The DELETE method is a key component of RESTful APIs, used to remove resources from a server. Understanding how it works, when to use it, and how to test it is crucial for building secure and efficient web applications.
Overview
Key Characteristics Of The DELETE Method
- Purpose: Used to permanently remove a specific resource from the server.
- Idempotency: Repeating a DELETE request has the same effect as a single request, the resource stays deleted.
- Request Body: Typically not required, as the URI defines the resource. Some APIs may accept a body for conditional deletions.
- Response Codes: Common responses include 200 OK, 202 Accepted, or 204 No Content, depending on the server’s handling.
- Resource Identification: Targets a single resource, not a collection. Deleting a parent may also remove related sub-resources.
- Server Behavior: Support for DELETE may vary across APIs and server configurations.
- Security: Requires strict authentication and authorization to prevent unauthorized deletions.
This guide covers its purpose, syntax, best practices, and real-world usage to help developers implement DELETE requests effectively.
What is the DELETE Method in HTTP
The DELETE method is an HTTP request used to remove a specific resource from a server. In REST APIs, it represents the delete operation in CRUD, allowing clients to request the permanent removal of data identified by a unique URL.
Although it can affect server data, repeating a DELETE request for the same resource does not change the outcome. If the resource is already deleted, additional requests will have no further effect.
Must Read: Life Cycle of an HTTP Request
Purpose and Function of DELETE Requests
DELETE requests are designed to request the removal of a resource from the server. When issued, the server processes the request and deletes the targeted data if valid.
Key functions include:
- Managing outdated or unwanted data
- Ensuring consistency by maintaining only active resources
- Supporting automation in systems where cleanup is required
Note: DELETE is idempotent, meaning repeating the request does not change the result beyond the initial action. It helps developers maintain server-side data hygiene efficiently.
Syntax and Format of DELETE Method
DELETE requests are structured with a URI that specifies the resource to be deleted. Most APIs do not require a request body, but headers like authentication tokens may be included.
Example Syntax:
DELETE /items/123 HTTP/1.1 Host: api.example.com Authorization: Bearer <token>
Key elements:
- HTTP Method: DELETE
- Target URI: Specifies the resource
- Headers: May include authorization or content-type
- Body: Usually not needed, unless specified by the API
The server typically returns a status code such as 200 OK or 204 No Content to confirm deletion
How DELETE Method Works in REST Architecture
In REST architecture, each resource is identified by a unique Uniform Resource Identifier (URI). When a DELETE request is sent to a specific URI, the server processes it and removes the corresponding resource, if it exists.
DELETE requests are handled entirely on the server side. The client does not need to know how the deletion is implemented; it only needs to target the correct URI. After a successful DELETE operation, the server typically responds with a status code such as 200 OK, 202 Accepted, or 204 No Content.
REST APIs rely on stateless communication. This means each DELETE request must contain all the information needed to process it, without relying on previous interactions.
Must Read: HTTP Methods: GET vs POST vs PUSH
DELETE vs PUT vs POST vs GET: Key Differences
This comparison highlights how each method is used for specific operations within RESTful services. DELETE is uniquely responsible for removing resources, while others focus on reading, creating, or updating them.
| HTTP Method | Purpose | Data Affected | Idempotent | Typical Use Case |
|---|---|---|---|---|
| GET | Retrieve data | No changes to data | Yes | Fetch user profile or list of products |
| POST | Submit new data | Creates new resource | No | Register user or create a blog post |
| PUT | Update or replace existing data | Overwrites entire record | Yes | Update user profile or settings |
| DELETE | Remove existing data | Deletes target resource | Yes | Delete user account or remove a comment |
Common Use Cases Of DELETE Method In APIs
DELETE is commonly used across web applications, enterprise systems, and API-driven platforms. Here are a few typical scenarios:
- User Account Removal: Deleting an inactive or requested user profile from the system.
- Deleting Comments or Posts: Removing user-generated content in social platforms or blogs.
- Cleaning Up Test Data: Erasing temporary data used during testing or automation.
- Inventory Management: Removing discontinued items from product databases.
- Revoking API Tokens: Deleting expired or unused authentication tokens for security.
Each use case reflects how DELETE helps maintain data accuracy and system efficiency.
Response Codes Returned From DELETE Method
When a DELETE request is processed, the server responds with an HTTP status code that indicates the outcome of the operation. These are the most commonly returned codes:
- 200 OK: The resource was successfully deleted, and a confirmation message may be included in the response.
- 202 Accepted: The request was received and will be processed, but the deletion is not yet complete.
- 204 No Content: The resource was deleted successfully, but no content is returned in the response.
- 404 Not Found: The resource specified in the URI does not exist.
- 401 Unauthorized or 403 Forbidden: The client does not have the necessary permissions to perform the delete operation.
DELETE Request Headers And Body Requirements
DELETE requests are generally straightforward, but certain headers may be required depending on the API’s configuration.
Common Headers:
- Authorization: Used to validate the user’s identity with a token or API key.
- Content-Type: Specifies the format of any included data (if applicable).
- Accept: Indicates the expected format of the response (e.g., application/json).
Request Body:
Most DELETE requests do not require a body. However, some APIs may allow optional metadata to be sent in the body to control how the deletion is handled, such as soft deletes or conditional deletes. If a body is used, the API documentation should clearly define its structure.
Security Implications of using DELETE Requests
Because DELETE requests can permanently remove data, they must be secured to prevent accidental or malicious actions.
Key Security Considerations:
- Authentication and Authorization: Always require proper credentials before allowing a DELETE operation.
- Rate Limiting: Prevent abuse by limiting how many DELETE requests a client can send in a given time frame.
- Role-Based Access Control: Ensure only users with appropriate permissions can delete sensitive resources.
- CSRF Protection: Use anti-forgery tokens to prevent unauthorized cross-site request forgery attacks.
- Logging and Auditing: Maintain logs of all DELETE requests to monitor and trace any unexpected data removals.
Troubleshooting Common DELETE Method Errors
Errors in DELETE requests can stem from incorrect URIs, missing headers, or server-side misconfigurations. Identifying the source quickly helps ensure smooth API interactions.
Common Errors and Fixes:
- 404 Not Found: The specified resource does not exist. Double-check the URI or ensure the resource has not already been deleted.
- 401 Unauthorized / 403 Forbidden: The client lacks valid credentials or permission. Confirm that the Authorization header is correct and the token is active.
- 405 Method Not Allowed: The server does not support DELETE for the targeted endpoint. Check the API documentation to verify supported methods.
- 500 Internal Server Error: An unexpected error occurred on the server. Review server logs and validate the request structure.
Best Practices for DELETE Method Implementation
Following best practices for DELETE requests ensures consistent behavior, improves security, and simplifies debugging.
- Use Unique Identifiers in URIs: Always specify the exact resource to delete using a unique ID, such as /users/123.
- Avoid Including Sensitive Data in the Body: Since DELETE requests rarely require a body, limit its use unless explicitly supported.
- Make Use of Proper Status Codes: Return appropriate responses like 204 No Content to confirm successful deletion.
- Enforce Access Control: Implement strict authentication and authorization to prevent unauthorized data deletion.
- Log Every DELETE Operation: Maintain server-side logs for audit trails and to trace issues when needed.
How to Intercept and Test DELETE Requests Effectively
Testing DELETE requests is critical for ensuring that API endpoints work as expected and do not unintentionally remove the wrong data.
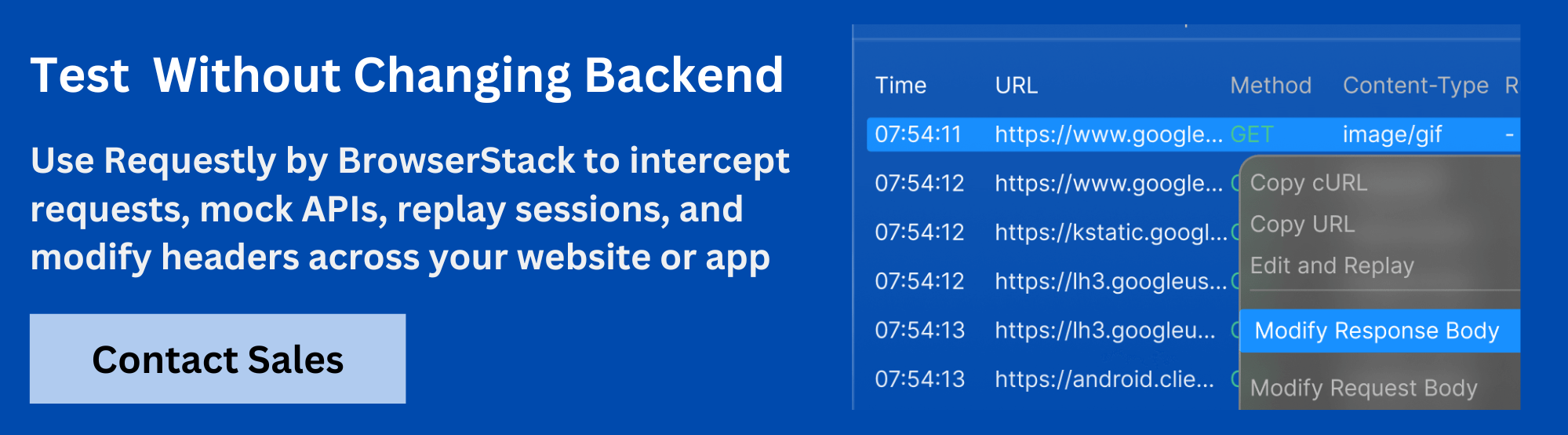
Intercept DELETE Requests Using Requestly HTTP Interceptor
Requestly offers a powerful and user-friendly way to test DELETE requests directly in the browser. With its HTTP Interceptor, developers can:
- Capture and Inspect DELETE requests as they happen
- Modify Request Headers or Payloads without changing source code
- Simulate DELETE Scenarios by altering endpoints or injecting delays
- Block or Redirect DELETE calls to avoid hitting live servers during testing
This makes Requestly ideal for front-end developers and testers who need full control over network traffic during API debugging or QA.
Conclusion
The DELETE method is essential in RESTful APIs for efficiently removing outdated or unnecessary resources. When used correctly, it supports cleaner architecture, improved user control, and better application performance.
Understanding its syntax, behavior, and security considerations is essential for both frontend and backend teams. Equally important is testing these requests to ensure they function as expected in different environments.
Using tools like Requestly HTTP Interceptor simplifies the testing and debugging process, enabling teams to intercept, modify, or block DELETE requests in real time without touching production code.