Monitoring and analyzing network traffic on a Mac helps uncover issues like performance bottlenecks, unauthorized data transfers, and unexpected application behavior. By capturing and examining packets, you can understand how apps interact with the network, identify potential security risks, and fine-tune configurations.
This document covers key areas to help you inspect network traffic on your Mac, including setup steps, built-in tools, third-party solutions, and best practices.
What is Network Traffic Inspection on Mac?
Network traffic inspection on Mac means capturing and analyzing the data packets sent and received by applications and services. This involves monitoring communication flows, identifying the sources and destinations of traffic, and understanding the details of protocols and payloads.
This process helps you verify application behavior, detect security threats, and find performance issues. It involves using built-in tools or third-party software to gain visibility into how your Mac interacts with networks.
Why Inspect Network Traffic on Mac?
Inspecting network traffic on a Mac provides several benefits beyond just troubleshooting:
- Diagnose Application Issues: Identify why apps might fail to connect or respond slowly.
- Understand Data Flows: Track where data originates and terminates to pinpoint bottlenecks.
- Improve Security: Spot suspicious patterns or unauthorized connections.
- Verify Compliance: Ensure your apps follow security and privacy standards.
Basics of Network Traffic on Mac
It is essential to understand the basics of network traffic on macOS to interpret what you see during inspections.
Here’s what you should know:
1. Data Packets: Network traffic consists of packets and small data units transmitted between your Mac and other devices. Packets contain headers with source and destination details and payloads with the actual data.
2. Protocols: These define the rules of communication. Common ones include:
- TCP (Transmission Control Protocol): Reliable, connection-based delivery.
- UDP (User Datagram Protocol): Faster but connectionless delivery.
- HTTP/HTTPS: Used for web traffic.
- DNS: Resolves domain names to IP addresses.
3. IP Addresses and Ports: Each device on a network has an IP address. Applications listen on specific ports to send and receive data.
4. Network Interfaces: macOS connects to networks using interfaces like Wi-Fi or Ethernet. Each interface has its own settings and traffic flows.
5. Firewalls and Filters: macOS includes built-in firewalls and filters that can affect traffic visibility during inspections.
How to Prepare Your Mac for Network Traffic Inspection
Before inspecting network traffic, you must ensure your Mac can capture and analyze data accurately. A properly configured environment ensures that tools work effectively and you gather reliable information.
Here’s how to prepare:
1. Update macOS: Use the latest macOS version or a supported version that receives security updates and patches. Outdated systems may lack the necessary components for traffic capture.
2. Check User Permissions: Many inspection tools need administrator-level access to capture packets at the network interface level. Verify you have admin rights and can use sudo commands in the Terminal if required.
3. Identify Active Network Interfaces: Know which interface your Mac uses for network connectivity. For example:
- Wi-Fi: en0 for wireless traffic
- Ethernet: en1 or other names for wired traffic
- Virtual Interfaces: For virtual machines or VPN tunnels
Use the ifconfig or networksetup -listallhardwareports commands in Terminal to list interfaces and their status.
4. Install Required Command-Line Tools: Some built-in commands like tcpdump rely on macOS system components (like Xcode Command Line Tools). Install them by running xcode-select –install if they’re not already present.
5. Check Network Connectivity: Test your network connection and ensure it’s stable before capturing traffic. Dropped packets or weak Wi-Fi signals can skew your analysis.
6. Secure Your Environment: Only inspect traffic on networks you own or have permission to monitor. Unauthorized inspection can violate privacy or legal guidelines.
How to Use Built-in macOS Tools to Inspect Network Traffic
macOS provides built-in tools that provide basic traffic monitoring capabilities. They’re useful for quick checks or troubleshooting, especially if you don’t want to install third-party tools.
Here’s how to use these built-in tools:
1. Inspect Network Traffic with Activity Monitor
Activity Monitor is a graphical tool that shows live network usage and traffic details for applications.
- Open Activity Monitor: Find it in Applications > Utilities or search with Spotlight.
- Navigate to the Network Tab: It lists processes, data sent and received, and the number of packets.
- Sort by Data Sent or Received: Click the column headers to find apps using the most bandwidth quickly.
Activity Monitor doesn’t show packet-level details, but it helps pinpoint high-traffic applications.
2. Using Terminal Commands for Network Traffic
The Terminal provides more advanced inspection through commands like nettop and tcpdump.
- nettop: Displays live network connections, sorted by process.
- Open Terminal and run sudo nettop
- View active connections, bytes sent/received, and connection states.
- Use arrow keys to navigate and q to quit.
- tcpdump: Captures packets for detailed inspection.
- Run sudo tcpdump -i en0 (replace en0 with your interface) to start a capture.
- Use flags like -nn to avoid DNS resolution or -c 100 to capture 100 packets.
- Stop the capture with Ctrl+C.
How to Inspect Network Traffic on Mac Using Requestly
Third-party tools like Requestly provide more advanced capabilities for network traffic inspection and manipulation. Requestly is a user-friendly app for capturing, modifying, and debugging HTTP and HTTPS traffic.
Here’s how to get started with Requestly:
1. Installing and Setting Up Requestly on Mac
Before inspecting or modifying network traffic with Requestly, you need to download and install it on your Mac.
- Download Requestly: Visit the official website and download the macOS application.
- Install and Launch: Move the app to your Applications folder and open it.
- Grant Permissions: Grant the requested permissions, such as proxy creation and HTTPS certificate installation, to allow Requestly to capture and modify traffic.
Optional: You can also download Requestly’s Browser Extension to inspect and modify network traffic.
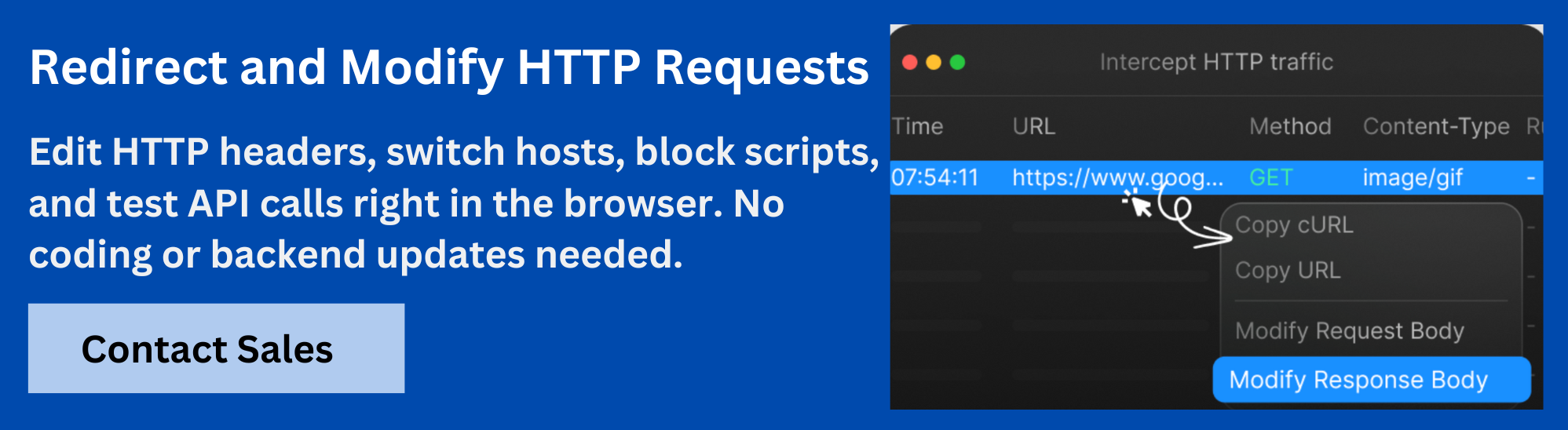
2. Using Requestly to Intercept and Modify Network Requests
Once installed, you can use Requestly to capture live network traffic and apply rules to modify requests or responses.
- Start Capturing Traffic: Enable capturing in the app to route traffic through Requestly’s proxy engine.
- Create and Manage Rules: Set up rules to:
- Modify Headers: Adjust request or response headers as needed.
- Redirect URLs: Change destination URLs for specific requests.
- Block Requests: Prevent certain requests from being sent or received.
- View Details: Inspect request and response data, including status codes, headers, and bodies, in real time.
Advanced Techniques to Inspect Network Traffic on Mac
Advanced techniques and deeper analysis are essential for more comprehensive insights. These approaches let you customize captures, analyze virtualized environments, and identify performance bottlenecks.
Here’s how to elevate your network traffic inspection:
1. Create Custom Filters and Capture Rules
Custom filters and capture rules focus on particular types of network traffic. They help you avoid capturing irrelevant data and ensure you see only the traffic that matters for your investigation.
- Custom Filters: Use command-line tools like tcpdump to build precise filters. For example, tcpdump -i en0 port 443 captures only HTTPS traffic.
- Protocol-Specific Analysis: Narrow down your capture to specific protocols. Use flags and filters to focus on HTTP, DNS, SSH, or other traffic types.
These filters reduce clutter and help you focus on the most relevant data for your investigation.
2. Inspect Traffic from Virtual Machines
If you run virtual machines on your Mac, you must inspect traffic at the virtual interfaces they create. This ensures you don’t miss traffic that flows only within the virtual environment.
- Identify VM Interfaces: Use ifconfig to list all active interfaces and locate those used by your virtual machines, like vnic0.
- Capture Traffic: Once identified, run your preferred network capture tools on these interfaces. For example, use tcpdump on the virtual interface to see packets sent or received by the VM.
This ensures you capture everything relevant, even if it doesn’t travel through your physical network adapter.
3. Use Network Inspection for Performance Tuning
Network inspection also plays a key role in troubleshooting performance problems and ensuring that applications work smoothly.
- Measure Latency: Examine packet timestamps to pinpoint where delays occur in the network path.
- Spot Retransmissions: Look for repeated TCP packets, often indicating congestion or unstable links.
- Identify Bottlenecks: Analyze traffic to determine whether issues are caused by the Mac itself, the local network, or external services.
Conclusion
Inspecting network traffic on your Mac is essential for troubleshooting issues, ensuring security, and improving performance. It involves capturing and analyzing data flows using built-in tools and command-line utilities that reveal how your applications and system communicate over the network.
Requestly adds powerful capabilities to easily intercept, modify, and debug requests. Requestly lets you create custom rules to block, redirect, or change headers and request bodies. It also provides real-time traffic views with detailed request and response data insights, making it easier to test changes and understand traffic behavior without needing deep command-line expertise.