Basic Authentication remains one of the simplest and most widely recognized methods for securing HTTP requests. Despite the emergence of more advanced authentication schemes like OAuth and JWT, Basic Authentication is still commonly used in testing, internal APIs, and legacy systems due to its straightforward implementation. However, its simplicity also brings certain security considerations that developers must understand to use it responsibly.
What Is Basic Authentication?
Basic Authentication is an HTTP authentication method that uses a combination of a username and password to verify a user’s identity. These credentials are encoded using Base64 and sent in the HTTP request header.
The header format follows this structure:
Authorization: BasicFor example, if your username is admin and password is password123, the encoded string would look like this:
Authorization: Basic YWRtaW46cGFzc3dvcmQxMjM=The server decodes this string, validates the credentials, and grants access if they match a valid user record.
Read More:What is API testing (with Examples)
How Basic Authentication Works
The Basic Authentication flow is straightforward and involves a simple exchange between the client and the server:
- Client Request: The client sends an HTTP request with an Authorization header containing the Base64-encoded credentials.
- Server Verification: The server decodes the credentials and checks them against its authentication database.
- Response:
- If valid, the server returns a 200 OK response along with the requested resource.
- If invalid, the server returns a 401 Unauthorized status, prompting the client to provide valid credentials.
Example request:
GET /protected-resource HTTP/1.1Host: example.comExample response (on failure):
Authorization: Basic YWRtaW46cGFzc3dvcmQxMjM=
HTTP/1.1 401 UnauthorizedWWW-Authenticate: Basic realm=”Access to the protected resource”The process is simple but lacks encryption, which makes secure transport layers like HTTPS mandatory.
Read More:What Is API Automation Testing?
Setting Up Basic Authentication on Servers
Implementing Basic Authentication depends on your server environment or framework. Below are some examples across popular technologies:
In Apache:
Add the following to your .htaccess file:
AuthType BasicAuthName “Restricted Area”In Nginx:
AuthUserFile /path/to/.htpasswd
Require valid-user
location /secure/ { auth_basic “Restricted Area”;
auth_basic_user_file /etc/nginx/.htpasswd;
}In Express.js (Node.js):app.use((req, res, next) => { const auth = {login: ‘admin’, password: ‘password123’};
const b64auth = (req.headers.authorization || ”).split(‘ ‘)[1] || ”;
const [login, password] = Buffer.from(b64auth, ‘base64’).toString().split(‘:’);
if (login === auth.login && password === auth.password) {
return next();
}
res.set(‘WWW-Authenticate’, ‘Basic realm=”401″‘);
res.status(401).send(‘Authentication required.’);
});This middleware validates credentials from incoming requests and restricts access to authorized users only.Read More: Top 10 Python REST API Frameworks in 2024
Using Basic Authentication in APIs and Clients
Basic Authentication is often used in APIs or automated scripts for quick authentication.
Example using cURL:
curl -u admin:password123 https://api.example.com/dataExample using Axios (JavaScript):
const axios = require(‘axios’);axios.get(‘https://api.example.com/data’, {
auth: {
username: ‘admin’,
password: ‘password123’
}
})
.then(response => console.log(response.data))
.catch(error => console.error(error));Example using Python Requests:import requestsresponse = requests.get(‘https://api.example.com/data’, auth=(‘admin’, ‘password123’))Although convenient, Basic Authentication should only be used over HTTPS to prevent credentials from being exposed.
print(response.json())
Security Limitations of Basic Authentication
Despite its simplicity, Basic Authentication has several security weaknesses:
- Base64 is not encryption: It merely encodes data, which can be easily decoded.
- Credentials sent with every request: This increases the risk of interception.
- Lack of session management: There is no token or expiration mechanism.
- Vulnerability to replay attacks: Credentials can be reused if intercepted.
- No built-in logout mechanism: The browser often caches credentials, leading to potential misuse.
These drawbacks make Basic Authentication suitable only for internal tools or when used with HTTPS and other security measures.
Alternatives to Basic Authentication
Modern authentication methods offer better security and scalability compared to Basic Authentication. Some alternatives include:
- Bearer Tokens (JWT): Stateless and secure, used widely in RESTful APIs.
- OAuth 2.0: Provides delegated authorization with access tokens.
- API Keys: Simple for service-to-service communication.
- Digest Authentication: Similar to Basic Auth but adds hashing to credentials for improved security.
Choosing the right method depends on the application’s complexity, sensitivity of data, and scalability requirements.
Debugging and Testing Basic Authentication
Debugging authentication headers can be challenging when credentials fail or responses return 401 Unauthorized. To effectively test Basic Authentication, developers need visibility into request headers and responses.
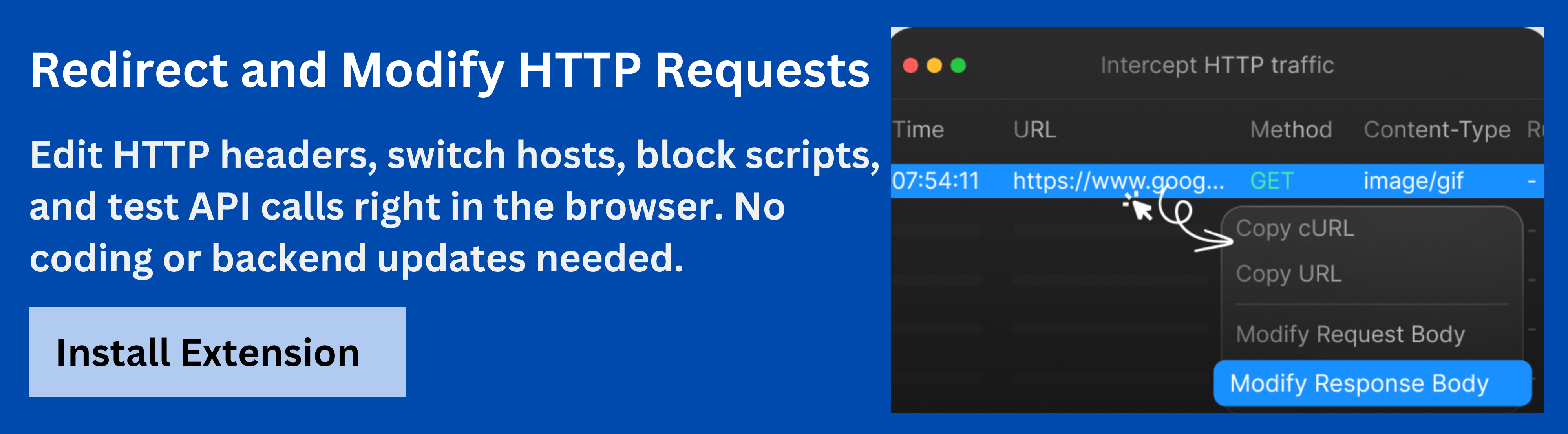
The Requestly HTTP Interceptor is an excellent tool for inspecting and debugging Basic Authentication flows. It allows developers to intercept, modify, and replay HTTP requests directly from the browser without altering code.
With Requestly HTTP Interceptor, you can:
- View and edit the Authorization header to verify correct Base64 encoding.
- Simulate failed or expired credentials to test server-side error handling.
- Modify endpoints or authentication schemes for testing scenarios.
- Validate response behavior under different security conditions.
Enhance your API debugging workflow with Requestly HTTP Interceptor-a browser-based tool that lets you inspect and test Basic Authentication headers effortlessly. Debug authentication flows, modify request parameters, and ensure secure communication without modifying your source code.
Best Practices for Implementing Basic Authentication
To ensure secure usage of Basic Authentication, developers should follow these best practices:
- Always use HTTPS: Prevent credentials from being exposed in plain text.
- Avoid hardcoded credentials: Use environment variables or configuration files.
- Limit access scope: Restrict endpoints accessible through Basic Authentication.
- Use strong passwords: Combine Basic Authentication with password policies.
- Regularly rotate credentials: Periodically update usernames and passwords.
- Implement rate limiting: Prevent brute-force attacks on endpoints.
Following these measures helps mitigate risks associated with Basic Authentication.
Frequently Asked Questions (FAQs)
1. Is Basic Authentication secure?
Only when used with HTTPS. Without encryption, credentials can be intercepted easily.
2. What is the difference between Basic and Bearer authentication?
Basic uses username and password encoded in Base64, while Bearer uses tokens (like JWT) that don’t expose user credentials.
3. Can Basic Authentication be used in production?
It’s recommended only for internal services or low-risk environments with HTTPS.
4. Does Basic Authentication support session expiration?
No, it lacks built-in expiration; each request re-sends the credentials.
Conclusion
Basic Authentication provides a simple, effective way to secure resources but should be implemented with caution. Its lack of encryption and session management makes it unsuitable for public APIs or high-security environments. However, when used over HTTPS and complemented with other controls, it can serve lightweight applications well.
By leveraging tools like Requestly HTTP Interceptor, developers can efficiently test, debug, and validate Basic Authentication headers-ensuring correct implementation and secure communication between clients and servers.