Debugging network traffic is essential to ensure your iOS app communicates correctly with servers, handles data properly, and delivers a smooth user experience. However, capturing and analyzing network traffic in the iOS simulator can be frustrating and time-consuming. Complex proxy setups, SSL encryption, and simulator limitations often block easy access to this data.
This article guides you through setting up network interception on the iOS simulator by configuring proxies, installing certificates, and troubleshooting common issues.
What is Network Interception on iOS Simulator?
Network interception on an iOS Simulator means capturing and analyzing the data exchanged between apps running on the simulator and the network. This includes requests sent from the app to servers, responses returned, headers, payloads, and other network metadata.
Intercepting network traffic on the simulator allows testing how apps handle real-world network conditions, verifying API calls, checking security protocols like SSL/TLS, and manipulating responses to test app behavior under various scenarios. It is crucial to ensure app reliability, performance, and security before deployment.
Challenges When Intercepting Network Traffic in the iOS Simulator
Intercepting network traffic in the iOS Simulator poses several challenges that testers and developers must understand and overcome. These challenges stem from the way the simulator handles networking, iOS security policies, and its integration with the host Mac system.
- Proxy Configuration Complexity: The simulator shares the Mac’s network stack, but configuring proxies correctly for interception requires manual setup. Misconfiguration can cause no traffic or incomplete capture.
- HTTPS and SSL Pinning: Modern iOS apps use HTTPS with SSL pinning to prevent man-in-the-middle attacks. Intercepting HTTPS traffic requires installing custom root certificates and bypassing pinning mechanisms, which is complex and often app-specific.
- Simulator Visibility Issues: Tools used for interception may not always detect the running simulator automatically. This causes difficulty in routing traffic through interception tools.
- Traffic Volume and Filtering: The simulator can generate vast amounts of network traffic, including system calls. Filtering relevant app traffic without noise demands precise configuration.
- Physical Device vs Simulator Differences: Some network behaviors differ between real devices and the simulator, which affects the accuracy of interception results.
- Performance Impact: Running interception tools and proxies alongside the simulator can slow down the testing environment, requiring resource balancing.
How to Set Up an iOS Simulator for Network Interception?
Setting up the iOS Simulator involves preparing a project in Xcode, launching the simulator, and configuring it for network interception. Follow these steps carefully to ensure you can intercept traffic successfully.
1. Create or Open a Project in Xcode
Before running your app on the simulator, you must have a project ready. You can open an existing project or create a new one by following these steps:
- Open Xcode on your Mac.
- To open an existing project, click File > Open and select the project file.
- To create a new project, select File > New > Project. In the iOS tab, select App and click Next.
- Configure the project by:
- Naming it (for example, “NetworkTestApp”).
- Choosing the programming language (Swift or Objective-C).
- Providing organization details and an identifier if required.
- Click Next, select a folder to save your project, then click Create.
- To ensure there are no errors, build the project by pressing Command + B or choosing Product > Build.
2. Open the Simulator in Xcode
Once your project is ready, launch the iOS Simulator by running your app or opening it manually:
- Click the dropdown near the Run button in Xcode to select the device to simulate. Select the desired iPhone or iPad model.
- Run the app by clicking the Run button or pressing Command + R. The simulator will launch automatically when your app is running.
- To open the simulator independently (without running the app), navigate in Finder to /Applications/Xcode.app/Contents/Developer/Applications/Simulator.app and launch it.
3. Configure and Launch the Simulator
The iOS Simulator uses your Mac’s network settings. Prepare your Mac and simulator environment for interception with these steps:
- Confirm your Mac is connected to the network you want the simulator to access.
- Remember that the simulator inherits network and proxy settings from your Mac.
- If you need to test a specific iOS version, download it from Xcode’s Preferences > Components.
- Launch your app inside the simulator to generate network traffic.
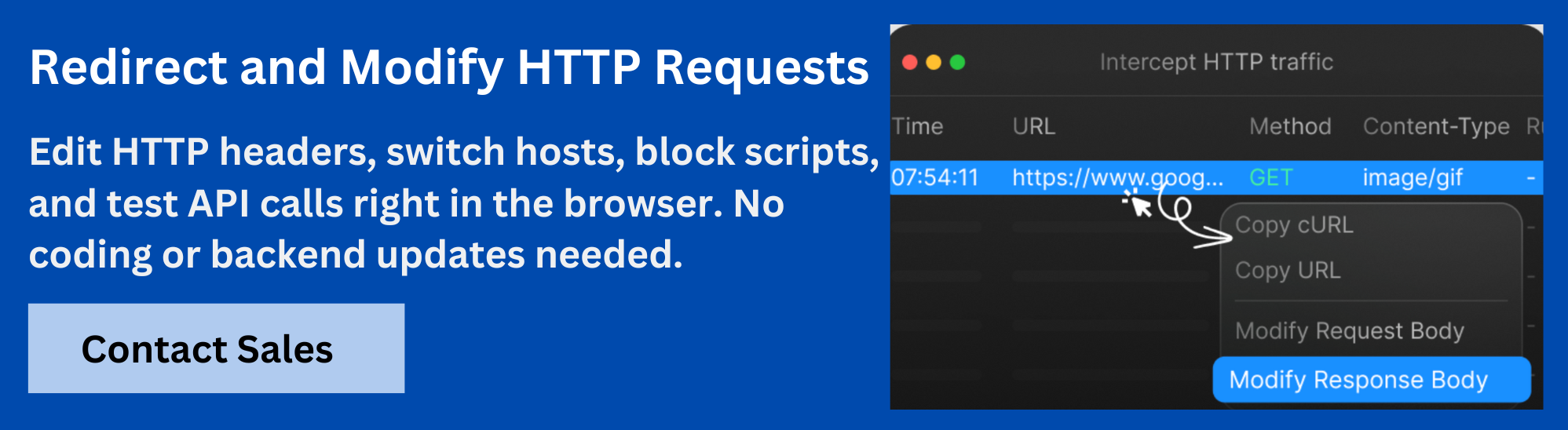
Why Use Requestly to Intercept iOS Network Traffic?
Requestly is a powerful and flexible tool designed to intercept, modify, and debug network traffic from iOS Simulators and other environments. Here are a few reasons why Requestly stands out for this purpose.
- Ease of Setup: Requestly offers a one-click simulator setup process that simplifies proxy configuration and certificate installation. This removes much of the manual work usually required.
- Cross-Platform Support: It supports macOS and integrates well with the iOS Simulator, enabling smooth traffic routing without advanced networking knowledge.
- Rule-Based Traffic Manipulation: Requestly allows you to create rules that can block, redirect, modify requests, or inject custom responses. This helps test edge cases or simulate backend failures without changing the actual server.
- HTTPS Traffic Interception: Requestly handles installing custom CA certificates to intercept HTTPS traffic safely, helping bypass SSL pinning for testing purposes.
- Real-Time Traffic Filtering and Monitoring: You can filter traffic by app or domain and inspect details instantly, which speeds up debugging and validation.
How to Intercept Network Traffic Using Requestly
Requestly is a macOS tool that captures and modifies network traffic from the iOS Simulator. Setting it up involves installing Requestly, connecting the simulator through proxy configuration, and installing certificates for HTTPS interception. Follow these steps to configure everything properly.
1. Install and Launch Requestly
Download and install Requestly on your Mac to begin capturing network traffic from the iOS Simulator:
- Visit the Requestly website and download the macOS installer.
- Run the installer and follow the on-screen instructions to complete the installation.
- Launch Requestly once installation finishes.
2. Configure the iOS Simulator Proxy for Requestly
Set up the iOS Simulator to route network requests through Requestly by configuring its proxy settings:
- Open the iOS Simulator and go to Settings > Wi-Fi.
- Tap the info icon next to the connected network.
- Scroll down to HTTP Proxy and select Manual.
- Enter the IP address (127.0.0.1 usually) and the port number provided by Requestly.
- Save the settings and exit.
3. Use the One-click Setup to Configure the Simulator Proxy
Simplify proxy setup using Requestly’s one-click configuration:
- Open Requestly and find the One-click Simulator Setup option.
- Click it to configure proxy settings on the simulator automatically.
- Skip manual proxy configuration.
4. Export and Install the Requestly CA Certificate on the Simulator
Enable HTTPS interception by installing and trusting Requestly’s Certificate Authority (CA) certificate on the simulator:
- Export the CA certificate from Requestly.
- Open Safari in the simulator and navigate to the certificate URL or drag and drop the certificate file into the simulator.
- Follow the prompts to install the certificate.
- Go to Settings > General > About > Certificate Trust Settings.
- Enable full trust for the installed certificate.
Troubleshooting Network Interception
Network interception on the iOS Simulator can sometimes fail or show unexpected behavior. Here are some common issues and their solutions to help ensure smooth interception and testing.
What if My Simulator Does Not Show in Requestly?
If your iOS Simulator does not appear in Requestly or connect properly, it usually means the proxy or connection settings are not correctly configured or recognized.
Check these points to resolve the issue:
- Verify Proxy Settings: Ensure the simulator’s Wi-Fi proxy is set to the correct IP and port Requestly expects. Even a small typo can cause failure.
- Ensure Simulator and Requestly are on the Same Network: If your Mac has multiple network interfaces (Wi-Fi, Ethernet, VPN), confirm the IP address used matches the active interface.
- Restart Simulator and Requestly: Sometimes the simulator or Requestly app needs a restart to detect each other appropriately.
- Disable Firewall or Security Software Temporarily: Your Mac’s firewall or antivirus software might block the proxy connection. Disable them briefly to see if they cause the problem.
- Update Requestly and Xcode: Using outdated versions may cause compatibility issues. Keep both tools up to date.
How to Troubleshoot a Missing Simulator
If the simulator is missing from the list or does not launch correctly, try these steps:
- Open Xcode and Verify Simulators: Go to Window > Devices and Simulators in Xcode to check if the simulator exists. Add a new simulator with the appropriate device and iOS version if it is missing.
- Reset Simulator Content and Settings: From the Simulator menu, select Device > Erase All Content and Settings. This clears corrupted data that might prevent proper operation.
- Restart Xcode and Mac: A fresh start can fix temporary glitches in simulator detection.
- Check Xcode Command Line Tools: Run xcode-select –install in Terminal to ensure command line tools are installed and up to date.
- Delete Derived Data: Sometimes corrupted build data causes simulator issues. In Xcode, go to Preferences > Locations and click the arrow next to Derived Data. Delete the contents of the folder.
How to Intercept HTTPS Traffic on iOS Simulator?
Intercepting HTTPS traffic requires additional steps because HTTPS encrypts data. Follow these steps:
- Export the Requestly CA Certificate: In Requestly, export the custom Certificate Authority (CA) certificate used to decrypt HTTPS traffic.
- Install the CA Certificate in Simulator: Open Safari on the simulator and access the certificate URL, or drag and drop the certificate file into the simulator.
- Install the Profile: The certificate installs as a profile. Open Settings > General > Profile (or Profiles & Device Management) and install the certificate profile.
- Enable Full Trust: Navigate to Settings > General > About > Certificate Trust Settings and enable complete trust for the installed certificate. Without this, HTTPS interception will fail.
- Restart the Simulator: Restart to ensure the changes take effect.
Advanced Network Interception Topics
After you have set up basic interception on the iOS Simulator, you can use advanced techniques to improve the precision and scope of your testing. These methods help you focus on specific apps, handle multiple devices, and refine your traffic capture to suit complex scenarios.
Filter Network Traffic by App Name
When multiple apps run on the simulator or device, capturing all network traffic can be overwhelming. Filtering traffic by app helps you isolate relevant requests and responses.
To filter traffic by app in Requestly or similar tools, use these approaches:
- Enable Process Identification: Requestly can link network requests to the specific process or app generating them. Enable this in the tool’s settings to see requests grouped by app.
- Set Filters Using Bundle Identifier: Use the app’s unique bundle identifier (e.g., com.yourcompany.appname) in your filtering rules to capture only the traffic from that app.
- Use Simulator Network Logs: Xcode’s Devices window lets you view the simulator’s network logs. Filter these logs by app to examine traffic without external tools.
- Apply Custom Proxy Rules: Advanced users may set up multiple proxy configurations or use command-line tools to route traffic differently based on the app, providing granular control over interception.
Intercept Traffic on Physical iOS Devices
Capturing network traffic on real devices requires extra care because of security restrictions and differences in network setup compared to the simulator.
Keep these points in mind:
- Configure Device Proxy: Set your device’s Wi-Fi proxy manually to the IP address and port of your interception tool.
- Install and Trust CA Certificate: To decrypt HTTPS traffic, install the interception tool’s Certificate Authority (CA) certificate on the device and enable full trust.
- Understand Device Limitations: Some apps use SSL pinning or advanced security measures that block interception. Installing certificates can be harder on physical devices. Network configurations vary with carriers and Wi-Fi networks.
- Use Developer Profiles and Permissions: Physical devices need appropriate development provisioning profiles to allow debugging and network inspection.
Best Practices for Network Interception
Follow these best practices to ensure effective and secure network interception during testing:
- Use Non-Production Builds Only: Intercept traffic only on development, staging, or testing builds to protect user data and avoid disrupting live services.
- Manage CA Certificates Carefully: Install and trust CA certificates only on devices or simulators under your control and remove them immediately after testing to reduce security risks.
- Filter Traffic by App or Domain: Apply filters based on app bundle identifiers, domains, or specific endpoints to focus on relevant network requests and improve analysis speed.
- Coordinate SSL Pinning Handling: Work with developers to disable SSL pinning in test builds rather than bypassing it on production apps to maintain security standards.
- Document Proxy Settings: Keep clear records of proxy IP addresses, ports, and installed certificates to ease troubleshooting and support team collaboration.
- Protect Sensitive Data: Monitor intercepted traffic for sensitive information such as passwords and tokens. Follow privacy policies and avoid unnecessary data storage.
- Restart After Configuration Changes: Reboot devices, simulators, and proxy tools after any changes to ensure new settings take effect and prevent unexpected issues.
Conclusion
Network interception helps developers and testers identify network request and response issues early. Properly setting up simulators, proxies, and certificates is essential to ensure accurate and effective interception.
Requestly helps developers capture, modify, and monitor network traffic from the iOS simulator with ease. It offers proxy configuration, SSL certificate management, and traffic filtering to streamline debugging.