The presence of “unsafe-inline” in Content Security Policies (CSP) poses significant security risks, particularly exposing web applications to XSS attacks.
Overview
What is “Unsafe Inline”?
“Unsafe-inline” is a directive in Content Security Policy (CSP) that allows inline scripts and styles to execute in web applications. It is considered a security risk because it opens the door for Cross-Site Scripting (XSS) attacks.
How “Unsafe Inline” Affects Web Applications:
- XSS Vulnerabilities: Allows malicious scripts to be injected into a webpage, compromising user data and security.
- Weakens CSP Protection: Reduces the effectiveness of CSP in preventing unauthorized code execution.
- Compromises User Trust: Can lead to data theft, unauthorized access, or malicious actions affecting end users.
- Browser Compatibility Issues: Some browsers may ignore CSP headers or not properly block inline scripts, leaving applications exposed.
This article addresses the risks associated with “unsafe-inline,” provides insights into securing web applications, and offers practical solutions to eliminate this security flaw.
What is “Unsafe Inline” in CSP?
“Unsafe-inline” is a keyword used in the Content Security Policy (CSP) header to allow inline JavaScript or CSS within a webpage. When included in the CSP, it permits the execution of inline scripts or styles, which is considered a security risk.
This directive makes it easier for attackers to inject malicious code (such as Cross-Site Scripting or XSS attacks), bypassing the protective measures CSP is meant to provide. Therefore, it’s highly recommended to avoid using “unsafe-inline” and adopt safer alternatives like nonces or hashes to secure content.
Read More: What are CORS Errors: The Complete Guide
The Role of Content Security Policy (CSP)
Content Security Policy (CSP) is a security feature that helps prevent a range of attacks, including Cross-Site Scripting (XSS) and data injection attacks, by controlling which resources (scripts, styles, images, etc.) can be loaded and executed on a web page. It works by defining a set of rules, or directives, that dictate where content can be loaded from and which actions are allowed within a webpage.
CSP significantly enhances web security by:
- Restricting Script Execution: Only allows scripts from trusted sources and prevents unauthorized inline scripts (unless explicitly allowed).
- Mitigating XSS: Blocks malicious script injections from external sources or attackers.
- Defining Resource Loading: Controls where assets like images, fonts, or stylesheets can be loaded from, reducing the risk of data leaks or unauthorized access.
By enforcing CSP, developers can minimize the surface area for potential attacks, making their applications more secure.
How “Unsafe Inline” Affects Web Applications
Here’s how “unsafe-inline” can negatively impact the security and functionality of your web application:
- Increases Vulnerability to XSS Attacks: Allowing inline scripts via “unsafe-inline” opens the door for attackers to inject malicious code into your website, compromising user data and session integrity.
- Weakens CSP Protection: The use of “unsafe-inline” significantly diminishes the effectiveness of CSP, which is designed to block unauthorized scripts. By permitting inline scripts, CSP cannot fully protect against script-based attacks.
- Compromises Application Integrity: Malicious code from injected inline scripts can manipulate website content, steal sensitive information, or redirect users to harmful sites, undermining the trust in your application.
- Hinders Best Security Practices: Enabling “unsafe-inline” goes against web security best practices, making it harder to implement modern, secure coding methods like content integrity verification (using nonces or hashes).
- Potential Browser Inconsistencies: Some browsers may not fully enforce CSP or might allow inline scripts to execute despite the security headers, leading to inconsistent behavior across different platforms.
Best Practices for Securing Web Applications
To effectively secure your web applications and avoid the risks associated with “unsafe-inline,” follow these best practices:
- Remove “unsafe-inline” from CSP: Avoid using “unsafe-inline” in your CSP header. Instead, use nonces or hashes to allow specific scripts while maintaining strict security.
- Use Nonces and Hashes: Implement nonces (random values) or hashes to identify trusted inline scripts, allowing their execution while preventing others.
- Leverage External Scripts and Styles: Move inline scripts and styles to external files, which can be easily verified and controlled through CSP.
- Enable Report-Only Mode: Use the Content-Security-Policy-Report-Only header to test CSP configurations without enforcing them, allowing you to identify issues without breaking functionality.
- Regularly Review and Update CSP: Periodically audit your CSP settings to ensure they remain up-to-date with the latest security standards and best practices.
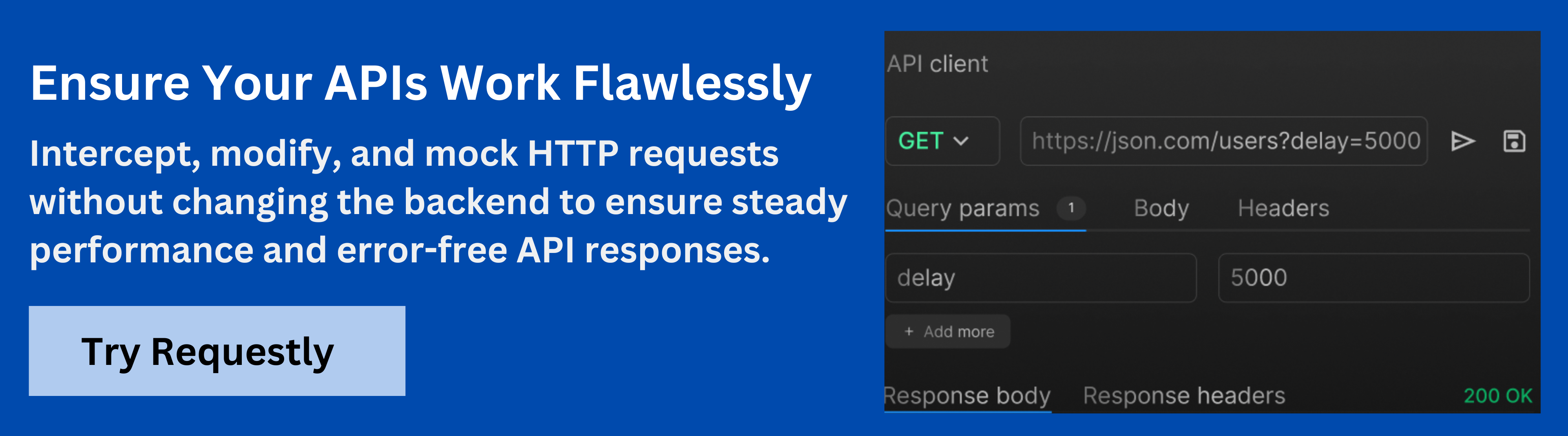
- Test CSP Implementation: Use security tools like Requestly to test and validate your CSP configurations, ensuring that “unsafe-inline” is properly blocked and no vulnerable scripts are allowed.
Read More: Popular API Examples and Use Cases
How to Eliminate “Unsafe Inline” from Your Web Application
To effectively eliminate “unsafe-inline” from your web application and enhance its security, follow these steps:
- Update Your Content Security Policy (CSP): Remove “unsafe-inline” from your CSP configuration. Instead, specify trusted sources for scripts and styles by using directives like script-src and style-src.
- Use Nonces or Hashes for Inline Scripts: Replace inline scripts with nonces (unique tokens) or hashes to ensure that only trusted inline scripts are executed. Nonces are added to the CSP header, and each inline script is given a corresponding nonce.
- Move Inline Scripts to External Files: Shift all inline scripts and styles to external files, and reference them through the CSP script-src and style-src directives. This makes the resources easier to manage and verify.
- Refactor Inline Event Handlers: Inline event handlers (e.g., onclick=”alert(‘Hello’)) can be moved into external JavaScript files. Use event delegation or JavaScript functions to add event listeners.
- Use Trusted Script Libraries: Load external libraries and frameworks from trusted, secure sources. Ensure these external resources are also CSP-compliant by adding them to the CSP directives (e.g., script-src).
- Test CSP Changes: Before fully implementing changes, use the Content-Security-Policy-Report-Only header to test your CSP changes and identify any issues without breaking your site’s functionality.
- Perform Regular Security Audits: Continuously audit your web application for CSP misconfigurations and test for security vulnerabilities. Utilize tools like Requestly to ensure that your policy is working as intended and to track potential vulnerabilities.
Challenges and Workarounds
While eliminating “unsafe-inline” from your web application is a crucial security measure, there are several challenges you may encounter, along with potential workarounds:
1. Legacy Systems and Third-Party Scripts: Older web applications or third-party libraries may rely on inline scripts, making it difficult to eliminate “unsafe-inline” completely.
Workaround: Refactor legacy code by moving inline scripts to external files. For third-party scripts, try to replace them with modern, CSP-compliant alternatives or use trusted script sources with proper hashes or nonces.
2. Browser Compatibility Issues: Some browsers may not fully support CSP or may implement it inconsistently, leading to potential issues with enforcing “unsafe-inline” policies across all users.
Workaround: Regularly test your application on different browsers to ensure compatibility. You can use the Content-Security-Policy-Report-Only mode to identify issues and make adjustments before enforcing strict policies.
3. Inline Event Handlers: Inline event handlers (e.g., onclick, onmouseover) in HTML can be challenging to move to external scripts, especially in large, complex applications.
Workaround: Use event delegation and JavaScript functions to bind events to elements dynamically, avoiding the need for inline event handlers altogether.
4. Performance Concerns with External Scripts: Moving inline scripts to external files can sometimes lead to performance issues due to additional HTTP requests for each script.
Workaround: Minimize the number of external script files by combining them where possible. Use techniques like script bundling and caching to reduce load times and improve performance.
5. Complexity of Migrating to CSP-compliant Code: Refactoring an entire web application to comply with CSP can be time-consuming and may require significant changes to the codebase, especially if the application was not initially designed with security in mind.
Workaround: Gradually implement changes using the Content-Security-Policy-Report-Only header to monitor the impact of your changes and address any issues before enforcing full security policies.
Test and Debug Unsafe Inline Issues with Requestly
Requestly by BrowserStack can be a useful tool for testing and debugging unsafe-inline issues related to Content Security Policy (CSP). Here’s how you can leverage it:
- Modify and Test CSP Headers: Use Requestly to dynamically alter CSP headers and simulate scenarios with or without unsafe-inline. This helps you understand how your application responds to changes in CSP configuration.
- Test Script Behavior: Intercept and modify requests to observe how inline scripts behave when unsafe-inline is allowed or blocked by your CSP settings.
- Inspect Network Traffic: Monitor network traffic to ensure that your CSP is properly enforcing or rejecting inline scripts, and identify any potential issues related to the handling of unsafe-inline.
With Requestly, you can easily validate that unsafe-inline is being properly managed and that your application adheres to security best practices. For a more comprehensive security analysis, combining Requestly with other testing tools is recommended.
Conclusion
Eliminating “unsafe-inline” from your web application is a crucial step in enhancing security and protecting against vulnerabilities like Cross-Site Scripting (XSS). By understanding the risks associated with inline scripts and adopting best practices such as using nonces, hashes, and external scripts, you can significantly strengthen your Content Security Policy (CSP).
While challenges such as legacy systems and browser compatibility may arise, tools like Requestly provide an effective way to test, debug, and ensure your CSP is properly configured. By following these strategies, you can create a more secure web application and provide a safer experience for your users.