HTTP is the protocol that powers communication between clients and servers on the web. Every webpage, API call, or mobile app interaction starts with an HTTP request.
Overview
What is an HTTP Request
An HTTP request is a structured message sent by a client, such as a browser, mobile app, or backend service, to a server to perform an action. This action could be retrieving data, submitting input, updating a record, or deleting a resource.
Structure of an HTTP Request:
An HTTP request follows a defined format, allowing the server to understand what the client wants and how it wants it.
- Request line: Contains the method (e.g., GET), the target URL, and the HTTP version
- Headers: Provide metadata like content type, authentication, or accepted response formats
- Body: Optional section used mainly with methods like POST and PUT to send data
- Query parameters: Key-value pairs in the URL used to filter or customize the request
Common HTTP Request Methods:
Each method tells the server what action the client wants to perform.
- GET: Retrieve data without modifying anything
- POST: Submit data to the server, often creating a new resource
- PUT: Replace an existing resource with new data
- PATCH: Partially update an existing resource
- DELETE: Remove a resource from the server
- HEAD: Same as GET, but returns only headers
- OPTIONS: Describes allowed methods for a resource
This article explains how HTTP requests work, how they are structured, how different methods behave, what changed with HTTP/2 and HTTP/3, and how to use them effectively and securely.
What is an HTTP Request?
An HTTP request is a message sent from a client to a server over the Hypertext Transfer Protocol (HTTP). It acts as the primary means by which a client requests information, performs actions, or interacts with a server.
When a user accesses a webpage, submits a form, or interacts with a web service, an HTTP request is generated. The client could be a web browser, a mobile application, a backend system, or even a third-party service.
The request typically contains several key components: the HTTP method (e.g., GET, POST), the resource identifier (usually a URL), headers (containing metadata such as content type and authentication), and occasionally a body (for sending data).
Read More: Life Cycle of an HTTP Request
Why are HTTP Requests Important?
HTTP requests are central to web communication and are the mechanism by which data is transferred between clients and servers. Understanding HTTP requests is critical for developers and system administrators alike for several reasons:
- Web Application Functionality: HTTP requests are used to load resources such as HTML pages, images, scripts, and stylesheets. They also handle actions like logging in, submitting forms, or making API calls.
- Security: The structure of an HTTP request is crucial for ensuring secure communication between clients and servers. Headers like “Authorization” and “Content-Type” help authenticate users, ensure the integrity of data, and prevent malicious attacks such as Cross-Site Scripting (XSS) or SQL injection.
- Optimization and Performance: Understanding the types of HTTP requests (e.g., GET vs. POST) can impact performance. For instance, caching strategies for GET requests can make applications faster, while efficient data handling in POST or PUT requests can reduce server load.
- Error Handling and Debugging: Identifying issues with HTTP requests (e.g., incorrect HTTP methods, improper headers, or malformed URLs) can be essential in debugging application errors.
How HTTP Requests Work
An HTTP request follows a defined flow, consisting of several key components that tell the server how to process the client’s request:
1. Request Line
The first part of the request defines the action the client wants to take. It includes:
- HTTP Method: This indicates what action the client wants the server to perform, such as GET (retrieve data), POST (send data), PUT (update data), or DELETE (remove data).
- Request URI: The Uniform Resource Identifier (URI) is a path or resource that the client is requesting, typically represented as a URL (e.g., /users, /products/123).
- HTTP Version: The version of HTTP being used for the request (e.g., HTTP/1.1 or HTTP/2).
2. Headers
They provide additional context to the server. Common headers include:
- Content-Type: Specifies the type of data being sent (e.g., application/json, text/html).
- Authorization: Used for authentication, such as passing a token or API key.
- User-Agent: Identifies the client (browser or application) making the request.
- Accept: Tells the server what type of responses the client can handle (e.g., text/html, application/json).
3. Body
If the HTTP method is one that involves sending data (e.g., POST, PUT), the body of the request contains the actual data being transmitted. This can be in various formats, such as JSON, XML, or form data.
Read More: What are API Headers and Body?
4. Query Parameters
These are optional but commonly included in URLs to filter or modify the request. For example, a URL like /products?category=books&sort=price contains query parameters (category=books, sort=price) that modify the request.
Once the request reaches the server, the server processes it based on the method, headers, and body content. It then sends back a response, which typically includes HTTP status codes (e.g., 200 for success, 404 for not found) and the requested data or confirmation of the action taken.
The server interprets each component of the HTTP request to deliver the appropriate response, ensuring that clients receive what they asked for or are informed of any issues with the request.
HTTP/2 and HTTP/3: What’s New?
HTTP/2 and HTTP/3 represent significant updates to the original HTTP/1.1 protocol, aiming to improve web performance, reduce latency, and address some limitations that arose from how HTTP/1.1 handled requests.
HTTP/2:
HTTP/2 introduced several key features over HTTP/1.1 that significantly improved web performance:
- Multiplexing: Multiple requests and responses can be sent simultaneously over a single connection, rather than waiting for one to finish before sending the next (which was a limitation in HTTP/1.1). This reduces latency and improves load times.
- Header Compression: HTTP/2 uses a more efficient mechanism for compressing headers, reducing the overhead of repeated header fields.
- Stream Prioritization: Clients can assign priority to different streams, allowing more important resources (like critical JavaScript or CSS) to be delivered faster.
- Server Push: Servers can push resources to the client before they’re requested, anticipating what the client will need, which can further speed up the loading process.
HTTP/3:
HTTP/3 builds upon HTTP/2’s improvements but goes a step further with a new transport protocol called QUIC (Quick UDP Internet Connections), replacing TCP with UDP. The main benefits of HTTP/3 include:
- Faster Connection Establishment: QUIC reduces the handshake time significantly compared to TCP, allowing for faster connections, especially on networks with high latency.
- Improved Performance on Mobile Networks: QUIC, and therefore HTTP/3, is designed to handle network changes and packet loss better, making it ideal for mobile devices where network conditions may fluctuate.
- Multiplexing and Stream Management: While HTTP/2 allows multiplexing, HTTP/3 improves this further with QUIC’s connection management, ensuring better handling of congestion and packet loss.
Here’s a table summarizing the differences between HTTP/2 and HTTP/3:
| Feature | HTTP/2 | HTTP/3 |
|---|---|---|
| Transport Protocol | TCP (Transmission Control Protocol) | QUIC (Quick UDP Internet Connections) |
| Multiplexing | Yes, multiple requests over one connection. | Yes, better with reduced head-of-line blocking. |
| Connection Establishment | Slower, multiple round trips required. | Faster, with fewer round trips due to QUIC. |
| Header Compression | HPACK for headers. | QPACK, more efficient and avoids blocking. |
| Packet Loss Recovery | Retransmits lost packets, causing delays. | Faster recovery without blocking other packets. |
| Server Push | Yes, sends resources before requested. | Yes, more efficient with QUIC. |
| Security | TLS 1.2 or 1.3 | Always TLS 1.3, more consistent security. |
| Performance on Mobile | Good, but still affected by packet loss. | Better, designed for mobile and unstable networks. |
| Compatibility | Widely supported. | Needs QUIC support, not universally adopted. |
| Speed | Faster than HTTP/1.1, but still TCP-limited. | Faster, especially on high-latency networks. |
HTTP Request Methods (Verbs)
HTTP methods, often called “verbs,” define the type of action that the client wants to perform on the server. These methods are critical for structuring requests and understanding what operation the client is requesting. Below are the most commonly used HTTP methods:
- GET: The GET method retrieves data from the server. It is the most common HTTP method and is used when a client wants to fetch resources, such as HTML pages, images, or API responses. GET requests should be idempotent, meaning they should not alter the server’s state.
- POST: The POST method is used to send data to the server. It is typically used for submitting forms, uploading files, or creating resources. Unlike GET, POST requests may alter the server’s state (e.g., creating a new record in a database).
- PUT: PUT is used to update or replace an existing resource on the server. When a PUT request is made, the resource at the specified URL is replaced with the new data provided in the request. PUT is idempotent, meaning repeating the same PUT request will have the same effect.
- PATCH: PATCH is used to apply partial modifications to a resource. Unlike PUT, which replaces the entire resource, PATCH allows updating only specific fields or parts of the resource. It is particularly useful when updating large resources where only a small change is required.
- DELETE: The DELETE method is used to remove a resource from the server. When a client sends a DELETE request, the server removes the specified resource. DELETE requests should also be idempotent.
- HEAD: HEAD is similar to GET, but it only requests the headers of a resource, not the body. It is useful for checking metadata (such as content length or type) without downloading the full resource.
- OPTIONS: OPTIONS is used to retrieve the allowed methods and operations that the server supports for a specific resource. It is often used to determine what actions can be performed on a resource without performing any actual operations.
HTTP methods are often categorized into three important behaviors: safe, idempotent, and cacheable. These attributes help developers understand how requests can be used without unintended side effects and optimize how servers handle requests.
Here’s a table summarizing the differences between safe, idempotent, and cacheable HTTP methods:
| Attribute | Safe Methods | Idempotent Methods | Cacheable Methods |
|---|---|---|---|
| Definition | Methods that do not modify server state. | Methods that can be repeated with the same result. | Methods whose responses can be stored for reuse. |
| Example Methods | GET | PUT, DELETE, GET | GET |
| Impact on Server | No change to the server’s state. | The result is the same regardless of how many times the request is repeated. | Responses can be stored and reused, reducing the need for repeated requests. |
| Behavior | Read-only operations. | Operations that can be repeated without side effects. | Responses are stored in cache for performance. |
| Common Use | Retrieving resources like pages or data. | Modifying or deleting resources in a consistent way. | Fetching resources where repeated calls can be optimized. |
| Can Repeat Requests Without Side Effects? | Yes | Yes | Yes |
| Example | GET: Fetching a webpage. | PUT: Updating a user profile. | GET: Fetching an image or JSON data. |
Key Differences Between HTTP Request Methods: GET vs POST
When working with HTTP requests, understanding the difference between GET and POST is crucial, as these are the most commonly used methods. Both are essential for different use cases, and their proper usage ensures that web applications and APIs function smoothly.
Here’s a table outlining the key differences between GET and POST HTTP request methods:
| Feature | GET | POST |
|---|---|---|
| Purpose | Retrieve data from the server | Send data to the server to create or update a resource |
| Impact on Server | Does not modify server state | Can modify server state (e.g., creating/updating resources) |
| Idempotent | Yes, it can be repeated without side effects | No, repeated requests can result in different outcomes |
| Cacheable | Yes, responses can be cached | No, responses are not cached |
| Data Transmission | Data sent via URL (query parameters) | Data sent in the body of the request |
| Data Size | Limited by URL length (generally around 2,000 characters) | Can send large amounts of data (no strict limit) |
| Security | Less secure, data visible in URL | More secure for sensitive data (data in body) |
| Use Case | Fetching resources like HTML, images, etc. | Form submissions, uploading files, and sending sensitive data |
| Example | GET /users?id=123 | POST /submit-form |
Read More: HTTP Methods: GET vs POST vs PUSH
Understanding and Using HTTP Headers
Headers are essential for the proper functioning of HTTP requests and responses. HTTP headers contain metadata that informs the server about the client’s request or tells the client about the server’s response.
Headers are divided into several categories, each with a specific purpose:
1. General Headers: These headers provide additional information that isn’t specific to the request or response itself but applies to both.
Example: Cache-Control indicates caching policies, while Connection controls whether the connection should be kept alive or closed.
2. Request Headers: These headers are sent with the HTTP request and provide additional details about the client or the request itself.
Example:
- User-Agent: Identifies the client making the request (e.g., browser or app).
- Authorization: Contains credentials for authentication (e.g., API key or token).
3. Response Headers: These headers are returned by the server and provide details about the server’s response, such as the type of content being returned or any caching instructions.
Example:
- Content-Type: Specifies the media type of the resource (e.g., application/json, text/html).
- Location: Used in redirect responses to indicate the new URL for the resource.
4. Entity Headers: These are used to describe the body of the resource.
Example:
- Content-Length: Specifies the size of the response body.
- Content-Encoding: Describes the encoding used (e.g., gzip).
5. Custom Headers: Some applications may use custom headers to convey specific information between the client and server.
Example: A custom header like X-Request-ID can be used to track the request through the backend.
How to Use HTTP Headers Effectively
Here’s a step-by-step process to effectively use HTTP headers in your application:
1. Identify the Purpose of the Header
Each HTTP header serves a specific role, so it’s essential to identify the exact purpose before implementing. Common types of headers include:
- General Headers: Apply to both request and response (e.g., Cache-Control, Connection).
- Request Headers: Provide information about the client or request itself (e.g., User-Agent, Authorization).
- Response Headers: Inform the client about the server’s response (e.g., Content-Type, Location).
- Entity Headers: Describe the body of the resource (e.g., Content-Length, Content-Encoding).
2. Set Cache-Control for Performance Optimization
Caching is a powerful performance tool for reducing server load and speeding up response times. By using appropriate cache-related headers, you can ensure that resources are cached and reused efficiently.
For example:
- To cache a resource for one hour, set: Cache-Control: max-age=3600
- To disable caching for sensitive data: Cache-Control: no-store
Using the Cache-Control header correctly ensures that frequently accessed data is cached, reducing load times and bandwidth usage, while also protecting sensitive data from being cached improperly.
Ensure Security with Authentication and Authorization Headers
Authentication and authorization headers control access to your resources. By setting these headers properly, you can secure endpoints and ensure only authorized users can access specific data.
For example:
- For API access, use the Authorization header to pass an API token: Authorization: Bearer <token>
- To enforce SSL (HTTPS), use the Strict-Transport-Security (HSTS) header:
Strict-Transport-Security: max-age=31536000; includeSubDomains
Using authentication headers like Authorization properly ensures secure access to APIs, while headers like Strict-Transport-Security enforce secure connections.
4. Use Content-Type and Accept for Proper Content Negotiation
Content negotiation between the client and server determines how resources are represented. The Content-Type header specifies the type of data being sent to the server (e.g., JSON, HTML), and the Accept header tells the server what kind of response the client expects.
For example:
- For sending JSON data, set: Content-Type: application/json
- For requesting a JSON response from the server: Accept: application/json
By using Content-Type and Accept headers effectively, you ensure that the data sent and received is in the expected format, allowing proper handling and processing by both the client and the server.
5. Implement Cross-Origin Resource Sharing (CORS)
If your server needs to allow access from different domains (e.g., in the case of a web API), you need to configure Cross-Origin Resource Sharing (CORS) headers. These headers specify which origins can access your resources.
For example:
- To allow any domain to access your API: Access-Control-Allow-Origin: *
- To restrict access to a specific domain: Access-Control-Allow-Origin: https://example.com
6. Set Content-Security-Policy (CSP) for Security
A strong Content-Security-Policy (CSP) header helps protect your site from cross-site scripting (XSS) and other code injection attacks by controlling where resources (e.g., scripts, images) can be loaded from.
For example, to only allow scripts from your own domain:
- Content-Security-Policy: script-src ‘self’
7. Use Custom Headers for Application-Specific Data
Custom headers can be used to pass data specific to your application, such as tracking information or request IDs. These headers are particularly useful for logging, debugging, and monitoring.
For example:
- For tracking a specific request or session: X-Request-ID: 12345
- For logging purposes: X-Client-Version: 1.2.3
Custom headers can be used for various purposes, including analytics, logging, and debugging, ensuring that important data is passed along with each request or response.
Working with the HTTP Request Body
Using the request body is essential when dealing with data that goes beyond simple parameters in the URL, such as complex JSON objects or file uploads.
In HTTP requests, the body contains the data being sent to the server. Unlike GET requests, which append data in the URL or via query strings, methods like POST, PUT, and PATCH utilize the request body to send data. The body is used for larger or more complex payloads, such as submitting form data, uploading files, or updating resources.
- POST, PUT, and PATCH allow clients to send data like user input, file uploads, or updates, and this data is carried in the request body.
- Content Types: The body’s format is specified by the Content-Type header. Common types include:
- application/json for structured data like JSON.
- application/x-www-form-urlencoded for traditional form submissions.
- multipart/form-data for handling file uploads.
Using URL Parameters and Query Strings
While the request body is used for larger, more complex data, URL parameters and query strings allow for sending smaller amounts of data directly in the URL itself. These are often used in GET requests, where clients fetch specific resources or apply filters.
- URL Parameters: These are embedded directly in the URL path and typically represent identifiers for resources. For example, /users/123 might fetch details for a specific user with ID 123.
- Query Strings: These are appended after the ? in the URL and consist of key-value pairs. They are commonly used for sorting, filtering, or pagination. For example, /search?query=laptop&sort=price uses query parameters to filter search results for “laptop” and sort them by price.
Both URL parameters and query strings are lightweight methods for passing data when requesting resources without the need for a body, making them ideal for retrieving information or making minor adjustments to the query.
Debugging and Troubleshooting HTTP Requests
When working with HTTP requests, especially in web development or API integration, issues are bound to arise. Here’s a step-by-step guide to help diagnose and resolve issues with HTTP requests.
1. Check the HTTP Status Code
Start by examining the HTTP status code in the response. This is a clear indicator of the outcome of the request:
- 2xx: Success (e.g., 200 OK, 201 Created)
- 4xx: Client error (e.g., 400 Bad Request, 404 Not Found)
- 5xx: Server error (e.g., 500 Internal Server Error)
The status code can immediately point you to the type of issue you’re dealing with. For example, a 404 status typically means the resource doesn’t exist, while a 500 indicates a server-side issue.
2. Examine the Request and Response Headers
HTTP headers often contain useful information about what’s happening with the request or response. These headers can tell you if authentication is failing, if data types are mismatched, or if the client is making a request in an unexpected format.
- Request Headers: Ensure headers like Content-Type, Authorization, and Accept are set correctly, as they affect how the request is processed by the server.
- Response Headers: Pay attention to headers like Cache-Control, Content-Type, and Location, which can help clarify issues with data formatting, redirection, or caching.
3. Verify the Request Method
Make sure you’re using the correct HTTP method for the desired action. For example, trying to update a resource with a GET request will lead to issues because GET is intended for retrieving data, not modifying it.
4. Check for URL and Path Issues
Incorrect URLs or path parameters are a common cause of failed HTTP requests. Double-check the following:
- Ensure that the base URL is correct.
- Verify that any path parameters or query strings are properly formatted.
- Pay attention to case sensitivity in paths or parameter names.
For instance, /users/123 is different from /users/123/, and a missing parameter could cause a 400 or 404 error.
5. Inspect the Request Body
If the HTTP method involves sending data (e.g., POST, PUT, PATCH), make sure the request body is formatted correctly.
- Check Content-Type: Ensure that the content type in the header (e.g., application/json) matches the format of the body.
- Validate Data: Double-check that the data sent in the body adheres to the expected structure, especially for APIs expecting JSON or XML payloads.
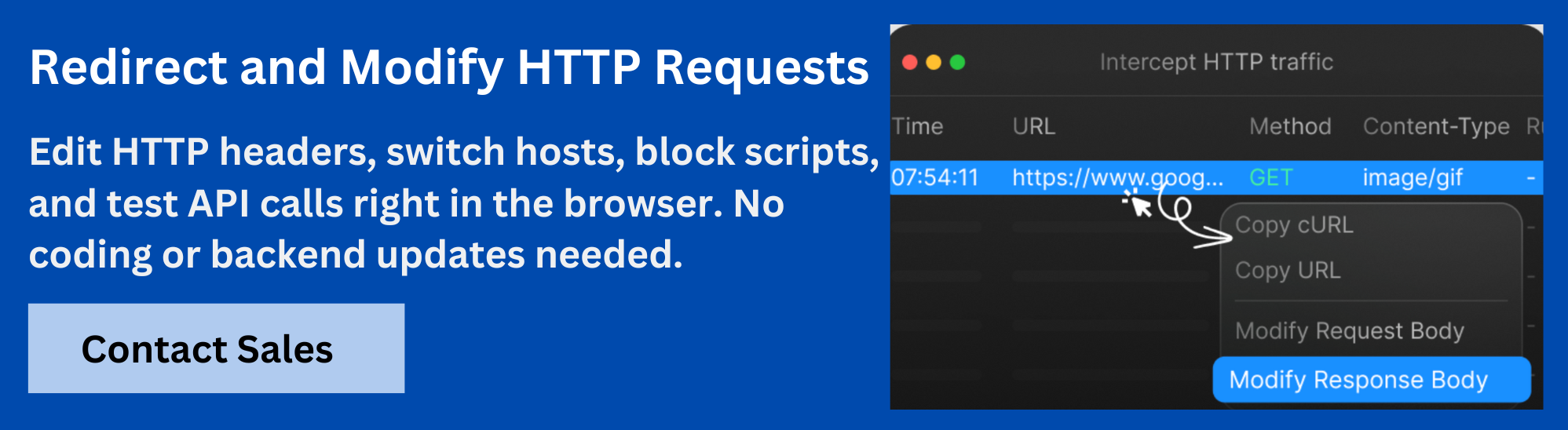
How Requestly Helps Test HTTP Requests?
Requestly by BrowserStack is a powerful browser extension that simplifies the process of debugging and troubleshooting HTTP requests. It allows you to intercept, modify, and log requests and responses in real-time, making it much easier to identify and fix issues with web requests.
Here’s how you can leverage Requestly in your debugging workflow:
- Modify HTTP Headers: Modify HTTP request and response headers in real-time without needing to alter the server code.
- Mock API Responses: Simulate various server responses (errors, delays, data) for testing purposes.
- View Detailed Logs: Inspect request and response details like status codes, headers, and bodies.
- Test CORS Configurations: Modify or add CORS headers to test cross-origin resource sharing.
- Redirect URLs: Redirect requests to different URLs or mock servers for testing different scenarios.
Conclusion
HTTP requests are fundamental to how clients and servers interact, determining how data is sent, retrieved, or manipulated. The structure of these requests, such as the method used, the headers, the body, and URL parameters, directly influences the functionality and efficiency of web applications and APIs.
If you’re a developer or a tester, Requestly simplifies debugging and testing HTTP requests. It lets you modify requests and responses in real-time. You can manage headers, mock responses, and simulate scenarios without altering server-side code. This speeds up troubleshooting and enhances the efficiency of web development and testing.