Charles Proxy is a web debugging tool that captures and analyzes HTTP and HTTPS traffic between devices and servers. It helps developers inspect, modify, and test network behavior in real time.
Overview
Usage of Charles Proxy
Used across web and mobile development, Charles Proxy is popular for API testing, SSL inspection, and simulating network conditions during QA.
Why look for alternatives to Charles Proxy?
- Manual proxy and certificate configuration
- Limited support across platforms and workflows
- No built-in support for real-time rule sharing
- Slower setup for modern debugging needs
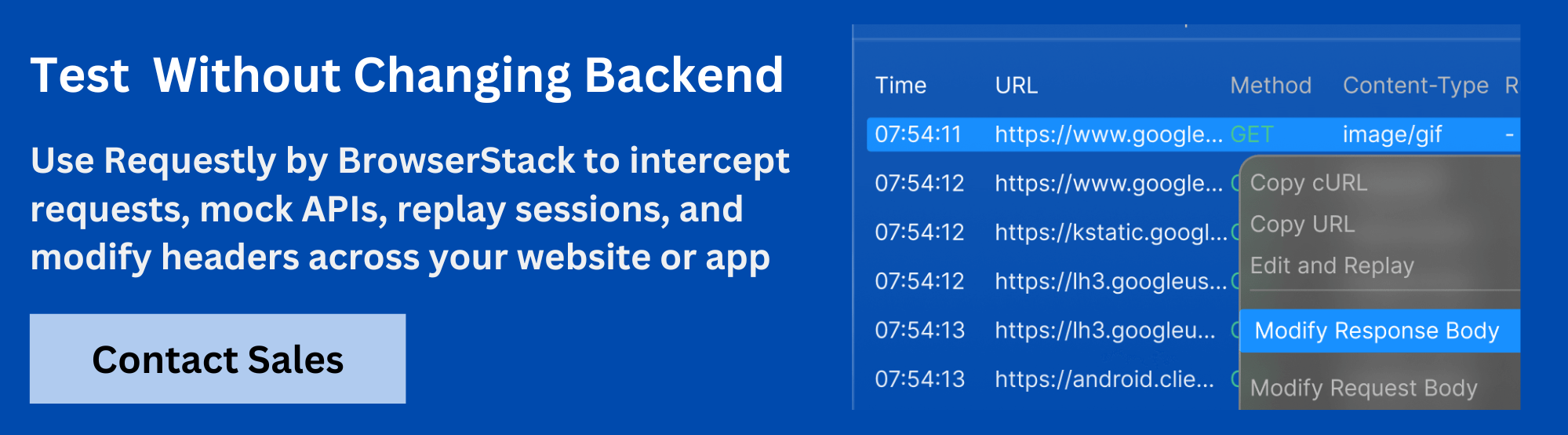
Requestly offers a simpler, faster approach to HTTP interception with real-time modification, API mocking, and seamless team collaboration.
This article covers what Charles Proxy is, how it works, and how to use it effectively across projects.
What is Charles Proxy?
Charles Proxy is an HTTP debugging proxy tool that allows developers to inspect network traffic between a device and the internet.
It captures HTTP and HTTPS requests and responses in real time, making it easier to analyze how web and mobile apps interact with APIs and servers.
The tool is commonly used for debugging issues related to cookies, headers, caching, redirects, and request payloads. Charles Proxy operates as a middle layer that logs, modifies, and simulates network behavior across browsers, backend services, and native apps.
Key Features of Charles Proxy
Charles Proxy offers a set of features focused on web traffic analysis and debugging.
These tools are useful for frontend engineers, QA teams, and API developers who need to troubleshoot client-server communication.
Notable features include:
- Traffic capture and inspection: Records all HTTP and HTTPS traffic with request and response details
- SSL proxying: Allows inspection of encrypted traffic by installing a root certificate
- Bandwidth throttling: Simulates slower network speeds to test performance under real-world conditions
- Breakpoints: Pauses requests and responses to modify them before they reach the server or client
- Request rewriting: Enables automated changes to headers, methods, or URLs for testing and debugging
- Session exporting: Saves and shares captured sessions for offline analysis or collaboration
- WebSocket support: Captures WebSocket messages alongside standard HTTP traffic
These capabilities make Charles Proxy a flexible tool for web debugging, though its configuration and manual setup may require additional steps, especially on mobile.
Supported Platforms and System Requirements
Charles Proxy is available for major desktop operating systems. It runs as a native application and requires administrative privileges to install root certificates and configure proxy settings.
Supported platforms:
- macOS: Compatible with the latest macOS versions, including Apple Silicon support
- Windows: Runs on Windows 10 and later, both 32-bit and 64-bit versions
- Linux: Not officially supported, but can run via Wine with limited functionality
System requirements:
- Java Runtime Environment (JRE) is required to run the application
- Admin access is needed to enable SSL proxying and configure system proxy settings
- Mobile device support (iOS and Android) requires proxy redirection through the desktop application
Use Cases for Charles Proxy
Charles Proxy is used by developers, QA testers, and network analysts to inspect and debug client-server communication. Its primary use cases include:
- Debugging HTTP and HTTPS traffic between web or mobile apps and backend APIs
- Testing API calls for request structure, authentication headers, and response payloads
- Analyzing redirect loops, caching, or cookies that affect app behavior
- Inspecting third-party integrations like payment gateways, analytics, or tracking scripts
- Troubleshooting SSL issues by decrypting secure traffic
- Simulating network latency or bandwidth limits for performance testing
How Charles Proxy Works
Charles Proxy captures all HTTP and HTTPS traffic by acting as a local proxy server. It enables developers to inspect, debug, and manipulate web and mobile network activity.
Here’s how Charles Proxy functions:
- Runs a proxy server locally (default port: 8888)
- Routes device or browser traffic through this proxy
- Logs requests and responses in real time
- Displays headers, status codes, query params, and body content
- Requires SSL certificate installation to inspect HTTPS traffic
- Supports web, emulator, and physical device traffic
Installation and Setup Guide
Getting started with Charles Proxy takes only a few minutes. Installation is available for macOS and Windows.
To install and launch:
- Download the installer from the official Charles Proxy website
- Run the setup file for your operating system
- Launch the application and allow proxy configuration
- Install the Charles SSL certificate if HTTPS traffic needs to be inspected
- Begin capturing traffic automatically through the system proxy
Configuring Charles Proxy For Web And Mobile Debugging
Charles supports traffic capture for both web and mobile. The setup differs slightly for each, particularly around SSL configuration and proxy routing.
For web debugging:
- Launch Charles and allow it to auto-configure system proxy
- Set the browser or OS proxy to 127.0.0.1:8888
- Enable SSL proxying in Proxy > SSL Proxying Settings
- Install and trust the Charles certificate in your system or browser
For mobile debugging (iOS and Android):
- Connect the device to the same Wi-Fi network
- Set proxy manually to your computer’s IP and port 8888
- Install and trust the certificate on the device
- Enable domain-specific SSL proxying inside Charles
SSL Proxying And Certificate Configuration
To decrypt HTTPS traffic, Charles requires SSL proxying to be enabled and trusted certificates installed. Without this, secure traffic cannot be inspected.
Steps to configure SSL proxying:
- Go to Help > SSL Proxying > Install Charles Root Certificate
- Install the certificate in your browser, system, or mobile device
- Trust the certificate in OS security settings or device preferences
- Enable SSL Proxying via Proxy > SSL Proxying Setting
- Add domain rules or * to proxy all secure traffic
Inspecting And Modifying HTTP/HTTPS Traffic
Once traffic is captured, Charles allows full inspection and editing of requests and responses. This is helpful for validating APIs or simulating different client inputs.
To inspect traffic:
- Select a session in the left panel
- Use the “Request” and “Response” tabs to view headers, payloads, and status codes
- Expand each node to view cookies, parameters, and JSON/XML content
To modify and replay:
- Right-click on a request and choose “Edit Request”
- Change the payload, URL, headers, or method
- Use “Repeat Advanced” to send the modified request
Bandwidth Throttling And Network Simulation
Charles can throttle bandwidth and add latency to simulate real-world network conditions. This helps test how apps behave on slower connections.
To simulate network environments:
- Go to Proxy > Throttle Settings and enable throttling
- Choose presets like 3G, DSL, or customize speeds manually
- Set bandwidth (e.g., 512 kbps) and latency (e.g., 300 ms)
- Apply these rules globally or per domain/session
Learn More: How to Intercept the Network on iOS Simulator?
Using Breakpoints And Rewriting In Charles Proxy
Charles enables interactive debugging with breakpoints and rule-based automation through rewriting. Both are powerful for intercepting and altering live traffic.
To use breakpoints:
- Right-click a request and enable “Breakpoints”
- Intercept the request or response before it completes
- Edit headers, method, or body, then forward or drop it
To rewrite traffic automatically:
- Go to Tools > Rewrite and create a new rule set
- Add match and replace rules for headers, paths, or parameters
- Example: Replace X-Env: prod with X-Env: staging for environment simulation
Web Scraping with Charles Proxy
Charles Proxy helps capture and inspect data from web requests, making it useful for manual web scraping and traffic analysis.
Common scraping tasks include:
- Identifying API endpoints behind dynamic websites
- Viewing request headers, query parameters, and response payloads
- Exporting session data for further parsing using tools like Postman or Python scripts
While Charles does not automate scraping, it simplifies endpoint discovery and response inspection for structured data extraction.
API Development and Testing with Charles Proxy
Charles Proxy allows developers to inspect API requests and validate backend integration in real time.
Useful API workflows:
- Debugging failed API calls and checking authentication headers
- Testing different payloads by modifying and replaying requests
- Comparing staging and production responses using request rewriting
This helps ensure API consistency, spot edge case failures, and reduce dependency on frontend UI during backend development.
Also Read: Front End Testing: A Beginner’s Guide
Security Testing Using Charles Proxy
Charles Proxy can be used for basic security testing by revealing potential vulnerabilities in network communication.
Key testing actions include:
- Intercepting requests to test for exposed tokens, cookies, or credentials
- Modifying parameters to test for improper input validation
- Simulating man-in-the-middle conditions via SSL interception
While not a full security audit tool, it helps uncover common misconfigurations or data exposure issues during development and QA.
Troubleshooting Common Issues
Charles Proxy setup may fail due to incorrect configuration or system-level restrictions.
Typical issues and solutions:
- Blank or no traffic: Ensure proxy settings point to 127.0.0.1:8888 and app traffic is routed through Charles
- HTTPS traffic not visible: Install and trust the Charles SSL certificate
- Mobile device not connecting: Confirm both devices are on the same Wi-Fi and manual proxy is set correctly
- App not responding: Check if breakpoints or rewriting rules are unintentionally active
Integration with Other Tools
Charles Proxy complements a variety of dev and test tools by acting as a traffic layer between applications and servers.
Common integrations include:
- Postman: Use captured requests to replicate API tests
- JMeter or LoadRunner: Export session data for load testing scripts
- Browser DevTools: Cross-verify requests and isolate frontend issues
- Requestly: Combine with Charles for advanced rule-based request interception in the browser
These integrations help extend debugging and automation workflows across your full toolchain.
Why Look for an Alternative to Charles Proxy?
Charles Proxy has been a go-to tool for inspecting and modifying network traffic, but it often involves extra setup and maintenance. Developers and testers frequently encounter friction when configuring system proxies, installing certificates, or debugging across different environments.
Common limitations include:
- Manual setup for SSL proxying and mobile debugging
- Inconsistent support across platforms and devices
- Lack of built-in features for mocking, scripting, or collaboration
- Steep learning curve for less technical users
These challenges make it harder to integrate Charles into fast-moving development cycles or team-based QA workflows.
A Modern Alternative to Charles Proxy: Requestly
Requestly is a modern HTTP interceptor built for today’s debugging and testing needs. It allows developers and QA teams to inspect, modify, and mock HTTP traffic in real time, without complex setup.
Available as a browser extension and desktop app, Requestly works across browsers, mobile apps, emulators, and backend services. It simplifies everyday tasks like testing API changes, rewriting headers, simulating responses, or debugging third-party integrations.
What makes Requestly a strong alternative:
- Instantly modify headers, URLs, methods, or payloads
- Mock APIs and inject scripts without touching backend code
- Share custom rules and sessions across teams
- Supports cross-platform traffic interception out of the box
- No proxy or certificate configuration required for most use cases
Requestly combines flexibility, speed, and collaboration in a single tool, making it a practical replacement for teams who find Charles Proxy too rigid or manual for modern workflows.
Conclusion
Charles Proxy remains a reliable tool for inspecting and debugging network traffic, especially for complex web and mobile applications.
But for modern teams who need a faster, easier, and more collaborative workflow, tools like Requestly offer a more agile alternative.
Whether you’re debugging an API, simulating network failures, or rewriting requests for testing, choosing the right tool depends on your environment, team needs, and how much time you’re willing to spend on setup versus execution.