HTTP (Hypertext Transfer Protocol) is the backbone of how data moves across the web. It defines the rules for communication between applications and systems.
Overview
What is HTTP?
HTTP (Hypertext Transfer Protocol) is a request-response protocol used to send and receive data between a client (like a browser or API client) and a server. It runs over TCP/IP and defines how messages are structured and handled.
Why is HTTP Used?
- Fetch resources: Load HTML, CSS, JavaScript, images, or files from a server
- Submit data: Send form inputs or payloads in API calls
- Control behavior: Use headers and methods to manage caching, redirects, content types, and authentication
- Drive APIs and services: Enable communication across microservices, mobile apps, and third-party integrations
How Does HTTP Work?
- Client sends a request: Includes a method (like GET or POST), a URL, headers, and sometimes a body.
- Server processes the request: Matches it to a route or resource, and executes logic.
- Server returns a response: Includes status code, headers, and optionally a body with content.
This article explains how HTTP works at every level, from basic requests to how headers, status codes, and encryption impact system behavior.
What is HTTP, and Why Is It Used?
HTTP stands for Hypertext Transfer Protocol. It’s a request-response protocol that powers communication between clients (usually browsers or applications) and servers. It works over TCP/IP and defines how messages are formatted and transmitted.
HTTP is used for:
- Fetching content: Requesting HTML, images, CSS, JavaScript, or any other resource from a server.
- Sending data: Submitting form data or making API requests using POST, PUT, or PATCH.
- Controlling behavior: Using methods and headers to cache responses, handle redirects, or specify content types.
Note: HTTP is stateless by design, meaning each request is independent and doesn’t retain previous request data unless managed with mechanisms like cookies or tokens.
The Evolution of HTTP: From 0.9 to HTTP/3
HTTP has evolved to improve performance, reliability, and support for modern use cases. Here’s a breakdown of how it’s changed:
- HTTP/0.9: The earliest version, supported only GET requests and returned raw HTML. No headers, no status codes.
- HTTP/1.0: Introduced headers, status codes, and more request methods like POST and HEAD. Each connection handled one request.
- HTTP/1.1: Persistent connections (keep-alive), chunked transfer encoding, and caching headers became standard.
- HTTP/2: Multiplexing over a single TCP connection, header compression (HPACK), binary framing layer.
- HTTP/3: Built on QUIC over UDP. Avoids TCP’s head-of-line blocking. Faster handshake, integrated TLS 1.3, better suited for mobile and high-latency networks.
Most real-world systems today primarily use HTTP/1.1, with HTTP/2 also widely adopted. HTTP/3 adoption is growing, particularly among performance-oriented platforms and content delivery networks (CDNs), but it is not yet as widely deployed.
What Is HTTPS and How Does It Secure HTTP?
HTTPS is the secure version of HTTP. It adds encryption and authentication to the communication between a client and server using TLS (Transport Layer Security).
When a browser or tool makes an HTTPS request, it begins with a TLS handshake. This handshake negotiates cryptographic parameters and verifies the server’s certificate. Only after that is complete does the actual HTTP request get sent over the secure channel.
HTTPS has three properties:
- Confidentiality: Data is encrypted, which prevents others from reading request or response contents in transit.
- Integrity: TLS checks that the data hasn’t been modified or tampered with.
- Authentication: The server’s certificate confirms its identity to the client. If the certificate is invalid or expired, the client blocks the request.
How HTTP Works: Client-Server Communication Model
The HTTP lifecycle starts when a client sends a request to a server. The server processes the request and returns a response.
Basic flow:
- Client sends a request: Includes method (e.g., GET, POST), target URL, headers, and optionally a body.
- Server processes the request: Matches it to a route, performs logic, and generates a response.
- Server sends a response: Includes status code, headers, and optionally a body.
Clients can be browsers, mobile apps, backend services, or testing tools. Servers might be simple HTTP servers, reverse proxies, or application gateways.
Read More: Life Cycle of an HTTP Request
HTTP Methods and Status Codes Explained
HTTP methods define what kind of operation the client wants to perform. Status codes tell the client the result of that operation.
Common HTTP Methods
These are standard request types used by clients to interact with servers over the web.
- GET: Retrieve data from the server without modifying it.
- POST: Submit data to the server, usually resulting in a new resource or side effect.
- PUT: Replace an existing resource with the data provided.
Read More: HTTP Methods: GET vs POST vs PUSH
- PATCH: Partially update a resource.
- DELETE: Remove a resource from the server.
- HEAD: Same as GET, but returns only the headers.
- OPTIONS: Returns the supported methods and options for a specific URL.
Common HTTP Status Codes
These HTTP status codes indicate the result of an HTTP request and help diagnose responses from the server.
- 200 OK: The request was successful.
- 201 Created: The resource was created successfully.
- 204 No Content: Request succeeded, but no content was returned.
- 301/302 Redirect: The resource has been moved to a different URL.
- 400 Bad Request: The request was invalid or malformed.
- 401 Unauthorized: Authentication is required and has failed or not been provided.
- 403 Forbidden: The server understands the request but refuses to authorize it.
- 404 Not Found: The requested resource could not be found.
- 500 Internal Server Error: A generic error occurred on the server.
Read More: HTTP Status Codes: Explained
Understanding HTTP Headers and Content Negotiation
HTTP headers carry metadata in both requests and responses. They influence routing, caching, authentication, compression, language selection, and content formatting. Most testing scenarios, especially around APIs or browser behavior, rely on correct header handling.
Headers fall into categories:
- General headers apply to both HTTP requests and responses and provide general information about the message. Examples include Cache-Control (controls caching behavior) and Connection (manages connection options like keep-alive).
- Request headers are set by the client to inform the server about its preferences, capabilities, or identity. Examples include Accept (specifies acceptable media types), User-Agent (identifies the client software), and Authorization (sends credentials for authentication).
- Response headers are sent by the server to describe the response and how it should be handled by the client. Examples include Content-Type (defines the media type of the response), Set-Cookie (sets a cookie on the client), and Location (used for redirects).
- Entity headers provide metadata about the message body and are used in both requests and responses when a body is present. Examples include Content-Length (size of the body in bytes) and Content-Encoding (compression or encoding used, like gzip).
Content negotiation is the process in which the client and server decide on the best representation of a resource to exchange. It is based on request headers such as:
- Accept: Tells the server what content types (e.g., application/json, text/html) the client prefers.
- Accept-Encoding: Specifies supported compression algorithms (e.g., gzip, br).
- Accept-Language: Lists preferred languages with optional weighting (q=0.8).
- Content-Type: Indicates the media type of the request or response body.
If negotiation fails, the server may return a 406 Not Acceptable response. In real systems, fallback logic is often implemented to avoid hard failures.
Testing implications include verifying:
- Headers are explicitly and correctly sent in requests, especially in APIs where Content-Type and Authorization affect routing and security.
- Server behavior changes based on header variations, such as delivering compressed vs uncompressed content, or returning localized responses based on Accept-Language.
- Intermediate systems (CDNs, proxies) do not strip or alter important headers that impact downstream logic.
Most request mismatches, failed compression, or localization bugs are due to overlooked or incorrectly handled headers.
Why Test on HTTP?
HTTP controls how systems behave when exchanging data. From method usage to header rules, every piece of HTTP contributes to the application’s behavior. Developers and testers need to treat HTTP as an active interface, not just transport.
Here are some reasons to actively test HTTP behavior:
- Behavior shifts based on method: A GET should not modify data. A PUT should be idempotent. These rules need verification to avoid bugs and side effects.
- Headers impact functionality: Incorrect Content-Type, missing Authorization, or poorly set Cache-Control can break features, expose data, or affect user experience.
- Status codes affect flows: UI logic, retries, redirects, and error messages all depend on the right status code being returned. Incorrect status codes lead to broken behavior or a misleading UX.
- Intermediate systems alter traffic: CDNs, reverse proxies, and API gateways often modify or drop headers. This can change the behavior between staging and production.
- Security testing depends on HTTP correctness: Request smuggling, cache poisoning, and session hijacking all exploit how HTTP is parsed.
In testing workflows, HTTP needs to be validated across environments. Unit tests might confirm correct methods and response codes. Integration tests should validate headers, redirects, and negotiation logic. In real-world usage, manual testing or tools like Requestly can help explore and patch these HTTP behaviors without changing code.
Security Risks to Watch When Working with HTTP
Many security issues in web applications come from how HTTP messages are parsed or handled. These issues often involve incorrect assumptions about headers, trust boundaries, or the behavior of intermediaries like proxies and CDNs.
- HTTP request smuggling is one such threat. It happens when different servers in the request chain interpret headers like Content-Length and Transfer-Encoding differently. This can let attackers bypass filters, hide requests, or interfere with legitimate traffic.
- Header injection allows attackers to insert values into HTTP headers if user input is not properly sanitized. This can be used to manipulate downstream behavior, poison caches, or exploit redirect flows.
- Session hijacking is another risk. If session tokens are not securely stored, transmitted, or invalidated, attackers can impersonate users. Cookies without secure flags, tokens in URLs, or headers sent over HTTP are common causes.
- Cache poisoning happens when untrusted input is stored in shared caches. If caching rules are not strict, private or malicious content might be served to unintended users.
When HTTPS is not used correctly, man-in-the-middle attacks become possible. Attackers can intercept, read, or alter traffic between clients and servers. Even with HTTPS enabled, expired certificates, weak protocols, or mixed content can weaken protections.
Why HTTP Matters in APIs and Microservices
HTTP defines how services exchange data in modern architectures. For APIs and microservices, every detail, method, path, status code, and header affects how services understand and trust each other.
In microservice environments, where multiple services handle specific tasks independently, testing HTTP behavior ensures that each service communicates correctly and handles edge cases predictably.
Here are some more reasons why HTTP is important in APIs and microservices.
- Authentication Headers: HTTP headers ensure secure communication by carrying tokens and credentials that services use to authenticate requests. This is crucial for verifying that only authorized services can interact with APIs or microservices.
- Method Behavior: Each HTTP method (GET, PUT, PATCH, DELETE) plays a specific role in the interaction between services. Proper use ensures that the right actions are performed, maintaining consistency and preventing unintended side effects in microservices.
- Versioning Strategy: HTTP headers and paths help manage API versions. A proper versioning strategy ensures that updates to one service don’t break interactions with others, allowing smooth transitions and backward compatibility.
- Rate limiting and throttling: HTTP headers like Retry-After and status code 429 are critical in controlling the number of requests a service can handle, protecting systems from overload and ensuring fair usage in microservices environments.
- Schema and Format Validation: The structure and format of the response body are defined by HTTP responses. Ensuring that these match the expected schema and content types is vital for maintaining consistency and data integrity across services.
Debugging HTTP Issues in Real Environments
When requests fail or don’t behave as expected, debugging HTTP traffic is critical. Here’s what testers and developers commonly deal with:
- Mismatched headers: Incorrect Content-Type, missing Authorization, or unsupported encodings can cause failed requests.
- Redirect loops: Misconfigured status codes or conflicting redirect rules can trap requests in infinite loops.
- Uncompressed responses: Improper server settings lead to large payload sizes.
- CORS failures: Cross-origin requests blocked due to missing or invalid CORS headers.
- Timeouts and dropped connections: Caused by network delays, server load, or missing keep-alive headers.
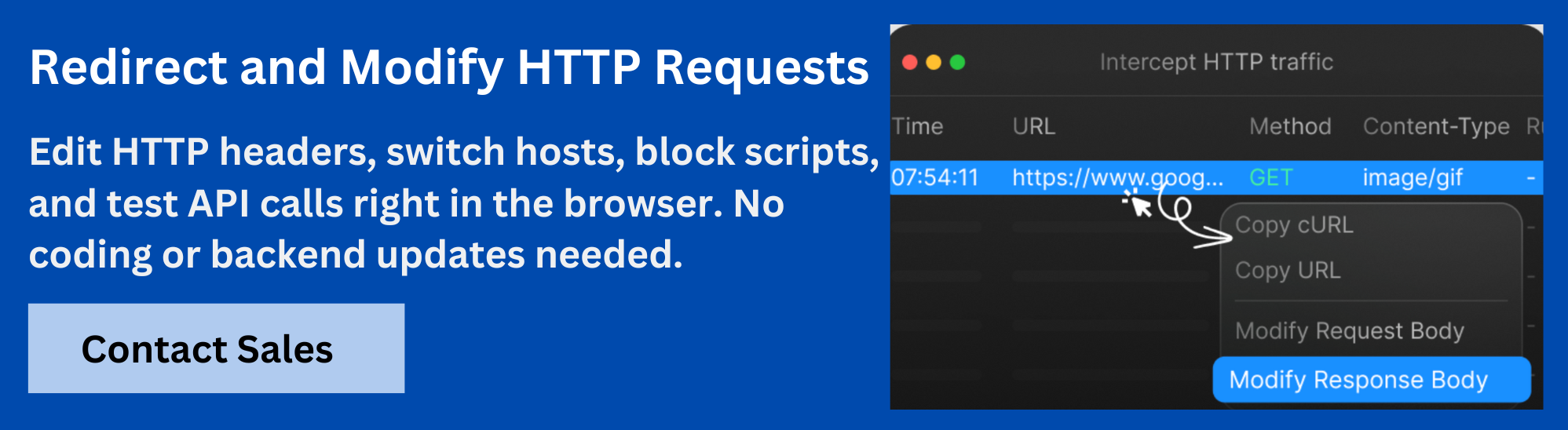
Requestly by BrowserStack is designed to give you complete visibility and control over the entire HTTP exchange. It runs as a browser extension or desktop app and allows you to inspect, modify, and simulate network behavior without changing your code or backend configuration.
Here is what you can do with Requestly:
- Intercept and inspect requests: View request and response headers, status codes, and payloads in real time.
- Redirect URL: Test how different header values or paths affect server behavior.
- Mock APIs: Return custom responses without needing a backend to be available.
- Simulate failure conditions: Delay, block, or alter requests to reproduce edge cases or network instability.
This is especially useful during frontend-backend integration or when validating how systems behave under broken or inconsistent network conditions.
Conclusion
HTTP is the core protocol that defines how clients and servers exchange data. The structure of each request and response, such as methods, headers, status codes, and encoding, affects what gets sent, what gets blocked, and what gets interpreted incorrectly.
For teams working on frontend-backend integration, testing distributed APIs, or debugging production issues, having visibility into HTTP traffic is essential. Requestly provides that visibility. It allows developers and testers to intercept, inspect, modify, and simulate HTTP behavior without needing changes to server-side code.