Many applications today rely on proxies, Content Delivery Networks (CDNs), and load balancers to improve performance and scalability. While these tools help deliver content quickly and efficiently, they can sometimes hide crucial client request data. Without this information, it becomes difficult to troubleshoot issues or enforce security measures effectively.
This is where X-Forwarded headers come into play. These custom HTTP headers preserve key details about the original request, allowing servers to identify the true source, even if the request passes through several layers of infrastructure.
What is X-Forwarded-For (Client IP)? Captures the original client IP as a request traverses proxies. What is X-Forwarded-Host (Original Host)? Preserves the Host header the client sent before any proxy changes. What is X-Forwarded-Proto (Protocol: HTTP/HTTPS)? Indicates whether the client’s original request used HTTP or HTTPS. Overview
This article delves deep into X-Forwarded headers and why it is used.
What are X-Forwarded Headers?
X-Forwarded headers are a set of custom HTTP headers used to pass along important information about a client’s request, even when it has been routed through one or more intermediary services like proxies, load balancers, or CDNs. These headers help maintain visibility of the original request data, which would otherwise be hidden by these intermediary layers.
By using X-Forwarded headers, servers can access the true source of the request-whether it’s the client’s IP address, the protocol used, or the host value. These headers make it possible for web applications to handle requests accurately, apply security rules, and troubleshoot issues that may arise due to hidden client data.
Common X-Forwarded Headers Explained
There are several X-Forwarded headers commonly used to preserve important client request information.
Some of the most common ones are:
X-Forwarded-For – Client’s IP Address
Description:
The X-Forwarded-For header carries the original IP address of the client making the request. This is crucial when requests pass through multiple proxies or load balancers, as each proxy may alter the client’s IP address, making it hard to track the true source of the request.
Syntax:
X-Forwarded-For: clientIP, proxy1IP, proxy2IP
In the syntax, clientIP represents the original client’s IP address, followed by the IPs of any proxy servers that handled the request. Each proxy appends its IP to the list, preserving the chain of intermediaries the request passed through.
Use Cases:
Identifying the true client IP: When a request is routed through proxies or CDNs, the original client’s IP is often lost. X-Forwarded-For ensures that the original IP is passed along, which is important for logging, analytics, and security.
- Geolocation-based decisions: The client’s IP address can be used to identify the geographical location of the request, enabling features like geo-blocking, region-specific content delivery, or local laws compliance.
- Rate limiting: By tracking the true client IP, you can apply rate-limiting measures, ensuring that no single user or IP abuses the system by sending too many requests within a short time frame.
- Security & logging: Accurate logs, which include the real client IP, are essential for security auditing, identifying malicious behavior, and tracking the origins of cyber-attacks.
X-Forwarded-Host – Original Host Value
Description:
The X-Forwarded-Host header indicates the original Host header sent by the client before it passed through any proxies or load balancers. This is helpful in scenarios where the proxy server changes the host value, such as when multiple websites are hosted on the same server or when the request is being handled by a load balancer that changes the destination host.
Syntax:
X-Forwarded-Host: originalHostValue
The originalHostValue represents the original host as seen by the client. This can be the domain name or IP address the client initially connected to, which might differ from the host that the request is ultimately routed to by the proxy.
Use Cases:
- Handling multi-site configurations: In cases where a proxy routes requests to multiple services or websites, X-Forwarded-Host ensures that the original domain or host name is preserved, allowing the server to respond appropriately.
- URL generation: For applications that need to generate absolute URLs or send email links, having the original host available allows the system to accurately create links based on the initial client request.
- Redirection management: If a user is redirected from one domain to another, knowing the original host helps ensure that redirects are handled properly, especially in complex, multi-domain setups.
X-Forwarded-Proto – Protocol Used (HTTP/HTTPS)
Description:
The X-Forwarded-Proto header indicates the protocol used by the client to make the original request. This header is particularly useful when requests pass through a proxy or load balancer that may alter the protocol (e.g., from HTTPS to HTTP) during routing. It helps maintain the correct information about whether the original request was secure (HTTPS) or not (HTTP).
Syntax:
X-Forwarded-Proto:
Where
can be either http or https, depending on the protocol used by the client to communicate with the server.
X-Forwarded-Proto: https
Use Cases:
- Ensuring secure connections: When a request is routed through multiple proxies, it’s important to know whether the original connection was secure. By checking the X-Forwarded-Proto header, applications can decide if they need to force HTTPS for security purposes.
- Redirect management: If an application needs to ensure that users always access the site via HTTPS, the X-Forwarded-Proto header can be used to check the protocol and, if necessary, redirect users to the secure version of the site.
- Mixed content handling: Some web pages may load resources (e.g., images, scripts) via HTTP even when the main page is loaded over HTTPS. The X-Forwarded-Proto header helps to identify the original protocol, allowing developers to prevent mixed content issues by forcing all resources to load over HTTPS.
Other Headers: Forwarded (RFC 7239), X-Real-IP
Description:
In addition to the commonly used X-Forwarded headers, there are a couple of other headers worth noting-Forwarded (defined in RFC 7239) and X-Real-IP.
- Forwarded (RFC 7239): This header is part of an IETF RFC standard and is designed to consolidate multiple forwarding headers into a single, standardized format. It can include multiple pieces of information such as the client’s IP, the protocol, and the host.
- X-Real-IP: Similar to X-Forwarded-For, the X-Real-IP header holds the original IP address of the client. Some proxy servers use this header to pass the real client IP without maintaining a chain of proxies as seen in X-Forwarded-For.
Syntax:
Forwarded (RFC 7239):
Forwarded: for=clientIP; proto=https; host=originalHost
In this syntax:
- for=clientIP: Specifies the IP address of the original client.
- proto=https: Indicates that the original request was made over HTTPS.
- host=originalHost: Represents the original host that the client connected to.
X-Real-IP:
X-Real-IP: clientIP
The clientIP in this case is the IP address of the client that made the request, typically used by the first proxy or load balancer.
Use Cases:
Forwarded (RFC 7239): This header is useful for simplifying and standardizing the forwarding of request details in complex setups with multiple proxies. It consolidates information from different X-Forwarded headers into one, making it easier to handle and interpret.
X-Real-IP: This header is commonly used in simpler proxy setups or when the full chain of IPs is not necessary. It typically represents the original client IP, passed directly by the first proxy without any further proxy chains.
Why are X-Forwarded Headers Important?
X-Forwarded headers are vital for preserving the integrity of client request data when requests pass through intermediaries like proxies and load balancers. These headers allow servers to access the original details about the client, even if they are masked or altered by intermediary layers.
Some key reasons as to why they are important are :
- Identify Original Client IPs
The primary use of X-Forwarded headers is to identify the true client IP address. Without this information, servers would only see the proxy or load balancer IPs, which could lead to inaccurate data and ineffective security measures.
By examining the X-Forwarded header, servers can accurately track the origin of requests, which is crucial for logging, analytics, and security enforcement.
- Apply Geo-Blocking or Rate-Limiting Rules
Knowing the original client IP helps with applying geo-blocking or rate-limiting measures. For example, if an application needs to restrict access based on the user’s geographical location, the client’s IP address is essential for identifying where the request is coming from.
Similarly, rate-limiting rules can be applied based on the client’s IP to prevent abuse of the system, such as excessive requests from a single client.
- Accurate Logging and Auditing
Accurate logs are essential for troubleshooting, security auditing, and monitoring. The original client IP is necessary to track the path of a request and understand its behavior within the network. For security teams, this information can be vital for investigating potential threats and tracking malicious activity.
- Improve Security and Compliance Visibility
X-Forwarded headers help enhance security visibility by ensuring that the original client information is accessible. This visibility is particularly important for compliance with privacy regulations and for ensuring that security policies are applied correctly. For example, an organization may need to maintain access logs with accurate client information for compliance with data protection laws.
- Enable Load Balancer Decisions
In more advanced systems, X-Forwarded headers can help load balancers make more informed decisions. For example, knowing the original protocol or host can help load balancers properly route traffic to the correct application instance. This ensures that traffic is managed efficiently, maintaining the performance and stability of the system.
Why Browsers Hide X-Forwarded Headers
Browsers hide X-Forwarded headers for a combination of security, privacy, and functional reasons.
- Protects user privacy: Prevents websites from accessing the real client’s IP address and other sensitive details.
- Prevents header spoofing: Stops malicious websites from manipulating these headers to bypass security mechanisms.
- Prevents information leakage: Shields network infrastructure and internal routing details that could be exploited by attackers.
- Reduces attack surface: Limits the potential for misuse by malicious sites seeking to exploit or misuse client request data.
- Ensures reliable security checks: By hiding these headers, browsers make it harder for attackers to bypass security rules based on IP or protocol.
Read More: Request Raise for Status – Python
How X-Forwarded Headers Work (with Examples)
X-Forwarded headers work by passing key client request details through intermediary layers like proxies and load balancers. These headers ensure that the original client data is preserved, even when the request is routed through multiple servers.
As illustrated in this image, when a client makes a request, it may pass through one or more proxies or load balancers before reaching the final server.
Each proxy or load balancer adds its own details to the request, while the X-Forwarded headers help retain the original client information.
Example in Express.js
In a Node.js application using Express.js, the X-Forwarded-For header can be accessed using req.headers. This makes it easy to retrieve the original client’s IP, even if the request passed through multiple proxies.
const clientIP = req.headers[‘x-forwarded-for’] || req.connection.remoteAddress;
In this example, the x-forwarded-for header contains the client’s original IP address, while req.connection.remoteAddress provides the IP address of the proxy if the header is absent.
Example in NGINX
In NGINX, proxies can set the X-Forwarded-For header to preserve the client’s IP. The proxy_set_header directive ensures that the header is passed along to the backend server.
proxy_set_header X-Forwarded-For $remote_addr;
This configures NGINX to send the client’s IP address to the backend server, allowing it to track the original source of the request.
Multiple Proxy Hops and IP List Ordering
When multiple proxies are involved, the X-Forwarded-For header will contain a list of IPs, ordered in the sequence the request passed through the proxies. The client’s IP will always appear first in the list, followed by the IP addresses of the intermediary proxies.
X-Forwarded-For: clientIP, proxy1IP, proxy2IP
Each proxy adds its IP to the end of the list, preserving the chain of requests. This allows the backend server to determine both the original client’s IP and the path the request took through the proxies.
Security Considerations when Using X-Forwarded Headers
While X-Forwarded headers are essential for preserving client data, they can also introduce security risks if not handled properly.
Some key considerations are :
- Headers can be spoofed: Since X-Forwarded headers are part of the HTTP request, they can be manipulated by attackers. They may fake the X-Forwarded header to bypass security measures such as IP-based filtering or rate limiting.
- Don’t blindly trust incoming headers: Never assume that the X-Forwarded headers are accurate. Always validate the headers before making any security decisions or logging actions based on them.
- Use trusted proxy chains: Ensure that all proxies in your infrastructure are trusted. This reduces the risk of receiving manipulated headers from untrusted or malicious proxies.
- Implement validation logic: Check the X-Forwarded header for consistency, ensuring the correct order of IPs and that it matches the expected format. This can help prevent spoofed or incorrect data from reaching your server.
- Fallback to remoteAddr if X-Forwarded is untrusted: If you cannot verify the authenticity of the X-Forwarded header, rely on the remoteAddr to get the IP address directly from the connection, which is more reliable.
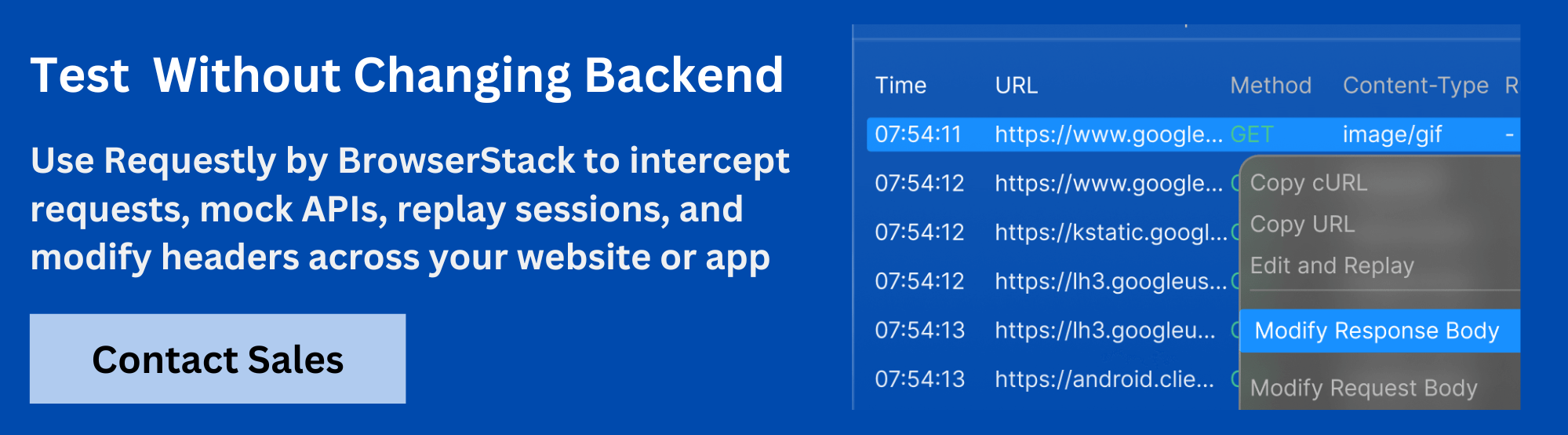
Testing X-Forwarded Headers with Requestly
Web applications often rely on X-Forwarded headers to track the original client’s IP, protocol, and host-especially when requests pass through proxies or load balancers. To ensure these headers are working correctly, testing is crucial for accurate IP resolution, security, and debugging.
Requestly makes it easy to manipulate these headers directly from the browser, simplifying the process.
How to Modify or Add Headers in HTTP Requests
- Inject Custom Headers with Ease: Requestly makes it simple to add or modify headers like X-Forwarded-For, X-Forwarded-Host, and X-Forwarded-Proto. This is especially useful for simulating requests from specific IPs or hosts, without the need to alter server-side configurations.
- Create Header Rewrite Rules for Specific URLs: With Requestly, you can set up header rewrite rules that apply only to specific URL patterns. This allows for focused testing of particular endpoints or environments, without impacting the backend setup.
Pro Tip : Take advantage of Requestly’s intuitive interface to quickly modify and test X-Forwarded headers directly from the browser. This eliminates the need for complex server-side changes and helps ensure your proxy and header configurations are working as expected before deployment.
Simulating Multiple Proxy Scenarios
- Replicate Proxy Chains: By adding multiple IP addresses to the X-Forwarded header, Requestly allows you to simulate requests passing through several proxy servers. This ensures that your application handles the header correctly, even in complex routing scenarios.
- Test Security Measures with Proxy Chains: Simulating different proxy setups lets you verify that security rules-such as IP allowlists or geolocation restrictions-are applied properly, ensuring your application is secure in all situations.
Debugging IP Resolution Logic in Development and Staging
- Ensure Consistent IP Resolution: Manipulating the X-Forwarded-* headers in development or staging environments ensures that the application’s IP resolution logic behaves consistently across different environments.
- Quickly Identify Issues: When discrepancies arise between environments, adjusting the headers can help quickly pinpoint whether the issue is with the proxy configuration or application logic.
Easily Set Up Header Rules in the Browser
- No Need for Server-Side Changes: Requestly works directly within the browser, so you don’t need to modify backend code or infrastructure to test different header scenarios.
- Manage Rules with a Click: Requestly’s intuitive interface lets you easily create, enable, or disable header rewrite rules. Switching between different testing configurations becomes quick and seamless.
- Collaborate Across Teams: Rules can be exported and shared with your team, ensuring that testing scenarios are consistent across different browsers and devices.
Pro Tip : After testing headers in your development environment, use BrowserStack to validate how your application performs across different browsers and devices. This ensures that your header manipulation doesn’t break functionality on other platforms and that security measures, like IP allowlists, are universally applied.
Some practical use cases are illustrated in the table below –
| Scenario | Example Rule with Requestly |
| Simulate client IP from a proxy | Add X-Forwarded-For: 203.0.113.1 |
| Emulate multiple proxies | Add X-Forwarded-For: 203.0.113.1, 198.51.100.2 |
| Test HTTPS detection | Set X-Forwarded-Proto: https |
| Override host for multi-tenant apps | Set X-Forwarded-Host: staging.example.com |
How does Requestly simplify testing X-Forwarded headers
Requestly streamlines the process of testing and debugging X-Forwarded-* headers by offering an intuitive, browser-based solution that eliminates the need for server-side changes or complex proxy setups.
By centralizing and simplifying header manipulation directly within the browser, Requestly makes it easier to test and validate IP resolution, security logic, and environment-specific behaviors. This approach reduces the complexity of testing X-Forwarded headers, helping teams quickly troubleshoot and ensure application functionality.
Some key features through which Requestly simplifies testing X-forwarded headers are –
- Visual Rule Management
- Provides a user-friendly interface for creating, editing, and toggling header modification rules.
- Rules can be quickly enabled or disabled to switch between different test scenarios without code changes.
- Granular Targeting
- Allows targeting of specific URLs, domains, or request types, ensuring header modifications only apply where needed.
- Supports advanced pattern matching for precise control over test coverage.
- Flexible Header Manipulation
- Enables the addition, modification, or removal of any X-Forwarded-* header, including X-Forwarded-For, X-Forwarded-Host, and X-Forwarded-Proto.
- Multiple values can be set to simulate complex proxy chains or multi-tenant environments.
- Instant Feedback
- Changes take effect immediately within the browser, allowing for rapid iteration and troubleshooting.
- Facilitates quick validation of application behavior in response to different header values.
- Collaboration and Consistency
- Rule sets can be exported and shared among team members, ensuring consistent testing practices across different machines and browsers.
A workflow example to illustrate this would look like –
- Set Up a Header Rewrite Rule in Requestly: Define a rule in Requestly to set or modify the X-Forwarded header for a specific target URL, simulating different client IPs or proxy chains.
- Trigger Requests and Monitor Responses: Send requests to the application and observe how the backend processes the simulated client IP or proxy chain, ensuring that the behavior aligns with expected outcomes.
- Adjust Rules for Various Scenarios: Modify the header rewrite rules to simulate different scenarios, such as multiple proxy hops or changes in the protocol (e.g., HTTP to HTTPS), and test how the application responds.
- Share Rule Configurations: Export and share the header rewrite rules with team members to ensure consistent testing across multiple environments and browsers.
Best Practices in using X-Forwarded Headers
When working with X-Forwarded headers, following best practices ensures accuracy, security, and reliability in your applications.
Here are five key practices to keep in mind:
- Validate Incoming Headers: Never trust incoming X-Forwarded headers blindly. Always validate the headers to ensure they come from trusted proxies to avoid spoofing attacks.
- Use Trusted Proxy Chains: Ensure that the entire chain of proxies is trusted. This prevents malicious proxies from modifying or injecting false information into the headers.
- Implement Security Measures: Apply proper security controls, such as IP allowlists or geolocation restrictions, using the data in the X-Forwarded headers to protect your application from unauthorized access.
- Limit Header Length: Be mindful of the size of the X-Forwarded header, especially when dealing with multiple proxies. Large headers can impact performance or cause issues with server configurations.
- Fallback to remoteAddr if Untrusted: If the X-Forwarded header cannot be trusted, fall back to using the server’s remoteAddr as a more reliable method of identifying the client’s IP
Conclusion
X-Forwarded headers are essential for accurately tracking client request data, especially in complex proxy setups. Tools like Requestly simplify testing and debugging these headers, providing an intuitive, code-free way to validate IP resolution, security logic, and environment-specific behaviors. By integrating Requestly into the workflow, teams can ensure reliable application performance across all environments.