Authentication is a key element of securing APIs and web applications. Among various methods available, bearer tokens have become one of the most common and efficient ways to verify requests in stateless systems. According to recent API security reports, more than 70% of modern APIs use bearer tokens for access control, particularly through OAuth 2.0 and JSON Web Tokens (JWT). Understanding how bearer tokens work helps developers implement stronger authentication systems and prevent unauthorized access.
What is a Bearer Token?
A bearer token is a type of access token that allows access to a protected resource when included in an HTTP request. The term “bearer” implies that whoever possesses the token can use it to access the resource-it does not require further proof of identity.
Bearer tokens are typically issued by an authorization server after successful user authentication. Once received, they are included in subsequent requests to access APIs securely. These tokens often have an expiration time to limit exposure in case of compromise.
In most systems, bearer tokens are transmitted in the Authorization header of an HTTP request as follows:
Authorization: BearerThis approach ensures that sensitive credentials are not transmitted directly, reducing risks associated with credential reuse.
How Bearer Authentication Works?
Bearer authentication operates on a straightforward flow: obtain the token once, and use it for all subsequent authorized requests. The general process includes the following steps:
- User Authentication: A user logs into an application with valid credentials, which are verified by an authentication server.
- Token Issuance: Once verified, the server issues a bearer token to the client.
- Token Usage: The client includes the token in the Authorization header of each HTTP request to access protected resources.
- Validation: The API server validates the token against its signature or via an authorization server.
- Access Granted or Denied: If valid, access is granted; otherwise, the request is rejected.
This method supports stateless authentication, meaning the server doesn’t store session.
Read More:How to test redirect with Cypress
Key Components of Bearer Tokens (including JWT, claims, signature)
Bearer tokens, especially those based on JSON Web Tokens (JWT), consist of three main parts:
- Header: Contains metadata about the token type (JWT) and the signing algorithm used, such as HS256 or RS256.
- Payload (Claims): Includes user data and access information, such as user ID, roles, and token expiration time.
- Signature: Generated by encoding the header and payload with a secret key. It ensures token integrity and authenticity.
Example of a JWT structure:
xxxxx.yyyyy.zzzzzEach segment represents the header, payload, and signature respectively. JWT-based bearer tokens are lightweight and easy to validate, making them ideal for modern distributed systems.
Read More: What Is API Automation Testing?
Common Use Cases for Bearer Tokens in APIs and Web Applications
Bearer tokens are used in multiple scenarios where secure, stateless communication is required. Some common use cases include:
- API Access Control: Authenticating and authorizing API requests without maintaining session data.
- Single Sign-On (SSO): Allowing users to log in once and access multiple services.
- Mobile App Authentication: Enabling secure communication between mobile apps and backend services.
- Third-Party Integrations: Facilitating secure connections between APIs of different services via OAuth 2.0.
These tokens ensure both convenience and security, especially in microservices architectures and distributed systems.
How to Include and Use Bearer Tokens in HTTP Requests?
Bearer tokens are included in the HTTP Authorization header using the following format:
GET /api/user/profile HTTP/1.1Host: example.comWhen making API requests, clients must ensure the token is:
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9…
- Added only to requests requiring authentication.
- Sent over secure HTTPS connections.
- Refreshed or replaced before expiration.
Popular HTTP clients like Postman, Axios, or Fetch API simplify adding bearer tokens to requests, enabling developers to test and automate authentication easily.
Differences Between Bearer Tokens and API Keys / Basic Authentication
While bearer tokens, API keys, and basic authentication all control access, their security and functionality differ:
- Bearer Tokens: Time-bound, encrypted tokens tied to specific users or sessions. Common in OAuth 2.0 systems.
- API Keys: Static credentials used for service authentication, but not ideal for user-level access or revocation control.
- Basic Authentication: Involves sending base64-encoded credentials (username and password) with each request-less secure without encryption.
Bearer tokens offer a more secure, scalable, and flexible approach, especially for APIs handling sensitive data.
Security Considerations: Token Expiry, Revocation, Storage and Transport Protection
Securing bearer tokens is critical since possession equals access. Key security measures include:
- Use HTTPS: Always transmit tokens over encrypted channels.
- Short Expiry Times: Reduce risk exposure by limiting token lifespan.
- Token Revocation: Allow users or systems to invalidate tokens when needed.
- Secure Storage: Store tokens securely on the client side (e.g., HTTP-only cookies or secure storage APIs).
- Rotate Tokens Regularly: Periodically refresh tokens to minimize potential misuse.
These practices strengthen the authentication flow and protect against common threats like token theft or replay attacks.
Debugging and Testing Bearer Token Workflows
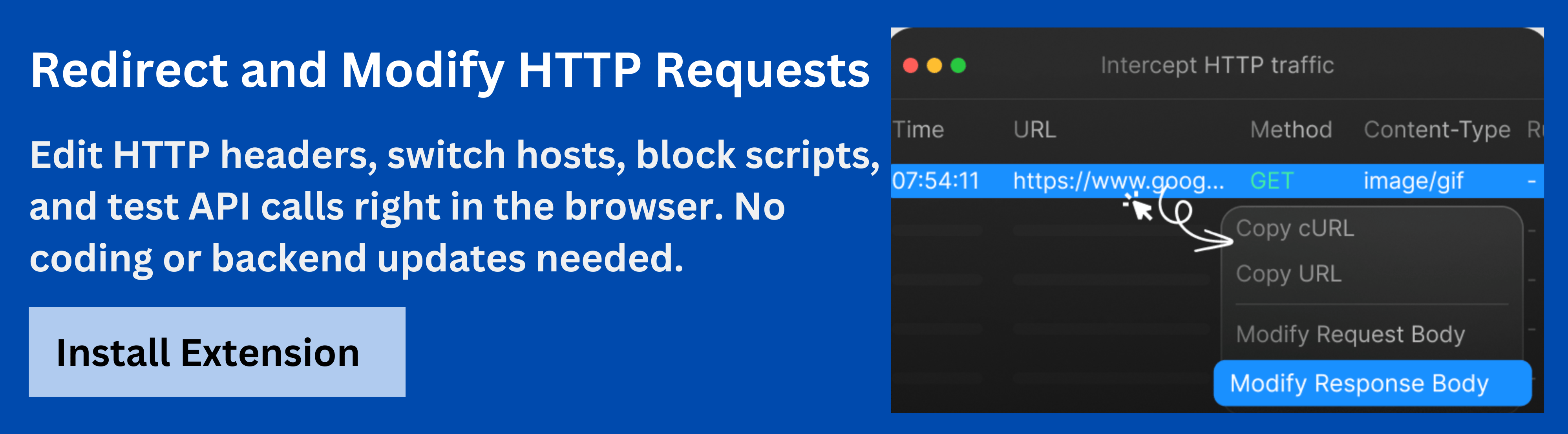
During development, debugging bearer token authentication is vital to ensure reliability. Tools that allow intercepting and modifying HTTP requests help test how APIs respond to valid, expired, or malformed tokens.
Requestly HTTP Interceptor offers a streamlined way to inspect, intercept, and modify HTTP requests directly in the browser. Developers can easily adjust Authorization headers, simulate expired or invalid tokens, and observe how APIs respond under different authentication scenarios-all without changing server-side configurations.
With Requestly HTTP Interceptor, developers gain a visual and efficient way to debug token-based authentication, automate testing workflows, and validate API security in real time. It’s an essential tool for ensuring that bearer token implementations are both secure and resilient.
Best Practices for Implementing Bearer Token Authentication
Implementing bearer token authentication securely requires adherence to best practices:
- Use short-lived tokens and refresh tokens for extended sessions.
- Store tokens securely and avoid exposing them in URLs or logs.
- Validate token signatures on every request.
- Employ scopes and claims to limit access levels.
- Revoke tokens immediately after logout or suspected compromise.
Following these guidelines minimizes risks and ensures reliable authentication across distributed systems.
Troubleshooting Common Issues and Pitfalls
Developers often encounter issues such as invalid signatures, expired tokens, or missing headers. Common troubleshooting steps include:
- Verifying that the Authorization header includes the correct “Bearer” prefix.
- Ensuring clock synchronization between servers to prevent expiration errors.
- Checking token encoding and signing algorithms.
- Monitoring logs for unauthorized or failed token validations.
A systematic debugging approach helps maintain authentication reliability and security consistency.
Future Trends: Proof-of-Possession, Token Binding, and Evolving Standards
The evolution of authentication standards is addressing weaknesses in bearer tokens. Proof-of-Possession (PoP) tokens aim to bind tokens to a specific client, preventing misuse if stolen. Similarly, token binding ensures tokens are only valid when used from their original transport layer.
With emerging protocols like OAuth 2.1 and enhanced identity management tools, the future of bearer authentication will focus on stronger cryptographic binding and reduced dependency on static tokens.
Conclusion
Bearer tokens have become the foundation of secure, scalable authentication in modern applications. Their flexibility, simplicity, and compatibility with OAuth 2.0 make them ideal for protecting APIs and user data. However, implementing them securely requires proper handling, regular validation, and thorough testing to prevent unauthorized access.
With the right debugging and testing practices-supported by tools like Requestly-developers can build more secure, reliable authentication systems that protect users and data effectively.