Authentication flows are essential for any application, and testing them thoroughly is critical to ensure security and proper access control. Mock APIs provide a safe and flexible way to test these flows without relying on live systems.
Overview
What Is a Mock API for Authentication Testing?
A Mock API for Authentication Testing is a simulated version of authentication endpoints that allows developers and testers to verify login, logout, token validation, and permission checks in a controlled environment.
Key Aspects of a Mock API for Authentication Testing
Here are the main aspects that make mock APIs effective for authentication testing:
- Simulates Login/Logout: Replicates the authentication process, allowing tests of login and logout flows without connecting to the live backend.
- Handles Different User Scenarios: Supports testing for various user roles, permissions, and account states to ensure all conditions are covered.
- Controls Response Data: Enables customization of API responses, including tokens, user details, and session information, for precise testing scenarios.
- Simulates Error Conditions: Allows testing of failed logins, expired tokens, and unauthorized access responses to verify error handling.
- Facilitates Parallel Development: Provides a stable environment for front-end and back-end teams to work simultaneously without dependency on live services.
Tools for Mock API for Authentication Testing
- Requestly: A browser extension to create mock APIs and modify request and response data.
- Postman: A platform to design and run mock endpoints for authentication flows.
- Apidog: A service to build and manage mock APIs with support for different user roles.
- Hoverfly: An API virtualization tool to simulate real authentication API behavior.
This article explains how a mock API for authentication testing works, how to set it up, advanced scenarios, limitations, and best practices.
Understanding Mock API for Authentication Testing
A mock API for authentication testing replicates the behavior of real authentication endpoints in a controlled environment. It allows developers and testers to simulate login, logout, token validation, and permission checks without depending on the live backend.
This makes it possible to test different scenarios reliably, handle edge cases, and verify how applications respond to various API behaviors.
Below are the main functions a mock API performs in authentication testing:
- Simulates Authentication Flows: Handles login, logout, and session validation just like a real API.
- Generates Custom Responses: Provides configurable responses, including tokens, user details, and session information.
- Tests Error Handling: Simulates failed logins, expired tokens, and unauthorized access scenarios.
- Supports Role-Based Testing: Allows testing for different user roles and permission levels.
- Enables Parallel Development: Lets front-end and back-end teams work independently by providing a stable API environment.
Why Use Mock APIs for Authentication Testing?
API mocking provides several benefits that make authentication testing safer, faster, and more flexible. By simulating authentication endpoints, teams can test without risking sensitive data or relying on unstable backend services. They also help identify issues early in development and support scenarios that are difficult to reproduce on live systems.
Key advantages of using mock APIs for authentication testing include:
- Reduces Dependency on Backend: Test authentication flows even if the backend is incomplete or unstable.
- Improves Test Coverage: Easily simulate different users, roles, and error conditions.
Read More: How to ensure Maximum Test Coverage?
- Speeds Up Development: Front-end and back-end teams can work in parallel without waiting for live endpoints.
- Ensures Consistent Testing: Provides predictable responses for repeated tests and automated test suites.
- Supports Risk-Free Testing: Avoids testing with real credentials or live systems, reducing security risks.
How Does Mock API for Authentication Work?
A mock API works by intercepting requests that would normally go to the live authentication server and responding with simulated data. When the application sends a login or token validation request, the mock API checks the request against preconfigured rules and returns a response that mimics the real API.
This allows developers and testers to control what data is returned and test different authentication scenarios safely.
Here is the step-by-step working process:
- Request Interception: The application sends a request to the mock API instead of the real server.
- Request Evaluation: The mock API checks the request type, credentials, or tokens against pre-set rules.
- Response Generation: Based on the rules, it returns a response such as a success message, token, user data, or an error.
- Scenario Simulation: Different responses can be configured to test roles, permissions, and error conditions.
- Integration with Tests: Automated tests can use these mock responses to verify application behavior consistently.
Top Tools for Mock API Authentication Testing
Here are the five best tools for mocking API for authentication testing.
1. Requestly by BrowserStack
Requestly is an open-source HTTP interceptor and API client designed to assist developers in testing, mocking, and debugging APIs. It enables the interception and modification of HTTP requests and responses, facilitating the simulation of various scenarios without the need for backend changes.
Key Features of Requestly:
- Modify API Responses: Simulate authentication tokens, user roles, and session data.
- Mock Login/Logout Endpoints: Create mock endpoints to test login and logout functionalities.
- Simulate Error Conditions: Mimic failed logins, expired tokens, and unauthorized access scenarios.
- Modify Request Headers: Adjust headers to test various authentication scenarios.
- Cross-Device Testing: Test authentication flows across different devices and platforms.
Why Choose Requestly:
- Open Source: Free to use and customizable to fit specific needs.
- Comprehensive Toolset: Combines API client, HTTP interceptor, and mocking capabilities in one platform.
- Cross-Platform Support: Works on various platforms, including browsers and desktop applications.
- Collaborative Features: Facilitates teamwork through shared workspaces and team collaboration tools.
- Extensive Documentation: Provides detailed guides and resources to assist users in utilizing the tool effectively.
Pricing:
- Free: Access to basic features for individual use.
- Lite: $8/member/month
- Basic: $15/member/month
- Professional: $23/member/month
2. Postman
Postman is a widely used API platform for designing, testing, and mocking APIs. It allows developers and testers to create mock endpoints for authentication flows, simulate responses, and automate testing without relying on a live backend.
Key Features of Postman:
- Create mock servers to simulate authentication APIs
- Use built-in authorization helpers for OAuth 2.0, API keys, and other methods
- Manage authentication tokens and credentials using environment variables
- Define and save mock responses for authentication endpoints
Pros and Cons of Postman:
| Pros | Cons |
|---|---|
| Extensive support for various authentication methods | Can be overwhelming for beginners |
| Robust community and documentation | Some advanced features require a paid plan |
| Supports automated testing and CI/CD integration | May require significant system resources |
3. Apidog
Apidog is a platform for building and managing mock APIs. It is suitable for testing authentication endpoints, simulating user roles, and defining custom responses to validate different scenarios.
Key Features of Apidog:
- Create mock servers to simulate authentication APIs
- Define expected behaviors for authentication endpoints
- Run tests on mocked authentication APIs
- Share mock authentication APIs with team members
Pros and Cons of Apidog:
| Pros | Cons |
|---|---|
| User-friendly interface | Limited integrations with other tools |
| Supports automated testing and CI/CD pipelines | Smaller community compared to other tools |
| Offers collaborative features | Some advanced features may require additional setup |
4. Hoverfly
Hoverfly is an API virtualization tool that simulates real API behavior, including authentication endpoints. It is suitable for complex testing scenarios and supports parallel development between front-end and back-end teams.
Key Features of Hoverfly:
- Simulate real authentication APIs based on recorded interactions
- Create dynamic mocks for different authentication scenarios
- Intercept and modify authentication requests and responses
- Preserve exact response patterns and headers from recorded interactions
Pros and Cons of Hoverfly:
| Pros | Cons |
|---|---|
| High-fidelity simulation of authentication APIs | Requires initial setup and configuration |
| Supports dynamic and complex mocking scenarios | Steeper learning curve |
| Integrates well with CI/CD pipelines | Smaller community and support resources |
Step-by-Step Guide: Setting Up a Mock API for Authentication Testing
Setting up a mock API for authentication testing allows developers and testers to simulate login, logout, token validation, and user roles without depending on a live backend. Requestly enables frontend developers to test authentication flows independently and ensures that automated tests run consistently.
Here is how to set up a Mock API for authentication testing using Requestly:
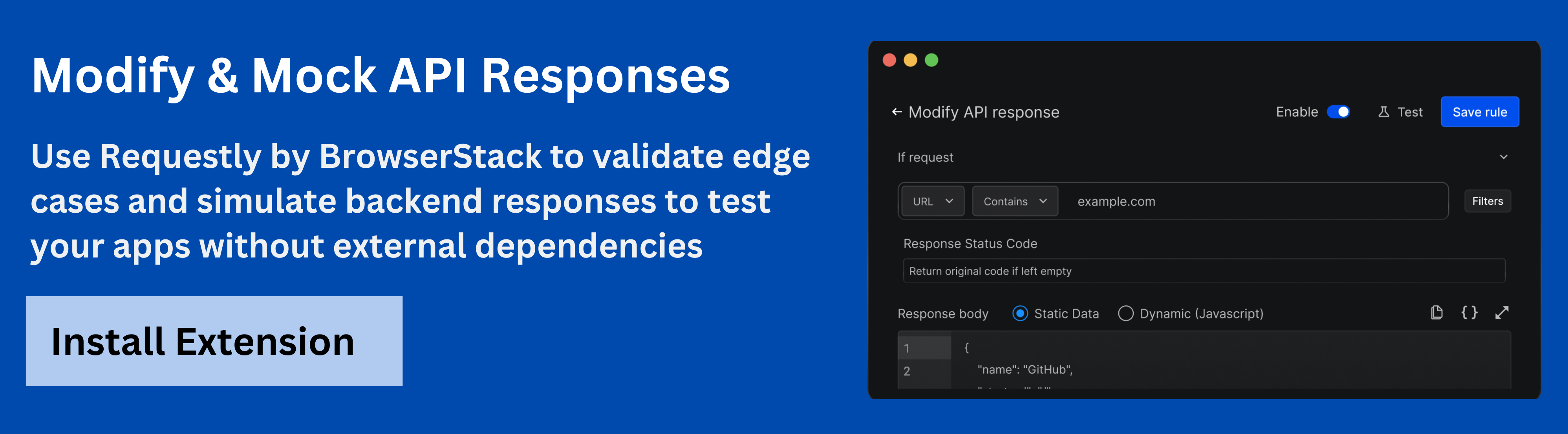
- Download Requestly either via extension for Chrome or Firefox, or the desktop app for more advanced traffic interception.
- Open the Requestly dashboard and navigate to HTTP Rules. Click New Rule and select Modify API Response.
- Set the URL pattern to match your authentication endpoint, such as https://yourapi.com/login.
- Configure the response status code (200 for success, 401 for failed login) and provide a JSON response simulating a real authentication response, including tokens, user details, and roles.
- Optionally, add headers like Content-Type: application/json.
- Save and enable the rule to start intercepting requests and returning the mocked responses.
- Test the mock API by initiating login requests from your application and verifying that the frontend handles the mocked authentication data correctly.
- Create additional rules to simulate scenarios like invalid credentials, expired tokens, or unauthorized access.
- Once the backend authentication is ready, disable or delete the mock rules to switch to the live API.
Advanced Mock API Scenarios for Authentication Testing
Mock APIs allow teams to test authentication flows beyond basic login and logout. Advanced scenarios help identify edge cases, validate role-based access, and ensure frontend and backend behavior aligns even before backend endpoints are fully developed.
Each scenario below explains why it matters and shows how to implement it.
1. Simulating Multiple User Roles
Testing different user roles ensures that access controls and permissions are enforced correctly. For example, an admin may have full access, while a regular user can only read data. By mocking responses for each role, developers can:
- Validate that restricted actions are blocked for non-admin users.
- Ensure the frontend displays the correct options based on role.
- Test conditional features without needing a live backend.
To implement this, create separate mock responses for the /login endpoint with different role attributes. Example response for an admin user:
{
"token": "admin-token",
"user": {
"id": "1",
"role": "admin",
"permissions": ["read", "write", "delete"]
}
}2. Token Expiration and Refresh Flows
Handling token expiration is critical to securing applications. By mocking expired tokens and refresh flows, developers can ensure:
- Frontend requests are properly rejected when tokens expire.
- Token refresh mechanisms are correctly triggered.
- Users are redirected to login or notified appropriately.
To implement this, return a 401 Unauthorized response with an error indicating token expiration:
{
"error": "token_expired",
"message": "The access token has expired"
}Then, create a mock refresh endpoint that returns a new valid token to test session renewal.
3. Failed Login Attempts
Simulating incorrect credentials or locked accounts ensures that:
- Security measures like account lockouts are functioning.
- Users receive accurate feedback.
- Frontend prevents further actions until successful authentication.
To implement this, return a 401 response for invalid credentials:
{
"error": "invalid_credentials",
"message": "The username or password is incorrect"
}Read More: How to Write Test Cases for Login Page
4. Permission Errors
Testing endpoints for permission restrictions ensures sensitive actions are not accessible to unauthorized users. This prevents accidental data leaks or unauthorized modifications.
To implement this, mock 403 Forbidden responses for restricted endpoints:
{
"error": "forbidden",
"message": "You do not have permission to access this resource"
}5. Network and Server Errors
Testing authentication under network failures or server errors ensures resilience and proper user feedback. Developers can check:
- Retry mechanisms
- Error messages displayed to users
- Application stability under intermittent failures
To implement this, mock delayed responses, 500 Internal Server Error, or network timeouts:
{
"error": "server_error",
"message": "Something went wrong, please try again later"
}6. Conditional Responses Based on Input
Some authentication flows depend on specific input, like a banned account or multi-factor requirements. Testing these ensures the correct handling of edge cases.
To implement this, return different responses depending on the request body or query parameters. For example, a banned user attempting to log in can return:
{
"error": "account_banned",
"message": "Your account has been suspended"
}Limitations of Mock APIs in Authentication Testing
While mock APIs are useful for testing authentication flows, they have inherent limitations that teams must be aware of. Below are the key limitations:
- No Real Backend Enforcement: Mock APIs do not enforce actual authentication or authorization rules. They simulate responses, so while the frontend reacts as expected, the real backend might behave differently. Tests relying solely on mocks cannot catch security or logic issues in the server.
- Limited Data Variability: Mocks often use static responses or predefined scenarios. This means unexpected edge cases or data combinations present in the real backend might not be tested, potentially missing critical bugs.
- Cannot Test Performance Under Load: Mock APIs do not replicate real network latency, concurrency, or backend processing delays. Tests for response times, server load, or scaling behavior require a real backend or a specialized performance testing environment.
- Partial Simulation of Complex Workflows: Advanced authentication flows, such as multi-factor authentication, account recovery, or third-party OAuth integrations, may be difficult to simulate fully with mocks. Mocking these may only cover basic success or error responses.
- Risk of False Confidence: Relying heavily on mock APIs can give a false sense of security. Passing all mock tests does not guarantee that the frontend will work correctly with the live backend or under production conditions.
- Maintenance Overhead: As backend APIs evolve, mock responses must be updated accordingly. Outdated mocks can cause tests to pass incorrectly or fail unnecessarily, leading to additional maintenance effort.
Best Practices for Mock API Authentication Testing
Using mock APIs effectively requires following certain best practices to ensure tests remain reliable, realistic, and maintainable. Below are key practices to consider:
- Define Clear Scenarios: Identify all critical authentication scenarios, including login, logout, token expiration, role-based access, failed logins, and error handling. This ensures coverage of both common and edge cases.
- Keep Mock Responses Realistic: Simulate actual backend responses as closely as possible, including status codes, JSON structures, and error messages. This helps the frontend and automated tests behave as they would in production.
- Use Conditional Responses: Configure mocks to return different responses based on request data, such as user roles, input values, or account status. This allows testing of dynamic behavior without a live backend.
- Integrate with Automated Tests: Include mock API scenarios in automated test suites to consistently verify frontend behavior across builds, deployments, and feature changes.
- Test Both Success and Failure Cases: Ensure mocks cover valid logins, failed logins, token expirations, unauthorized access, and network errors. Testing only success scenarios can hide potential issues.
- Document Mock Scenarios: Keep a clear record of all mock endpoints, their responses, and the scenarios they cover. This makes it easier for new team members to understand test coverage and reduces maintenance effort.
Conclusion
Mock APIs allow teams to test authentication flows by simulating login, logout, token management, and error conditions without relying on a live backend. They help developers and testers identify edge cases, enforce role-based access, and ensure the frontend behaves according to authentication rules.
Requestly allows developers to create mock endpoints, return different responses based on user roles or input, simulate expired tokens, and trigger error conditions. By configuring these scenarios, teams can test authentication flows thoroughly and verify frontend behavior without waiting for the backend.