Clickjacking attacks exploit iframes to trick users into interacting with hidden or malicious elements, often without their knowledge. The frame-ancestors directive in Content Security Policy (CSP) addresses this problem by giving developers fine-grained control over which domains can embed their applications.
Overview
frame-ancestors is a Content Security Policy (CSP) directive that specifies which domains are allowed to embed a web page inside frames or iframes. It helps prevent unauthorized framing and protects against clickjacking attacks.
Security benefits of frame-ancestors:
- Prevents clickjacking by blocking unauthorized framing.
- Ensures only trusted domains can embed your application.
- Reduces risk of data theft through malicious overlays.
- Strengthens defense-in-depth when combined with other CSP rules.
- Provides flexible, modern protection beyond legacy headers.
This article explores how the frame-ancestors directive enhances web security, its differences from legacy headers, and practical ways to test and debug it.
Understanding frame-ancestors directive
The frame-ancestors directive is part of Content Security Policy (CSP) and controls which sources are permitted to embed a webpage using <frame>, <iframe>, <object>, <embed>, or <applet>. Unlike other directives, it must be set through HTTP response headers and cannot be applied via <meta> tags.
Key configuration options include:
- ‘none’ – Blocks all framing attempts.
- ‘self’ – Allows framing only from the same origin.
- Specific domains – Grants embedding rights to defined trusted domains (e.g., https://example.com).
- Wildcards – Used with caution to allow multiple subdomains.
By tailoring these values, developers can precisely control embedding behavior, reducing exposure to malicious framing and maintaining safer integration with partner applications.
Differences from X-Frame-Options
X-Frame-Options was the earlier header used to control framing, but it has several limitations compared to frame-ancestors. While both serve the purpose of preventing clickjacking, frame-ancestors provides greater flexibility and modern security coverage.
Key differences include:
- Flexibility: X-Frame-Options supports only DENY, SAMEORIGIN, or ALLOW-FROM (with limited browser support). frame-ancestors allows multiple domains, wildcards, and more granular rules.
- Compatibility: X-Frame-Options is supported by older browsers, while frame-ancestors is the CSP standard recommended for modern applications.
- Enforcement: frame-ancestors can define complex embedding policies within a single directive, something not possible with X-Frame-Options.
- Future-Proofing: frame-ancestors is actively maintained as part of CSP, whereas X-Frame-Options is deprecated.
Many applications choose to implement both headers, using frame-ancestors for modern browsers and X-Frame-Options for backward compatibility.
Security Benefits: Protecting Against Clickjacking
Clickjacking is a deceptive technique where attackers embed a legitimate webpage inside an invisible or disguised frame, tricking users into clicking buttons, entering credentials, or approving transactions without realizing it.
This type of attack not only compromises user trust but can also lead to financial fraud, data theft, or unauthorized actions on critical web applications.
The frame-ancestors directive plays a central role in mitigating these risks by defining precisely which domains are permitted to frame a webpage. Any site outside the allowed list is automatically blocked by the browser, preventing malicious embedding before it can even occur.
Key security benefits include:
- Defense against unauthorized framing: Ensures that only trusted domains, such as a company’s own platforms or verified partners, can embed the application.
- Prevention of hidden UI attacks: Stops attackers from overlaying invisible login forms, transaction buttons, or ads on top of legitimate interfaces.
- Preservation of sensitive workflows: Protects critical processes like banking logins, payment confirmations, or admin dashboards from being hijacked within a hostile frame.
- Reduced risk of session hijacking: By eliminating untrusted framing contexts, it limits the attacker’s ability to trick authenticated users into dangerous clicks.
- Alignment with modern security standards: As part of CSP, frame-ancestors is a forward-looking approach, replacing older mechanisms with granular control that aligns with OWASP recommendations.
In practice, this directive adds a strong layer of security against one of the most prevalent threats on the web. When combined with other CSP rules and robust input validation, it significantly reduces the attack surface for web applications and APIs.
Real-World Troubleshooting
Even with frame-ancestors properly configured, developers and testers often encounter unexpected behavior when working with framed content. A common issue is when an iframe request returns a valid 200 OK response, yet the embedded page appears blank. This happens because the browser silently enforces the CSP rule, blocking the frame without breaking the network request.
Key troubleshooting scenarios include:
- Blank iframes despite successful responses: If a page loads normally on its own but appears empty when framed, check the browser console.
- Nested iframe conflicts: When multiple iframes are chained together, every ancestor must satisfy the directive. A single non-compliant frame in the hierarchy will block the content.
- Misconfigured header placement: Since frame-ancestors only works when set in HTTP response headers (not <meta> tags), embedding will fail if it’s incorrectly configured in markup.
- Cross-domain embedding failures: If a trusted partner or third-party app is unable to embed content, verify whether their domain is explicitly listed in the frame-ancestors directive. Missing or incorrect protocol (http vs https) is a frequent oversight.
By reviewing developer tools, inspecting CSP headers in network responses, and validating embedding behavior across different origins, teams can quickly identify and resolve framing issues. Proactive testing in staging environments helps surface these problems before they impact production systems.
How to Test frame-ancestors in APIs/UI Tests
Testing frame-ancestors is essential to confirm that CSP rules are applied correctly and reliably protect against unauthorized framing. The process involves both header validation and behavioral checks.
- Check response headers: Use authentic tools to verify that the Content-Security-Policy header includes the expected frame-ancestors directive.
- Positive and negative iframe tests: Try embedding the page from an allowed domain (should succeed) and from a disallowed domain (should be blocked by the browser).
- Inspect console errors: Look for CSP violation messages in developer tools when an iframe is blocked.
- Automate in CI/CD: Add header checks and iframe embedding tests in your test suite to catch misconfigurations before release.
- Edge cases: Test nested iframes, protocol-specific rules, and wildcard usage to ensure the directive behaves as intended.
These checks help ensure that frame-ancestors is not only present but also consistently enforcing the intended security policy across different scenarios.
Read More: Cypress API Testing: A Comprehensive Guide
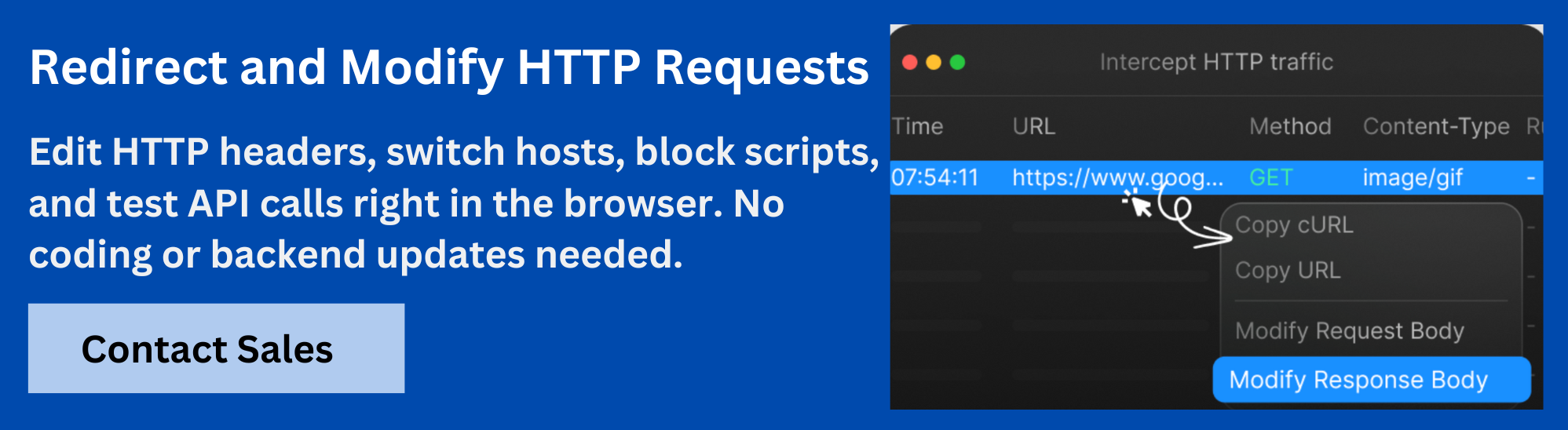
Debugging Frame Issues with Requestly HTTP Interceptor
When iframes fail to load due to restrictive frame-ancestors settings, identifying the root cause can be challenging. Requestly HTTP Interceptor by BrowserStack simplifies this process by allowing testers to inspect, modify, and simulate HTTP response headers directly in the browser.
With Requestly, you can:
- Inspect CSP headers: Quickly confirm if frame-ancestors is present and correctly configured.
- Modify headers on the fly: Temporarily add, remove, or adjust the directive to test different embedding scenarios without server changes.
- Reproduce security issues: Simulate misconfigurations to understand how the browser responds when an origin is missing or incorrectly allowed.
- Speed up troubleshooting: Eliminate the need for repeated backend deployments when debugging framing behavior.
By using Requestly, API testers and developers can validate frame-ancestors policies more efficiently, ensuring CSP rules work as intended while reducing the turnaround time for debugging.
Best Practices and Recommendations
A well-configured frame-ancestors directive strengthens application security, but it must be applied carefully to avoid blocking legitimate use cases or leaving gaps. The following best practices help strike the right balance:
- Adopt a deny-first approach: Start with frame-ancestors ‘none’ and open up access only to trusted domains as needed.
- Allow only explicit, trusted origins: Use specific domains (e.g., https://partner.example.com) instead of wildcards to reduce exposure.
- Combine with legacy headers for coverage: Keep X-Frame-Options alongside frame-ancestors to support older browsers that may not fully enforce CSP.
- Test across different environments: Validate the directive in staging and production to ensure consistency in behavior and avoid unexpected blocking.
- Monitor and audit regularly: Include frame-ancestors checks in automated tests and security scans to catch accidental misconfigurations.
- Pair with layered defenses: Use it alongside other CSP directives and input validation for a more comprehensive security posture.
By following these practices, teams can ensure that framing protections remain effective, compatible, and aligned with broader application security goals.
Conclusion
The frame-ancestors directive is a modern, flexible, and reliable defense against clickjacking and unauthorized framing. By defining exactly which domains can embed your application it prevents attackers from exploiting hidden frames while still allowing legitimate integrations.
When paired with thorough testing, smart debugging tools like Requestly HTTP Interceptor, and ongoing monitoring, it becomes a key pillar of a robust web security strategy.