Cross-Site Scripting (XSS) attacks are among the most common browser-based security risks. The X-XSS-Protection header was one of the early methods to safeguard users from these attacks.
Overview
What Is the X-XSS-Protection Header?
The X-XSS-Protection header is an HTTP header used to enable or disable the browser’s built-in XSS filter. It instructs the browser to detect and block malicious scripts injected into web pages to reduce the chances of code execution through reflected XSS vulnerabilities.
Why Is the X-XSS-Protection Header Used?
It provides a basic line of defense against common XSS attacks by controlling how browsers handle suspicious scripts:
- Filter activation: Enables the browser’s native XSS filter to scan incoming scripts for malicious patterns.
- Attack blocking: Stops the page from rendering if a potential XSS attempt is detected.
- Content sanitization: In some configurations, the browser automatically modifies unsafe content to prevent execution.
Is the X-XSS-Protection Header Still Relevant?
Although modern browsers have deprecated this header in favor of the Content Security Policy (CSP) header, X-XSS-Protection still offers value in older environments. It can serve as a fallback for legacy browsers where CSP support is limited or unavailable.
This article explains how the X-XSS-Protection header works, why it matters, and how to test it effectively with Requestly.
What Is X-XSS-Protection?
The X-XSS-Protection header is a browser security feature designed to detect and mitigate reflected Cross-Site Scripting (XSS) attacks. It activates the browser’s built-in XSS filter, which scans incoming requests and responses for malicious scripts.
When a potential XSS attack is detected, the browser can either block the page entirely or sanitize the unsafe content before rendering it. This helps reduce the risk of script injection in older browsers that still support this header.
Common configuration values include:
- 0: Disables XSS protection.
- 1: Enables XSS protection.
- 1; mode=block: Enables protection and blocks the page when an attack is found.
- 1; report=URL: Enables protection and sends a violation report to the specified endpoint.
Note: The X-XSS-Protection header is now deprecated in most modern browsers and has been replaced by the Content-Security-Policy (CSP) header for stronger and more reliable XSS protection.
Why Is X-XSS-Protection Important?
X-XSS-Protection played a key role in enhancing browser-based security before modern standards like CSP became common. It offered a straightforward way to minimize the impact of XSS attacks, especially for applications running on older browsers.
Here are the main reasons it was considered important:
- Early browser defense: Provided a built-in layer of protection without requiring complex configurations or external tools.
- Reduced reflected XSS risk: Helped detect and block scripts that tried to reflect user input back into a webpage.
- Improved user safety: Prevented execution of injected scripts that could steal cookies, session tokens, or personal information.
- Simple to implement: Required only one response header, making it easy for developers to activate basic XSS filtering.
Types of XSS Attacks
Understanding the different types of Cross-Site Scripting (XSS) attacks helps explain why headers like X-XSS-Protection were introduced. XSS attacks generally exploit vulnerabilities in web applications to execute malicious scripts in users’ browsers.
Here are the main categories:
- Reflected XSS: Malicious scripts are injected via URL parameters or form inputs and executed immediately when the page loads. For example, a search query containing a script that runs upon submission.
- Stored XSS: Malicious code is permanently stored on the server, such as in a database or comment section, and executed whenever a user accesses the affected page.
- DOM-Based XSS: Scripts manipulate the Document Object Model (DOM) on the client side without involving the server, causing unintended script execution.
- Self-XSS: Requires the user to intentionally execute scripts, often through social engineering or tricking them into pasting code into their browser console.
Purpose of X-XSS-Protection Header
The X-XSS-Protection header was introduced to provide a targeted defense against reflected XSS attacks in browsers. Unlike application-level input validation, it operates at the browser layer, giving users a fallback protection mechanism against malicious scripts that might bypass server-side safeguards.
Here’s a closer look at its purposes and practical impact:
- Activate browser-level scanning: Instructs the browser to analyze incoming HTML and script content for known XSS attack patterns, preventing unsafe code execution before it affects the user.
- Block malicious pages proactively: When the mode=block option is enabled, the browser prevents the page from rendering entirely, stopping an attack without relying on the developer to sanitize content manually.
- Prevent script-based data theft: Helps mitigate attacks where malicious scripts aim to capture cookies, session tokens, or local storage data by stopping execution in real time.
- Provide early warnings for attacks: Some configurations allow sending reports to monitoring endpoints, giving security teams actionable data on attempted XSS exploits.
- Support legacy browser security: Even as modern browsers shift to CSP, X-XSS-Protection remains relevant for environments where older browsers are in use, offering a basic, yet important, layer of defense.
Content Security Policy (CSP) vs. X-XSS-Protection
While X-XSS-Protection offers basic client-side defense, Content Security Policy (CSP) provides a far more robust and flexible approach to preventing XSS attacks. CSP allows developers to define which sources of scripts, styles, and other resources are trusted, effectively controlling what the browser is allowed to execute.
Here’s a detailed comparison:
| Feature | X-XSS-Protection | Content Security Policy (CSP) |
| Scope of Protection | Targets reflected XSS attacks | Protects against reflected, stored, and DOM-based XSS |
| Granularity | Simple on/off or block mode | Fine-grained control over scripts, styles, and resources |
| Reporting | Basic reporting in some browsers | Detailed violation reports to a specified endpoint |
| Browser Support | Mainly older, now-deprecated browsers | Widely supported across modern browsers |
| Bypass Resistance | Can be bypassed in certain scenarios | Enforces strict rules; harder to bypass |
| Implementation Complexity | Very simple to implement (single header) | Requires planning and careful configuration |
Best Practices for X-XSS-Protection
Even though X-XSS-Protection is deprecated, applying it correctly can help secure older browsers and complement modern security measures. Here are in-depth best practices:
- Enable selectively with purpose: Use X-XSS-Protection: 1; mode=block only for browsers that lack full CSP support. This ensures that the header actively blocks detected XSS without interfering with modern security policies in newer browsers.
- Combine with Content Security Policy (CSP): Treat X-XSS-Protection as a fallback rather than a primary defense. CSP provides granular control over sources and scripts, while X-XSS-Protection covers older browsers that cannot enforce CSP effectively.
- Sanitize and validate inputs rigorously: Never depend solely on the browser filter. Apply strict server-side and client-side validation to prevent malicious scripts from entering the application in the first place. For example, escape user-supplied HTML and enforce type constraints on inputs.
- Avoid inline scripts and unsafe eval functions: Inline JavaScript increases the attack surface. By enforcing CSP directives like script-src ‘self’, developers can block unsafe scripts, making X-XSS-Protection more reliable in catching unexpected patterns.
- Monitor and log attempted attacks: If the header is configured with reporting, capture attempts to understand attack vectors. This data helps security teams identify patterns and strengthen other defenses.
Read More: What is the Content-Type Header?
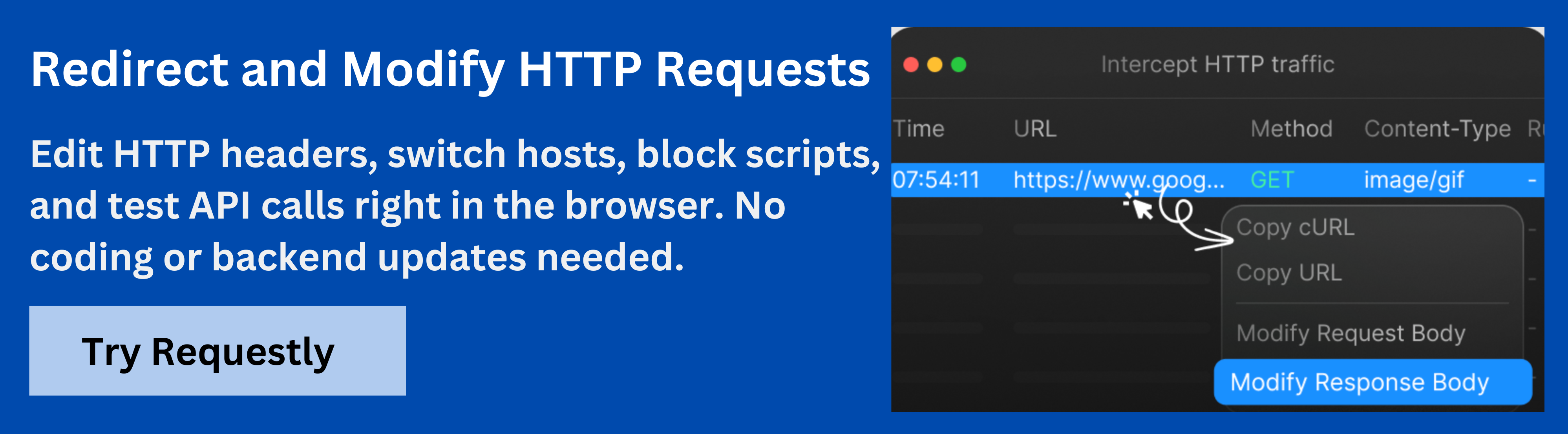
Why Use Requestly to Test X-XSS-Protection?
Requestlyis a browser extension and testing tool that allows developers to modify HTTP requests and responses in real time. It can intercept, add, remove, or edit headers and URL parameters without changing the server code, making it ideal for testing how web applications behave under different security configurations.
Using Requestly, you can simulate different X-XSS-Protection scenarios and verify how browsers respond to potential XSS attacks. This helps ensure that applications handle malicious scripts correctly and maintain layered defenses.
Steps to Test X-XSS-Protection with Requestly:
- Install Requestly: Add the Requestly browser extension and open the dashboard.
- Create a Modify Headers Rule: Select “Modify Headers” as the rule type, specify the URL pattern for your application, and choose to add or modify the X-XSS-Protection header.
- Set Header Values: Test different configurations: use 0 to disable the filter, 1 to enable it, and 1; mode=block to block malicious scripts entirely.
- Simulate CSP Scenarios: Optionally, create additional rules to adjust or remove Content-Security-Policy headers to test how your application behaves under stricter or relaxed script execution rules.
- Test Legacy Browser Behavior: Verify how older browsers that still support X-XSS-Protection respond to your configurations.
Important Considerations:
- Modern browsers have deprecated X-XSS-Protection in favor of CSP, so its impact is limited in current environments.
- Header testing should complement broader security practices, including rigorous input validation, output encoding, and content sanitization.
- Testing with Requestly should always be done in a controlled environment to prevent accidental exposure to live vulnerabilities.
- Use Requestly testing as part of a layered security strategy, and ensure XSS protection is enforced through multiple mechanisms, not just the header.
Conclusion
The X-XSS-Protection header was an early browser-based defense against reflected XSS attacks, providing a simple way to block or sanitize malicious scripts. While it is now deprecated in modern browsers and largely replaced by Content-Security-Policy, understanding its use and limitations remains important.
Requestly offers a practical way to test X-XSS-Protection and related headers by modifying HTTP requests and responses in real time. It allows developers to simulate different configurations, observe browser behavior, and validate layered XSS defenses.