SameSite cookies are an essential security feature that helps prevent cross-site request forgery (CSRF) attacks by controlling when cookies are sent with cross-site requests.
Overview
Importance of SameSite Cookies
- Prevents CSRF Attacks: Restricts cookies from being sent with cross-site requests, preventing unauthorized actions on trusted sites.
- Enhances Privacy: Limits the exposure of cookies to third-party sites, protecting user data from unwanted tracking.
- Improves Session Security: Ensures that session cookies are only sent in secure contexts, reducing the risk of session hijacking.
- Simplifies Cross-Domain Cookie Management: Helps developers control cookie behavior in third-party contexts, ensuring security without breaking functionality.
This article explains the functionality of SameSite cookies, their importance for security, best practices for implementation, and methods for debugging and testing them effectively.
What are SameSite Cookies?
SameSite cookies are a special type of cookie with a security attribute designed to control how cookies are sent with cross-site requests.
They are used to prevent cross-site request forgery (CSRF) attacks and improve privacy by limiting the conditions under which cookies are included in requests from different sites.
The SameSite attribute is set on the Set-Cookie header by the server, and it governs whether cookies are sent with cross-origin (cross-site) requests.
By setting the SameSite attribute, developers can control how cookies behave in these scenarios, adding an extra layer of security for web applications.
Must Read: How to Prevent Cross Site Tracking
Why SameSite Cookies are Important for Security
SameSite cookies enhance security by preventing cross-site request forgery (CSRF) attacks. CSRF occurs when a malicious site tricks a user’s browser into making unauthorized requests to a trusted site.
By setting the SameSite attribute, cookies are not sent with cross-site requests unless allowed, protecting against cookie theft and session hijacking when combined with security measures like HTTPS and HttpOnly cookies.
The SameSite attribute helps mitigate risks such as:
- CSRF: Prevents cookies from being sent with cross-origin requests, thereby blocking unauthorized actions.
- Data Leakage: Limits the exposure of cookies to unauthorized domains or third parties.
- Session Hijacking: Reduces the risk of attackers accessing session cookies across different websites.
Different SameSite Cookie Values
The SameSite attribute supports three main values: Strict, Lax, and None. Each value determines when cookies are sent with requests, offering different levels of cross-site request restrictions.
Understanding these values is key to choosing the right balance between security and functionality.
1. SameSite=Strict
When a cookie is set with SameSite=Strict, it offers the highest level of protection. Cookies marked as Strict are only sent in requests originating from the same site (same domain).
This means cookies will not be sent in cross-site requests at all, even if the user is navigating between websites in the same browser session.
- Use Case: Ideal for highly secure applications like banking, where the session cookie should never be exposed to cross-site requests.
- Limitation: May break functionality for some user interactions, like social media login integrations or third-party widgets.
Example:
Set-Cookie: sessionId=abc123; SameSite=Strict; Secure; HttpOnly
2. SameSite=Lax
The SameSite=Lax value provides a moderate level of protection. Cookies marked as Lax are sent in same-site requests and also in top-level navigations (such as when the user clicks a link to navigate between pages on different sites).
However, cookies will not be sent with cross-site subrequests, such as loading images or making API calls from a different domain.
- Use Case: Useful for sites where user authentication is needed, but cross-site request functionality (like embedded third-party content) still needs to work.
- Limitation: Not as secure as Strict, but offers a good balance of security and usability.
Example:
Set-Cookie: userSession=xyz456; SameSite=Lax; Secure; HttpOnly
3. SameSite=None
The SameSite=None value means that the cookie will be sent with all requests, including cross-origin ones. This setting does not provide any restrictions and allows cookies to be shared between different sites.
SameSite=None should be used in conjunction with the Secure flag, ensuring that cookies are sent only over HTTPS connections.
- Use Case: Necessary for third-party services that need to send cookies across different sites, such as advertising networks or login systems used across different websites.
- Limitation: This setting removes security protections entirely for cross-site requests, so it should only be used when absolutely necessary.
Example:
Set-Cookie: thirdPartyAd=def789; SameSite=None; Secure; HttpOnly
How to Set the SameSite Attribute in Set-Cookie
The SameSite attribute is set within the Set-Cookie header to define how cookies behave in cross-site requests. It can be added when sending cookies from the server, and it can take one of three values: Strict, Lax, or None.
To set the SameSite attribute, use the following syntax in the Set-Cookie header:
Set-Cookie: name=value; SameSite=Strict; Secure; HttpOnly
- SameSite=Strict: Cookies will only be sent in same-site requests.
- SameSite=Lax: Cookies will be sent in same-site requests and top-level navigations.
- SameSite=None: Cookies will be sent in all requests, including cross-site, but must be used with the Secure flag.
Including Secure ensures that the cookie is only sent over HTTPS connections, adding an extra layer of security.
Must Read: How to use Cypress Clear Cookies Command?
SameSite Cookies and Cross-Site Request Forgery (CSRF) Protection
SameSite cookies are a strong defense against Cross-Site Request Forgery (CSRF) attacks, where a malicious site tricks a user’s browser into making unwanted requests to a trusted site.
By setting SameSite to Strict or Lax, cookies are blocked from being sent with cross-site requests, preventing unauthorized actions. Combined with HTTPS and the HttpOnly flag, SameSite cookies help reduce CSRF risks and protect user sessions.
SameSite Cookies in Modern Browsers
Modern browsers have begun enforcing the SameSite cookie attribute to enhance security. Browsers like Chrome, Firefox, and Edge have started defaulting to SameSite=Lax for cookies that don’t specify a value, offering a balance between security and user experience.
Key browser behaviors include:
- SameSite=Lax by Default: Cookies without the SameSite attribute are treated as Lax, meaning they will be sent in same-site requests and top-level navigations.
- SameSite=None Requires Secure: Cookies set with SameSite=None must also include the Secure flag, ensuring they are only sent over HTTPS.
- Enforcement of SameSite Rules: Older versions of browsers may not fully support SameSite enforcement, but recent updates have made this behavior the default for enhanced security.
These changes help prevent CSRF and other cross-origin attacks by reducing unnecessary exposure of cookies to third-party sites.
Challenges with SameSite Cookies in Third-Party Contexts
While SameSite cookies provide significant security benefits, they pose challenges when used in third-party contexts, such as advertising or authentication across multiple websites.
Key challenges include:
- Cross-Site Tracking: Third-party cookies (e.g., from advertisers or analytics providers) are often blocked by browsers when using SameSite=Strict or Lax, disrupting user tracking across websites.
- Cross-Origin Authentication: Sites that use cookies for authentication across multiple domains may encounter issues when cookies are restricted by SameSite rules, making it harder to share session data across subdomains or with external services.
- SameSite=None Requires Secure: Cookies set to SameSite=None need to be sent over HTTPS, which can complicate setups for non-secure websites or services.
- Legacy Browser Support: Older browsers may not fully support SameSite enforcement, leading to inconsistent behavior across different user bases.
For websites that rely on third-party cookies, developers need to carefully plan their implementation to ensure that SameSite cookies do not break essential functionalities while maintaining security.
Also Read: How to handle Cookies in Selenium WebDriver
Real-World Use Cases for SameSite Cookies
SameSite cookies are essential for ensuring security and usability across a range of real-world applications. Below are some common use cases:
- User Authentication: SameSite cookies help maintain secure user sessions by ensuring that session cookies are only sent in same-site requests, preventing cross-site hijacking.
- Shopping Cart Persistence: E-commerce websites use SameSite cookies to remember items added to the shopping cart across pages, while also preventing malicious third-party sites from modifying cart contents.
- Personalization: Websites can use SameSite cookies to store user preferences, such as language or theme settings, ensuring a personalized experience without risking data exposure.
- Cross-Site Services: When third-party services (like social login or ad services) need to share cookies across sites, SameSite cookies ensure proper control over cookie sharing to prevent security breaches.
These use cases highlight how SameSite cookies help maintain security while improving user experience.
Best Practices for Using SameSite Cookies
To ensure security and functionality, developers should follow these best practices when implementing SameSite cookies:
- Set SameSite to Lax or Strict: Use SameSite=Lax for cookies that need to be sent in top-level navigations and SameSite=Strict for highly sensitive cookies, such as those used in banking or account management.
- Use SameSite=None with Secure: When using SameSite=None (for cross-site functionality), always pair it with the Secure flag to ensure cookies are transmitted only over HTTPS.
- Add the HttpOnly Flag: Protect cookies from being accessed by JavaScript by marking them with the HttpOnly attribute, reducing the risk of XSS attacks.
- Limit Cookie Scope: Use Domain and Path attributes to restrict cookies to specific parts of your site or subdomains, minimizing exposure.
- Monitor Browser Compatibility: Regularly test cookies across browsers to ensure consistent behavior and functionality, especially with new SameSite enforcement.
These practices ensure that cookies are both secure and effective for a wide range of use cases.
Learn More: How to use Cypress Clear Cookies Command?
How SameSite Affects User Sessions and Privacy
SameSite cookies directly impact both user sessions and privacy by controlling when cookies are sent with requests. Here’s how it works:
- Session Security: SameSite cookies help protect session cookies from being sent in cross-site requests, which prevents unauthorized access or session hijacking by malicious websites.
- Privacy Control: By limiting cookie sharing between sites, SameSite enhances privacy by preventing third-party trackers from accessing session data without the user’s consent.
- Cross-Site Functionality: While SameSite improves security, it can affect third-party services like social logins or embedded widgets, as they rely on cookies being sent across different sites.
Overall, SameSite cookies provide a critical balance between enhancing privacy and ensuring smooth, secure user interactions across websites.
Debugging and Testing SameSite Cookies
Testing and debugging SameSite cookies is crucial for ensuring that cookies are properly configured and functioning as expected across different browsers and environments.
Tools like DevTools and Request Interceptors help streamline this process by providing direct insights into cookie interactions and modifications.
Using DevTools
Browsers like Chrome and Firefox offer built-in DevTools to inspect and debug cookies, including the SameSite attribute.
Steps to use DevTools for SameSite cookie debugging:
- Open DevTools (Right-click > Inspect or press Ctrl+Shift+I).
- Navigate to the Network tab and reload the page.
- Click on a network request and select Cookies in the request headers section.
- Look for cookies with the SameSite attribute to verify their behavior.
DevTools provide a simple, real-time way to check if cookies are being set and transmitted according to the expected SameSite policy.
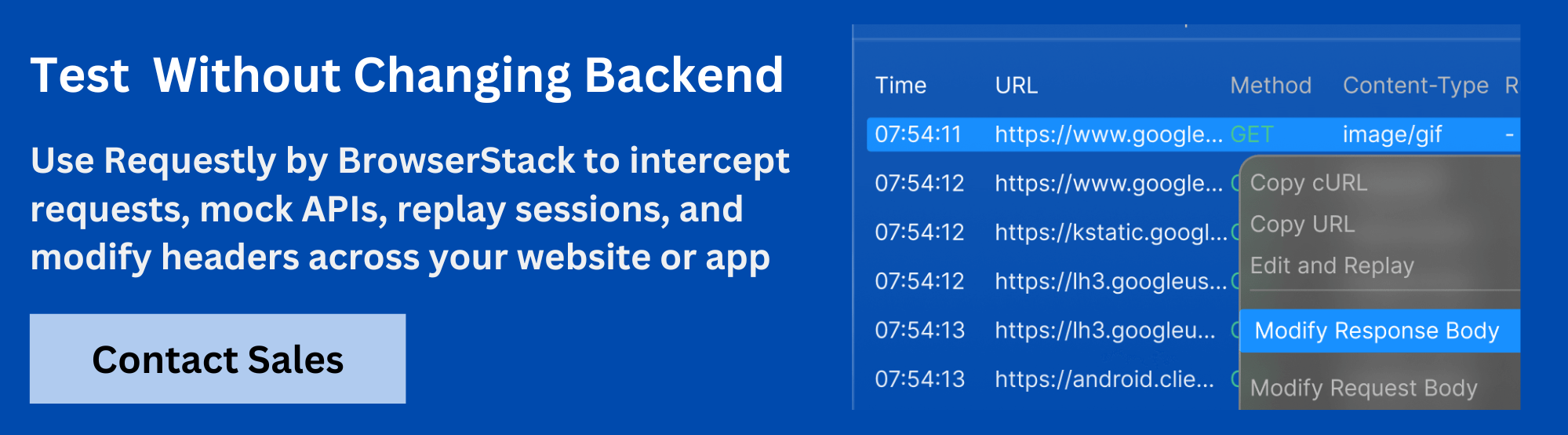
Using Request Interceptors
For more advanced cookie testing, Requestly HTTP Interceptor allows developers to intercept and modify HTTP requests directly in the browser, providing deeper control over SameSite cookies.
Benefits of using Requestly for SameSite cookie testing:
- Modify Cookie Values: Test how cookies behave by changing values or SameSite settings before sending the request.
- Block or Redirect Requests: Intercept requests with specific cookie conditions and block or modify them to simulate different user states.
- Real-Time Debugging: Adjust cookies live in the browser, making it easy to troubleshoot issues related to SameSite enforcement.
Common Issues with SameSite Cookies
While SameSite cookies offer significant security benefits, they can also introduce several challenges. Common issues include:
- Inconsistent Cross-Browser Support: Different browsers may enforce SameSite rules differently, especially older versions.
- Cross-Domain Authentication Failures: Third-party services or cross-origin authentication can break if SameSite is too restrictive.
- SameSite=None Requires Secure: When using SameSite=None, cookies must be sent over HTTPS, which can complicate setup for non-secure sites.
- Broken Third-Party Integrations: Services like social login or embedded content may not function correctly when SameSite cookies block cross-site cookie sharing.
Understanding these challenges helps in addressing issues proactively during development and testing.
Conclusion
SameSite cookies are an essential tool for improving web security by preventing CSRF and controlling cookie behavior across sites. They help ensure that cookies are only sent in the right contexts, protecting user sessions and privacy.
While configuring and testing SameSite cookies requires attention to detail. By following best practices, developers can ensure their applications are both secure and functional, providing a seamless user experience.