Content Security Policy (CSP) is a security standard enforced via HTTP headers, protecting against XSS and other injection attacks. It works by controlling which sources a browser is allowed to load resources from, creating a whitelist for trusted content.
Overview
How Content Security Policy Works:
- HTTP Header: CSP is implemented by setting the Content-Security-Policy HTTP header.
- Directives: This header contains rules (directives) for resource loading, such as script-src for JavaScript or img-src for images.
- Whitelisting: Only resources from trusted sources are allowed, and any unapproved resources are blocked.
Example:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted-cdn.com;
This article talks about how Content Security Policy works, its importance in preventing security vulnerabilities, and how to implement and optimize it for better web protection.
What is Content Security Policy?
Content Security Policy (CSP) is a security standard that helps prevent attacks like Cross-Site Scripting (XSS) and data injection by restricting which resources a browser can load and execute on a website.
It lets web administrators define trusted sources for content through the Content-Security-Policy header, reducing the risk of malicious code running on web pages.
This helps ensure that only trusted content is executed, protecting both the website and its users.
Importance of Content Security Policy
A well-implemented Content Security Policy plays a vital role in web security for several reasons:
- Prevents Cross-Site Scripting (XSS): By restricting the sources from which scripts can be loaded, CSP reduces the risk of XSS attacks, which inject malicious scripts into trusted websites.
- Mitigates Data Injection Attacks: CSP ensures that only authorized data is processed, protecting sensitive user data.
- Reduces Malware Risk: Limiting where content can be loaded from helps prevent the inclusion of malicious resources, reducing the chance of malware injection.
- Improves Trust and Compliance: Implementing a robust CSP header demonstrates proactive security measures, helping to build trust with users and adhere to security standards like GDPR and HIPAA.
Also Read: What is Automated Penetration Testing
How Content Security Policy Works
Content Security Policy (CSP) works by specifying a set of rules in the Content-Security-Policy HTTP header, which tells the browser which content is allowed to load and execute.
Here’s how it works:
- Directives: CSP uses a series of directives that define the allowed sources for different types of content. For example:
- script-src: Specifies where JavaScript files can be loaded from.
- style-src: Defines trusted sources for stylesheets.
- img-src: Specifies which domains images can be loaded from.
- Policy Enforcement: When a browser receives a page with a CSP header, it checks the content against the specified policy. If any content attempts to load from an unauthorized source, it is blocked. For example, if a script tries to load from an untrusted source, the browser will prevent it from running.
- Reporting Violations: CSP also allows sites to report violations to a specified endpoint using the report-uri directive. This helps web administrators monitor and improve their policies over time.
Setting Up Content Security Policy: A Step-by-Step Guide
Setting up Content Security Policy is straightforward but requires careful attention to detail. Follow these steps:
- Define the Policy: Choose the directives you want to implement (e.g., script-src, style-src, img-src).
- Add the Content-Security-Policy Header: Add the Content-Security-Policy header to your HTTP responses, specifying the allowed sources for each resource type. Example:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted-cdn.com;
- Test the Policy: Start by using a report-only mode with the Content-Security-Policy-Report-Only header to log violations without enforcing them.
- Monitor and Refine: Continuously monitor your site for violations and adjust the policy as needed to balance security and functionality.
Common Content Security Policy Directives
Here are some of the most commonly used Content Security Policy directives:
- default-src: Specifies the default source for all content types (e.g., default-src ‘self’;).
- script-src: Defines trusted sources for JavaScript files (e.g., script-src ‘self’ https://trusted-cdn.com;).
- style-src: Specifies where CSS can be loaded from (e.g., style-src ‘self’ https://trusted-styles.com;).
- img-src: Defines allowed sources for images (e.g., img-src ‘self’ https://trusted-images.com;).
- connect-src: Limits where XMLHttpRequest, Fetch, and WebSocket connections can be made.
- font-src: Restricts the sources for fonts.
How Content Security Policy Protects Against Cross-Site Scripting (XSS)
Content Security Policy is a powerful tool to prevent Cross-Site Scripting (XSS) attacks by restricting where scripts can be loaded and executed from.
- Script Restrictions: By setting the script-src directive to only trusted sources (e.g., script-src ‘self’;), Content Security Policy blocks malicious scripts from executing, even if they’re injected into the page.
- Inline Script Blocking: Content Security Policy can disallow inline scripts (unsafe-inline), preventing attackers from injecting malicious JavaScript directly into the HTML.
- Strict Directives: With proper directives, Content Security Policy limits the sources for other content types (like images, fonts, etc.), reducing the attack surface for XSS.
- Content Security Policy mitigates the risk of XSS by ensuring that only scripts and resources from trusted sources are allowed to execute, keeping user data safe.
Implementing Content Security Policy in Different Web Applications
Implementing Content Security Policy (Content Security Policy) ensures secure data handling by controlling where resources are loaded from. The implementation varies depending on the application:
- Static Websites: Add the Content-Security-Policy header in server configurations or via meta tags in HTML.
- Single Page Applications (SPA): Use directives like script-src and connect-src to restrict where scripts and dynamic content can be loaded.
- APIs: Apply Content-Security-Policy to restrict API interactions, ensuring only trusted endpoints are used.
Adjust Content Security Policy directives according to your application’s needs for maximum security.
Testing and Validating Content Security Policy Headers
To ensure Content Security Policy headers are correctly implemented, follow these steps:
- Use Browser Developer Tools: Inspect the Content-Security-Policy header in the browser’s network tab to ensure it’s being applied properly.
- Report-Only Mode: Test policies by using Content-Security-Policy-Report-Only to log violations without enforcement.
- Test with Tools: Use Postman or curl to check the headers and validate their accuracy.
- CSP Validators: Utilize online tools to verify Content-Security-Policy configuration and test its effectiveness.
Testing helps ensure Content Security Policy functions as intended without causing disruptions.
Content Security Policy in Content Management Systems (CMS) like WordPress
In Content Management Systems (CMS) like WordPress, implementing Content Security Policy adds an extra layer of security. Here’s how to do it:
1. Plugins: Use security plugins (e.g., Wordfence Security) to easily configure Content-Security-Policy headers
2. Manual Configuration: Add the Content-Security-Policy header via the .htaccess file or a custom plugin.
Example:
Header set Content-Security-Policy "default-src 'self';"
3. Test and ensure that the Content-Security-Policy is working correctly to protect against XSS and other attacks.
Best Practices for Configuring Content Security Policy
Follow these best practices when configuring Content Security Policy:
- Start with Report-Only Mode: Use Content-Security-Policy-Report-Only to test and log violations without enforcing the policy.
- Be Specific with Directives: Define specific directives like script-src, img-src, rather than using broad directives.
- Avoid unsafe-inline and unsafe-eval: These values increase vulnerability. Use nonces or hashes for inline scripts if necessary.
- Whitelist Trusted Sources: Always specify trusted domains for external resources to prevent malicious content.
- Use Nonces for Inline Scripts: For added security, use nonces for inline scripts to ensure they’re trusted.
- Regular Updates: Periodically review and update your Content-Security-Policy as your website evolves.
Common Content Security Policy Errors and How to Troubleshoot Them
When setting up Content Security Policy (Content Security Policy), it’s important to ensure that the configuration is correct to prevent issues like blocked resources, security vulnerabilities, and poor performance.
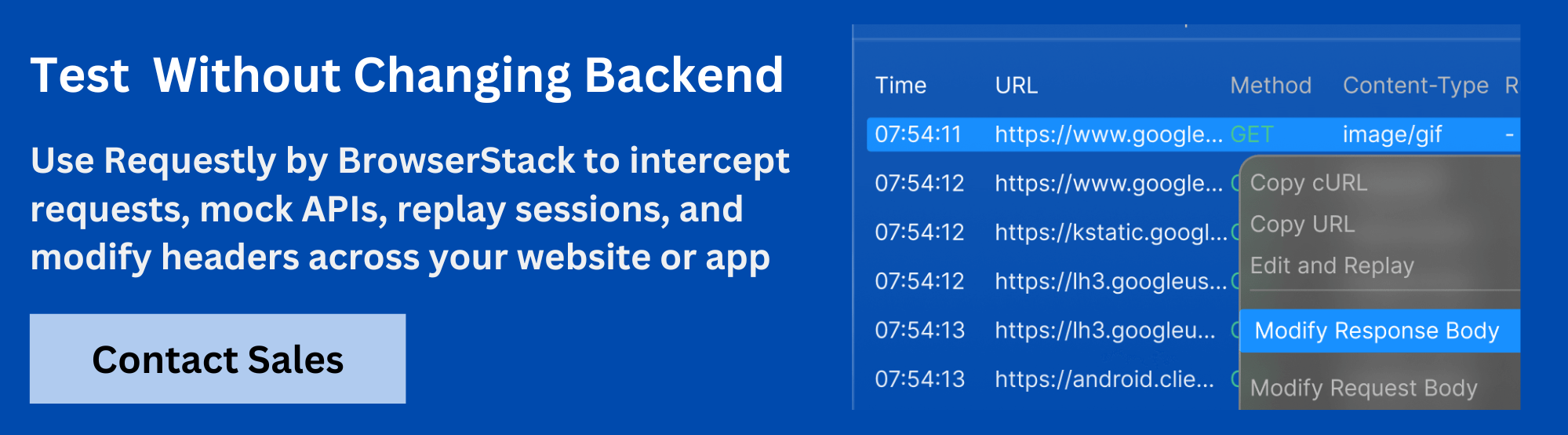
Requestly HTTP Interceptor can help developers by allowing real-time inspection and modification of Content-Security-Policy headers. It simplifies troubleshooting by enabling you to simulate different scenarios, identify errors, and optimize policies.
Here are common Content-Security-Policy errors and how to troubleshoot them:
- Blocked Resources: Resources, such as scripts or images, might be blocked if the Content Security Policy is too restrictive or the sources aren’t specified properly. With Requestly HTTP Interceptor, you can intercept and modify Content Security Policy headers in real-time, allowing you to test how changes impact resource loading and easily identify which resources are being blocked.
- Inline Script Blocking: Inline scripts can be blocked when the policy doesn’t allow unsafe-inline. This can be resolved by using nonces or hashes for inline scripts. Requestly HTTP Interceptor helps you test different variations of Content Security Policy and observe how the policy change allows inline scripts to execute without issues.
- Mixed Content Blocking: When a page served over HTTPS tries to load content (like scripts or images) over HTTP, it gets blocked. Ensure all resources are loaded via HTTPS. Requestly HTTP Interceptor allows you to simulate Content Security Policy violations and test how different mixed content scenarios behave, helping you confirm the proper blocking of mixed content.
CSP Reporting: Monitoring Violations and Enhancing Security
Content Security Policy also provides a reporting feature, allowing you to monitor violations of the policy in real-time.
This helps improve security by detecting unauthorized resource loading and script execution attempts. Here’s how you can implement and use CSP Reporting effectively:
- Violation Reporting: By setting the report-uri or report-to directive in the Content-Security-Policy header, violations are reported to a specified endpoint. This allows web administrators to track any potential threats.
- Reviewing Reports: The violation reports contain details about blocked resources, including which URLs were blocked and the reason. By reviewing these reports, you can identify areas of improvement in your security settings.
- Enhancing Security: By analyzing CSP violation reports, you can continuously refine your security settings and prevent new attacks.
Challenges in Adopting Content Security Policy
Adopting Content Security Policy (Content Security Policy) can be challenging, especially for complex web applications with many external resources. Key challenges include:
- Legacy Code: Integrating Content Security Policy into older websites may require significant refactoring, particularly to address inline scripts and external resources.
- Compatibility: Ensuring that third-party resources (like ad networks, analytics scripts, or CDNs) comply with the policy can be difficult.
- Testing and Maintenance: Continuously testing the policy and adjusting it as your site evolves can require ongoing monitoring and fine-tuning.
Despite these challenges, the security benefits of implementing a Content Security Policy far outweigh the initial setup effort, making it a valuable tool for modern web security.
Content Security Policy and SEO: Improving Site Security and Performance
Content Security Policy (Content Security Policy) plays a significant role in enhancing both site security and performance, which indirectly benefits SEO.
- Improved Site Security: By reducing the risk of cross-site scripting (XSS) attacks and data injections, Content Security Policy makes websites safer, improving user trust and reducing security-related penalties.
- Faster Load Times: By restricting resource loading, Content Security Policy ensures that only trusted and optimized resources are used, improving page load speed and enhancing Core Web Vitals.
- Enhanced Crawlability: A secure site that loads faster has better user experience metrics, which search engines reward with improved rankings.
Learn More: How to Increase Website Speed
Conclusion
Content Security Policy is a crucial web security measure that helps protect websites from various attacks, including XSS and data injections. By implementing and fine-tuning Content Security Policy, developers can enhance site security, improve performance, and ensure proper data handling.
Although adoption can be challenging, the benefits, improved security, better user experience, and improved SEO performance make it essential for modern websites.