and HttpOnly. This helps ensure that cookies are correctly configured and only transmitted over secure HTTPS connections.
2. Using Request Interceptors
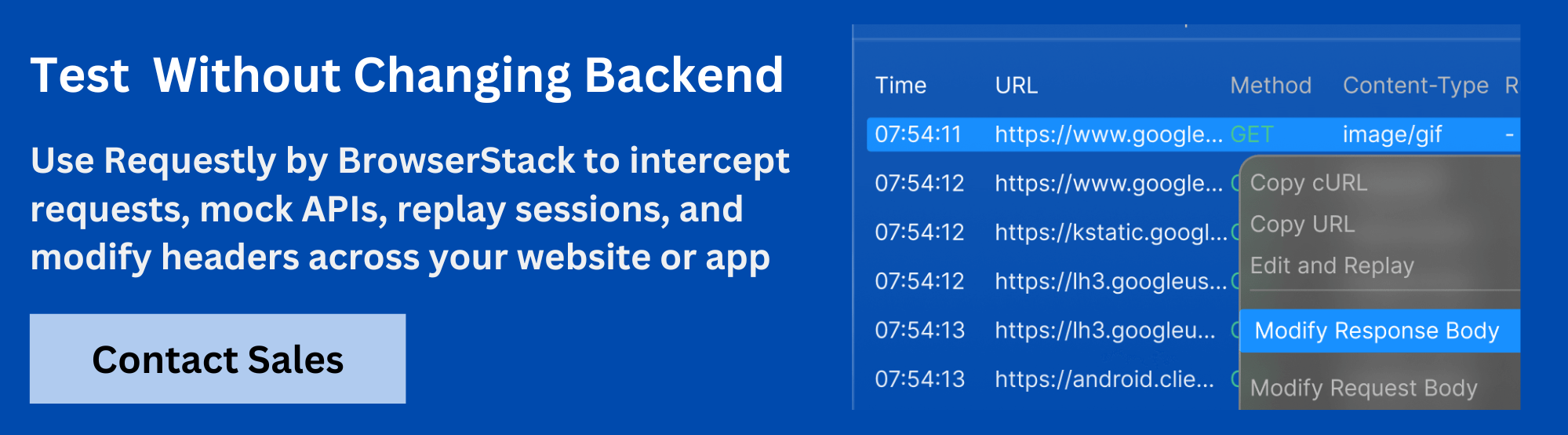
Requestly HTTP Interceptor is a powerful tool for developers looking to debug, modify, and test secure cookies directly in the browser, without needing to change backend code.
Key benefits of using Requestly:
- Modify Cookies in Real-Time: Easily change cookie values, including Secure and SameSite attributes, during live sessions without needing to update server-side code.
- Simulate Secure and Cross-Site Requests: Test how cookies behave across different origins, ensuring they are only sent when appropriate and when the Secure flag is active.
- Intercept and Debug Requests: Track all outgoing requests and inspect cookies to make sure they are properly secured and transmitted under HTTPS.
- Test Different Cookie Configurations: Simulate scenarios where cookies should or shouldn’t be sent based on SameSite settings, helping identify potential issues before they affect users.
Requestly makes it easy to test secure cookies, ensuring their correct functionality across different use cases and enhancing overall web application security.
Browser Compatibility and Secure Cookie Behavior
Secure cookies are supported by modern browsers, ensuring cookies are only transmitted over HTTPS. However, browser compatibility can vary, especially with older versions.
- Chrome, Firefox, Edge: These browsers enforce Secure cookies and SameSite behavior.
- Legacy Browsers: Older browsers may not fully support these features, which can lead to inconsistent behavior.
- Cross-Browser Testing: Always test across browsers to ensure secure cookie transmission works as expected.
Common Issues with Secure Cookies (With Solutions)
Secure cookies can sometimes cause issues, particularly in cross-origin scenarios. Here are some common problems and their solutions:
- Cookie Not Sent Over HTTP: Secure cookies require HTTPS. Ensure your site is HTTPS-enabled for cookie transmission.
- SameSite=None Requires Secure: Cookies with SameSite=None must be marked Secure. Always pair SameSite=None with the Secure flag.
- Compatibility Issues in Legacy Browsers: Older browsers may not support SameSite or Secure flags. Consider using alternative security mechanisms, like CSRF tokens, for legacy browser support.
Conclusion
Secure cookies are essential for protecting sensitive data and maintaining secure user sessions.
By following best practices and ensuring proper configuration, developers can improve privacy and mitigate risks like session hijacking and data theft.
Testing across browsers helps ensure consistent, secure cookie behavior across all platforms.