The X-Forwarded-Proto header is essential for indicating the original protocol (HTTP or HTTPS) used in a request, especially when traffic passes through proxies or load balancers. However, if not properly managed, this header can become a vulnerability, allowing attackers to manipulate it for malicious purposes, such as bypassing secure HTTPS connections.
Overview
What is X-Forwarded-Proto?
The X-Forwarded-Proto header indicates the protocol (HTTP or HTTPS) that was used by the client to make a request before it was passed through a proxy or load balancer. It helps servers determine whether to enforce secure connections based on the original request.
Security Risks Associated with X-Forwarded-Proto:
- Header Manipulation: Attackers can modify the X-Forwarded-Proto header to spoof the protocol and bypass HTTPS security measures.
- Insecure Redirection: Malicious manipulation of the header can lead to insecure redirects from HTTPS to HTTP, exposing sensitive data.
- Untrusted Proxies: Relying on untrusted proxies for this header may lead to inaccurate or altered data, compromising security.
- Bypassing Security Policies: Poor validation of the header can allow attackers to bypass security policies, especially in applications that enforce HTTPS.
Best Practices for Handling X-Forwarded-Proto:
- Validate the Header: Ensure the X-Forwarded-Proto header is only trusted from trusted proxies and load balancers.
- Enforce HTTPS: Always redirect HTTP requests to HTTPS using the header to ensure secure communication.
- Use Strict Transport Security (HSTS): Implement HSTS to enforce HTTPS connections, regardless of the protocol in the X-Forwarded-Proto header.
- Disable Untrusted Proxies: Avoid trusting any proxy that isn’t fully secured to prevent header manipulation.
What is the X-Forwarded-Proto Header?
The X-Forwarded-Proto header is a key component in modern web application architectures that use proxies or load balancers. It indicates the protocol (either HTTP or HTTPS) that was used by the client to initiate the request before it passed through an intermediary server. This header is crucial because, in many cases, proxies or load balancers sit between the client and the backend server, which may not be able to directly detect whether the original request was secure (HTTPS) or not (HTTP).
For example, when a client sends a request over HTTPS, but the request passes through a proxy that communicates with the backend over HTTP, the X-Forwarded-Proto header informs the server that the original request was made using HTTPS. This allows the server to properly handle redirects, security policies, and ensure that secure communication is maintained throughout the entire request flow.
Common Use Cases of X-Forwarded-Proto Header
The X-Forwarded-Proto header plays a critical role in several scenarios where web traffic passes through intermediate systems like proxies, load balancers, or reverse proxies. Here are some common use cases:
- Handling Secure Redirects: When a client makes an HTTP request but the server wants to enforce HTTPS, the X-Forwarded-Proto header can help determine if the original request was over HTTP. Based on this, the server can redirect the client to the HTTPS version of the page to ensure secure communication.
- Enforcing HTTPS Security Policies: Many web applications rely on HTTPS for secure data transmission. By checking the X-Forwarded-Proto header, a server can verify that the request was originally made over HTTPS and apply relevant security measures, like setting HTTP Strict Transport Security (HSTS) or blocking HTTP connections entirely.
- SSL Termination in Load Balancers: In configurations where SSL termination happens at a load balancer, the backend servers may not directly handle SSL/TLS connections. The load balancer forwards the original protocol information (HTTPS or HTTP) to the backend server using the X-Forwarded-Proto header, which helps the backend server maintain security awareness.
- Tracking Original Protocol for Analytics: Some systems use the X-Forwarded-Proto header to track which clients accessed a service over HTTP versus HTTPS. This information can be useful for understanding traffic patterns and adjusting security settings accordingly.
- Proxying Requests Across Different Protocols: When multiple layers of proxies or reverse proxies are involved, the X-Forwarded-Proto header ensures that the backend server knows whether the original request came over a secure connection (HTTPS) or an unsecured one (HTTP), allowing it to handle the request correctly based on the protocol.
- Conditional Logic Based on Protocol: Websites or applications might want to serve different content depending on the protocol used. For example, certain resources or features may only be available to users on HTTPS. The X-Forwarded-Proto header helps implement such conditional logic by revealing whether the request was secure or not.
How X-Forwarded-Proto Works in Web Infrastructure
The X-Forwarded-Proto header is vital in web architectures that involve proxies or load balancers. It helps backend servers understand whether the original client request was made over HTTP or HTTPS, even if the server itself doesn’t handle the initial connection.
- Proxying Requests: When a client sends a request through a proxy or load balancer, the X-Forwarded-Proto header is added to indicate the protocol (HTTP or HTTPS) used by the client.
- SSL Termination: In cases where SSL is terminated at the proxy, the backend server uses this header to know if the request was initially secure (HTTPS) or not, even though it only communicates over HTTP.
- Enforcing Secure Communication: The backend server can inspect this header to enforce security policies, such as redirecting HTTP requests to HTTPS for secure communication.
- Multi-Layer Proxies: In setups with multiple proxies, only the last proxy adds the correct X-Forwarded-Proto header, ensuring the backend server receives accurate protocol information.
Example Scenario:
- A user connects to a website over HTTPS.
- The user’s request passes through a reverse proxy or load balancer.
- The proxy forwards the request to the backend server, including the X-Forwarded-Proto: https header.
- The backend server receives the request and can validate that it was originally made over HTTPS, allowing the server to serve secure content and apply appropriate security measures.
- If the request were over HTTP, the backend server could redirect the user to the HTTPS version of the page to ensure a secure connection.
Security Risks Associated with X-Forwarded-Proto
These security risks highlight the potential vulnerabilities that can arise when the X-Forwarded-Proto header is not properly handled or validated, allowing attackers to bypass security measures and compromise communication.
- Header Manipulation: Attackers can manipulate the X-Forwarded-Proto header to spoof the protocol, making a request appear secure (HTTPS) when it was originally made over HTTP. This can lead to vulnerabilities, such as allowing insecure access to sensitive data.
- Insecure Redirects: If the X-Forwarded-Proto header is not properly validated, attackers can exploit it to bypass HTTPS redirects. This allows them to trick users into accessing insecure (HTTP) versions of a website, potentially exposing data to man-in-the-middle attacks.
- Untrusted Proxies: Relying on untrusted or misconfigured proxies to pass the X-Forwarded-Proto header can result in incorrect protocol information. This can cause the server to apply improper security policies, such as failing to enforce HTTPS connections or applying insecure configurations.
- Bypassing Security Policies: Improper validation of the X-Forwarded-Proto header can allow attackers to bypass critical security measures like Strict Transport Security (HSTS), which is designed to force secure (HTTPS) connections. If attackers can manipulate the header, they may prevent these policies from being enforced, leading to insecure communication.
Read More: Top 10 Python REST API Frameworks
Best Practices for Handling X-Forwarded-Proto
To mitigate the security risks associated with the X-Forwarded-Proto header, it’s essential to follow best practices that ensure proper handling and validation.
- Validate the Header: Ensure that the X-Forwarded-Proto header is only trusted from known, trusted proxies or load balancers. Do not rely on this header if it comes from an untrusted source, as it can be easily manipulated by attackers.
- Enforce HTTPS: Always redirect HTTP requests to HTTPS based on the X-Forwarded-Proto header. If the header indicates an HTTP request, enforce a secure HTTPS connection to protect user data.
- Use Strict Transport Security (HSTS): Implement HSTS to enforce the use of HTTPS, regardless of the protocol specified in the X-Forwarded-Proto header. This prevents attackers from bypassing secure connections.
- Disable Proxy Trust on Unsecured Systems: In environments where proxies are not fully secured, avoid trusting the X-Forwarded-Proto header entirely. This can prevent attackers from manipulating the header to bypass security controls.
- Monitor and Log Header Usage: Continuously monitor and log the X-Forwarded-Proto header’s usage to identify potential security misconfigurations or attempts to exploit vulnerabilities.
How to Test and Validate X-Forwarded-Proto Configurations
To ensure proper handling and security of the X-Forwarded-Proto header, it’s important to regularly test and validate its configuration. Here are some key steps to help you do so:
- Check Header Integrity: Inspect the X-Forwarded-Proto header in incoming requests to ensure it correctly reflects the protocol (HTTP or HTTPS) used by the client before passing through any proxies.
- Test with Different Protocols: Send both HTTP and HTTPS requests, and verify that the server handles them properly based on the X-Forwarded-Proto header. For HTTP requests, check that the server redirects to HTTPS, and for HTTPS requests, ensure secure communication is maintained.
- Simulate Attacks: Test how the application responds to manipulated X-Forwarded-Proto headers. Verify if the server continues to enforce security policies, such as HTTPS redirects and strict transport security, even with altered header values.
- Automate Tests: Use automated security testing to continuously monitor for potential misconfigurations in handling the X-Forwarded-Proto header, ensuring any vulnerabilities are detected early.
- Validate Against Trusted Proxies: Ensure that the X-Forwarded-Proto header is only accepted from trusted proxies. Reject any requests with headers that come from untrusted sources or contain suspicious modifications.
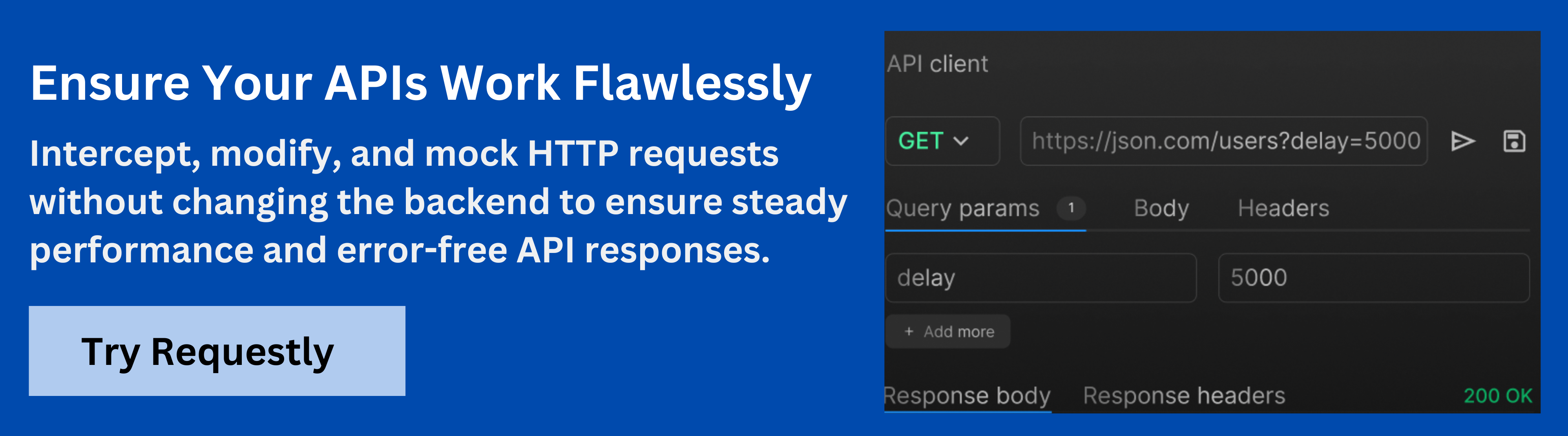
Streamline Security Testing with Requestly
Requestly by BrowserStack offers powerful features for modifying HTTP requests and headers, which can be useful for streamlining security testing of the X-Forwarded-Proto header. Here’s how you can use Requestly for testing:
- Modify Headers in Real-Time: Requestly allows you to modify the X-Forwarded-Proto header on the fly, enabling you to simulate requests with different protocols (HTTP/HTTPS) and test how your server handles them.
- Simulate Redirection: Use Requestly to modify the X-Forwarded-Proto header and test if your server correctly enforces HTTPS redirection for HTTP requests, ensuring your security policies are being followed.
- Intercept and Inspect Traffic: Requestly helps you intercept live traffic, inspect headers like X-Forwarded-Proto, and verify that your server is handling secure and non-secure requests appropriately.
- Test Custom Scenarios: Inject custom headers or manipulate requests to test various server configurations, ensuring that the application correctly handles protocol-related scenarios without introducing vulnerabilities.
By using Requestly to modify headers and simulate different request conditions, you can efficiently test how your web infrastructure responds to different X-Forwarded-Proto configurations.
Conclusion
The X-Forwarded-Proto header plays a critical role in ensuring secure communication between clients and servers, especially in architectures involving proxies or load balancers. While it provides essential information about the original request protocol (HTTP or HTTPS), improper handling or validation of this header can lead to significant security risks, such as man-in-the-middle attacks, insecure redirects, and bypassing security policies.
By following best practices such as validating headers, enforcing HTTPS, and using tools like Requestly for real-time testing and monitoring, you can safeguard your infrastructure against potential vulnerabilities. Regularly testing and validating the configuration of the X-Forwarded-Proto header is essential to maintaining a secure web environment and protecting sensitive user data from exploitation.
By implementing the strategies outlined in this article, you can ensure that your system is secure, resilient, and able to handle requests in a manner that upholds the integrity and security of your web applications.