The Cookie header is a key part of HTTP that enables browsers to send stored cookies back to the server with every relevant request. It plays a critical role in session management, personalization, and user tracking.
Overview
Common uses of Cookie Header include:
- Session Management: Maintains login state or shopping cart data
- Personalization: Stores language, theme, or layout preferences
- Tracking: Records user behavior for analytics and advertising
Syntax Of Cookie Header:
The Cookie header is a list of name-value pairs, separated by semicolons.
Example:
Cookie: userId=12345; theme=dark; loggedIn=true
This guide explains how the Cookie header works, its structure, common use cases, and best practices for secure and efficient implementation.
What is the Cookie Header?
The Cookie header is an HTTP request header used by browsers to send stored cookies back to the server. These cookies typically contain session identifiers, user preferences, or other stateful data required to maintain continuity between client and server interactions.
The header is automatically added to outgoing requests by the browser whenever a cookie is associated with the requested domain and path. This allows servers to recognize returning users and serve personalized content or maintain sessions without requiring repeated authentication.
The Cookie header is different from Set-Cookie, which is used by servers to instruct the browser to store a cookie. In contrast, the Cookie header is the mechanism through which the browser sends those stored cookies back to the server.
Read More: Understanding Cookies in Software Testing
Structure and Syntax of Cookie Header
The Cookie header follows a simple syntax where each cookie is expressed as a key-value pair. Multiple cookies are separated by semicolons.
Basic Syntax:
Cookie: name1=value1; name2=value2
Each pair represents a single cookie previously set by the server using the Set-Cookie response header. The header does not include cookie attributes like Secure, HttpOnly, or Path. These attributes are used during cookie storage and are not sent in the request header.
Example:
Cookie: session_id=abc123; theme=dark; loggedIn=true
In this example, the browser sends three cookies to the server. All were previously stored and are valid for the current domain and path.
How Cookie Header Works in HTTP Requests
Here’s a step-by-step breakdown of how the Cookie header functions during client-server communication:
- Server Sends Set-Cookie Header: The server sets cookies using the Set-Cookie response header, including attributes like domain, path, and expiration.
- Browser Stores The Cookies: The browser saves the cookies and associates them with the specified domain and path.
- Browser Adds Cookie Header To Requests: For future requests to the same domain and path, the browser includes a Cookie header with the relevant cookies.
- Header Sent Only If Conditions Match: Cookies are included only if the request meets the original Set-Cookie attributes.
- Server Reads And Uses Cookie Data: The server extracts cookie values from the header to identify sessions or apply preferences.
- Response Is Customized Accordingly: Based on the cookie data, the server delivers a personalized or session-aware response.
Difference Between Cookie and Set-Cookie Header
The Cookie and Set-Cookie headers serve different roles in the HTTP request-response cycle.
| Header | Direction | Purpose |
|---|---|---|
| Set-Cookie | Server → Client | Instructs the browser to store a cookie |
| Cookie | Client → Server | Sends stored cookies to the server in a request |
- Set-Cookie is sent by the server in the response header. It defines the cookie name, value, and optional attributes like Path, Secure, HttpOnly, and SameSite.
- Cookie is sent by the browser in the request header. It contains the name-value pairs of cookies previously set and valid for the current domain and path.
In simple terms, Set-Cookie creates or updates cookies, while Cookie sends them back to the server.
Purpose of using Cookie Header
The Cookie header plays a key role in maintaining stateful communication in an otherwise stateless HTTP protocol. It allows the browser to send stored cookie data back to the server with every relevant request.
Common purposes include:
- Session Management: Keeps users logged in by identifying active sessions.
- User Preferences: Remembers settings like language, theme, or layout.
- Personalized Content: Delivers user-specific data such as recommendations or saved items.
- Tracking and Analytics: Enables usage tracking and user behavior analysis.
Without the Cookie header, each request would be treated as independent, breaking continuity across user sessions and features.
Key Components of Cookie Header
The Cookie header contains one or more name-value pairs, each representing a stored cookie. While attributes like Secure and HttpOnly are part of the Set-Cookie header, only the name-value pairs are included in the Cookie header.
Main components include:
- Name: Identifier for the cookie (e.g., session_id)
- Value: Stored data (e.g., abc123)
- Delimiter: Each cookie pair is separated by a semicolon and a space
Example:
Cookie: session_id=abc123; theme=dark; loggedIn=true
This format allows the server to parse and process individual cookies as needed. Only cookies matching the current domain and path are sent in the Cookie header.
How Browsers Handle Cookie Header
Browsers automatically manage when and how the Cookie header is sent during HTTP requests. Once a cookie is stored using the Set-Cookie header, the browser includes it in all future requests that match the cookie’s domain, path, and security rules.
Key behaviors include:
- Automatic Inclusion: Browsers add the Cookie header without developer intervention for matching requests.
- Scope Matching: Only cookies valid for the request’s domain and path are included.
- Secure Contexts: Cookies marked with the Secure attribute are sent only over HTTPS.
- Expiration Handling: Expired cookies are removed and not included in requests.
This automated behavior simplifies session handling and user identification across multiple pages or visits.
Cookie Storage: Session vs Persistent Cookies
Cookies can be stored either temporarily or persistently, depending on how they are set.
| Feature | Session Cookies | Persistent Cookies |
|---|---|---|
| Storage Duration | Stored in memory | Stored on disk |
| Expiration | Deleted when the browser is closed | Retained until the specified expiration time |
| Set-Cookie Usage | No Expires or Max-Age attributes | Includes Expires or Max-Age attributes |
| Use Cases | Temporary login sessions, single-visit data | Remembering login status, user preferences |
| Security Impact | Lower risk due to short lifespan | Must be managed carefully to prevent misuse |
Security Considerations for Cookie Header
Because cookies often contain sensitive information like session tokens or user identifiers, securing the Cookie header is critical.
Key security practices:
- HttpOnly: Prevents client-side scripts from accessing the cookie, reducing the risk of cross-site scripting (XSS) attacks.
- Secure: Ensures cookies are only sent over encrypted HTTPS connections.
- SameSite: Restricts when cookies are sent in cross-site requests to help prevent cross-site request forgery (CSRF).
- Minimal Exposure: Avoid storing personally identifiable or sensitive data in cookies.
Proper use of these attributes helps protect user sessions, improve privacy, and maintain trust in web applications.
Also Read: How to handle Cookies in Selenium WebDriver
Practical Use Cases of Cookie Header
The Cookie header plays a vital role in modern web applications by enabling servers to identify and maintain state for each user.
Below are common scenarios where the Cookie header is actively used:
- User Authentication: Stores session tokens to maintain login states across multiple pages.
- Personalized Content: Remembers user preferences such as language, theme, or layout settings.
- Shopping Carts: Saves items in a cart even if the user navigates away or returns later.
- Analytics And Tracking: Associates user activity with unique identifiers for behavioral analysis.
- Feature Access Control: Enables or disables features based on user roles or preferences.
These use cases highlight how the Cookie header supports both functionality and user experience in web applications.
How to Read and Modify Cookie Header in the Browser
Inspecting and modifying cookie headers is useful for debugging and testing purposes. Developers can use built-in browser tools or external extensions to monitor how cookies are sent and received.
There are two common ways to read and modify Cookie Header in browser:
- Using DevTools
- Using Request Interceptors like Requestly
Both methods offer real-time insights into how the Cookie header behaves during HTTP transactions.
Using DevTools
Browser DevTools provide a simple and effective way to view cookie headers during network requests.
Steps to read the Cookie header using DevTools:
- Open the web application in a browser (Chrome, Firefox, or Edge).
- Right-click the page and select Inspect to open DevTools.
- Navigate to the Network tab.
- Reload the page to capture network activity.
- Click on a request and go to the Headers section.
- Look under Request Headers for the Cookie entry.
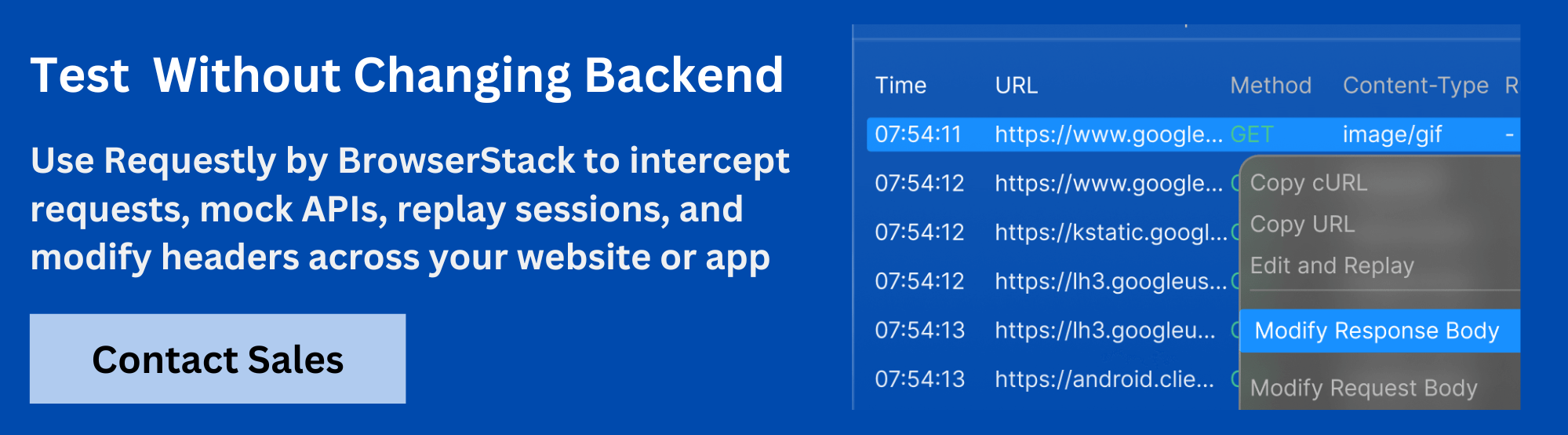
Using Request Interceptors
While DevTools is useful for inspection, developers often need more control to test how different cookie values affect application behavior. This is where Requestly HTTP Interceptor becomes essential.
Requestly HTTP Interceptor lets you:
- Intercept and modify the Cookie header before it reaches the server
- Simulate different cookie values without editing backend logic
- Block or redirect requests based on cookie conditions
- Debug authentication or session issues quickly and safely
Unlike DevTools, Requestly gives you full control over outgoing requests, making it ideal for frontend testing, security validation, and QA workflows.
Limitations and Challenges With Cookie Header
While the Cookie header enables powerful session and state management, it also comes with certain limitations and challenges developers must consider.
Key limitations include:
- Size Restrictions: Most browsers limit cookie size to around 4KB per cookie and a total of 20–50 cookies per domain.
- Performance Overhead: Every request to the server carries the Cookie header, even if the data is not needed, which can increase request payloads.
- Lack of Granular Control: The Cookie header sends all applicable cookies, even if only one is needed for a specific endpoint.
- Inconsistent Cross-Browser Behavior: Cookie handling may vary slightly across browsers, especially for attributes like SameSite.
- Security Risks: Cookies are vulnerable to theft or manipulation if not properly secured using HttpOnly, Secure, and SameSite flags.
Also Read: How to test HTTPS Websites from Local Host
Best Practices for Setting and Sending Cookie Headers
To ensure cookies are handled securely and efficiently, developers should follow proven best practices when setting and using the Cookie header.
Recommended practices include:
- Use HttpOnly For Sensitive Data: Prevents JavaScript access to authentication cookies.
- Always Use Secure For HTTPS Sites: Ensures cookies are not sent over insecure connections.
- Set SameSite Attribute: Helps defend against cross-site request forgery (CSRF) attacks.
- Minimize Cookie Size: Keep cookies lean to reduce request overhead.
- Limit Scope With Domain And Path: Restrict cookies to only the necessary parts of the site.
- Avoid Storing Sensitive Information: Do not store passwords or personal identifiers in cookies.
Conclusion
The Cookie header is an essential component of modern web communication, allowing browsers to send stored data back to the server with each request. It plays a key role in user authentication, personalization, and session persistence.
While powerful, the Cookie header requires careful handling to avoid security vulnerabilities, performance issues, and browser inconsistencies. By understanding its structure, purpose, and limitations, and by using tools like Requestly, developers can manage cookies effectively and build more secure, responsive applications.