Web browsers sometimes misinterpret the type of content served by a web application, which can allow malicious scripts to run unexpectedly. The X-Content-Type-Options header prevents this by enforcing strict content-type handling.
Overview
What are X-Content-Type-Options?
X-Content-Type-Options is an HTTP header that instructs browsers to strictly follow the declared content type of resources, preventing them from interpreting files as something else.
What X-Content-Type-Options Does
- Prevent MIME Type Sniffing: Stops browsers from trying to guess the content type header and executing potentially harmful scripts.
- Enhance Browser Security: Ensures content is interpreted exactly as intended, reducing attack surfaces.
- Support Consistent Behavior: Provides predictable rendering across different browsers.
Why X-Content-Type-Options Is Used
- Mitigate XSS Attacks: Blocks content misinterpretation that could lead to cross-site scripting vulnerabilities.
- Enforce Strict Content Handling: Ensures scripts, styles, and other resources are processed safely.
- Maintain Security Standards: Helps comply with web security best practices and guidelines.
How to Use X-Content-Type-Options
- Set Header to nosniff: Add X-Content-Type-Options: nosniff in server response headers.
- Apply Across All Resources: Ensure all static and dynamic resources include the header.
- Combine With Other Security Headers: Use alongside Content-Security-Policy and X-Frame-Options for layered protection.
This article explains X-Content-Type-Options, its importance, usage, best practices, misconfigurations, and testing strategies.
What Are X-Content-Type-Options?
X-Content-Type-Options is an HTTP response header that instructs web browsers to strictly respect the declared content type of a resource. Normally, browsers attempt to “sniff” or guess the type of content they receive, which can sometimes lead to executing scripts or files incorrectly.
By using X-Content-Type-Options, servers tell browsers to trust only the content type specified in the Content-Type header, ensuring that scripts, images, stylesheets, and other resources are interpreted exactly as intended.
This is particularly important for preventing security vulnerabilities such as cross-site scripting (XSS), where malicious scripts could run if a browser misinterprets a file type. It is commonly implemented with the value nosniff, which enforces strict type adherence across all resources served by the application.
Why Is X-Content-Type-Options Important?
X-Content-Type-Options is critical for web security because it prevents browsers from misinterpreting content, which could otherwise allow malicious scripts or files to execute.
Here are the main reasons X-Content-Type-Options is important:
- Mitigates Cross-Site Scripting (XSS) Risks: By preventing browsers from guessing content types, X-Content-Type-Options stops scripts served with incorrect content types from executing, reducing opportunities for XSS attacks.
- Ensures Predictable Content Handling: X-Content-Type-Options guarantees that scripts, stylesheets, images, and other resources are interpreted exactly as declared, preventing unexpected browser behavior.
- Reduces Attack Surface: Misinterpreted content can be exploited to deliver malicious payloads. X-Content-Type-Options minimizes such risks by strictly enforcing declared content types.
- Supports Compliance with Security Standards: Many security frameworks and best practices recommend X-Content-Type-Options as a baseline measure to ensure content integrity and safe handling by browsers.
- Enhances User Trust: By preventing unintended script execution and content misinterpretation, X-Content-Type-Options helps maintain secure user interactions with a web application.
How Does X-Content-Type-Options Work?
Browsers often try to guess the type of content they receive, which can lead to security issues if they interpret files incorrectly. X-Content-Type-Options enforces strict adherence to the declared content type to prevent such risks.
Here are the main ways X-Content-Type-Options works:
- Enforces Declared Content Type: When a server includes X-Content-Type-Options: nosniff, the browser will only process a resource according to the Content-Type header. For example, a file labeled as text/javascript will only execute as a script, and any mismatch will cause the browser to block execution.
- Blocks MIME Type Sniffing: Browsers often try to detect file types heuristically, which can allow a mislabelled file to execute malicious code. X-Content-Type-Options disables this behavior, ensuring that sniffing does not override the declared type.
- Applies to All Resource Types: The header affects scripts, CSS, images, fonts, and other content. This means even incorrectly served files cannot be misinterpreted, reducing the risk of XSS and content injection attacks.
- Prevents Exploitation of Browser Quirks: Some browsers historically allowed dangerous fallback behaviors if content types were ambiguous. With X-Content-Type-Options, these quirks are disabled, creating a predictable and secure execution environment.
- Supports Layered Security: By strictly enforcing content types, X-Content-Type-Options complements other security headers such as Content-Security-Policy and X-Frame-Options, creating multiple layers of protection against code injection and malicious content.
Common X-Content-Type-Options Misconfigurations and How to Avoid Them
Even when X-Content-Type-Options is implemented, misconfigurations can reduce its effectiveness or break functionality. Here are frequent misconfigurations and ways to avoid them:
- Missing Header on Certain Resources: Some scripts, images, or stylesheets may be served without the header. Always verify that X-Content-Type-Options: nosniff is applied across all critical resources.
- Incorrect Header Value: Using values other than nosniff will not enforce strict content-type handling. Ensure the value is exactly nosniff.
- Overriding by Middleware or Proxies: Some server-side frameworks or proxies may override headers. Confirm that the header is correctly set at the server or reverse proxy level and not removed later in the request pipeline.
- Inconsistent Application Across Environments: Development, staging, and production environments may have different configurations. Standardize header implementation across all environments to prevent gaps.
- Breaking Legacy Scripts: Older scripts or third-party resources may rely on MIME type sniffing. Test all functionality after enabling X-Content-Type-Options and update or replace incompatible resources.
Best Practices for Implementing X-Content-Type-Options
Proper implementation of X-Content-Type-Options ensures that browsers enforce strict content-type handling without causing unintended issues.
Here are best practices for X-Content-Type-Options:
- Always Set the Header to nosniff: Ensure X-Content-Type-Options: nosniff is included in all HTTP responses. This prevents browsers from attempting to guess content types.
- Apply Across All Resources: Include the header for scripts, stylesheets, images, fonts, and dynamic content to maintain consistent security enforcement.
- Use Server-Level Configuration: Configure the header at the web server or reverse proxy level (e.g., Apache, Nginx) to guarantee coverage across the entire application.
- Combine With Other Security Headers: Implement alongside Content-Security-Policy, X-Frame-Options, and HSTS to provide multiple layers of protection.
- Avoid Overriding on Specific Resources: Do not exclude certain scripts or files unless absolutely necessary, as inconsistent application of the header can introduce vulnerabilities.
- Test After Deployment: After setting X-Content-Type-Options: nosniff, verify it is present on all critical resources. Use tools like Requestly to test header behavior in real time and ensure browsers strictly follow declared content types.
Advanced X-Content-Type-Options Use Cases
X-Content-Type-Options can be leveraged in complex scenarios to strengthen security and ensure strict content handling across diverse applications.
- Securing Third-Party Content: Enforce X-Content-Type-Options on scripts, styles, or media loaded from external domains to prevent execution if a third-party server serves an incorrect content type.
- Dynamic Resource Protection: For resources generated dynamically, such as user-uploaded files or server-side scripts, X-Content-Type-Options ensures that content is interpreted strictly as intended, reducing risks of executing injected code.
- Preventing Legacy Browser Exploits: Older browsers may try aggressive MIME sniffing. X-Content-Type-Options blocks these behaviors, mitigating exploits that target content-type vulnerabilities in outdated clients.
Read More: Cross Browser Compatibility Issues to Avoid
- Layered Security with Content Security Policy: Combining X-Content-Type-Options with CSP ensures that only correctly typed scripts and styles execute, providing multiple barriers against content injection attacks.
- Protecting Mixed-Content Scenarios: In applications serving both static and dynamic resources, X-Content-Type-Options prevents misinterpretation of mixed content types, maintaining predictable behavior across resources.
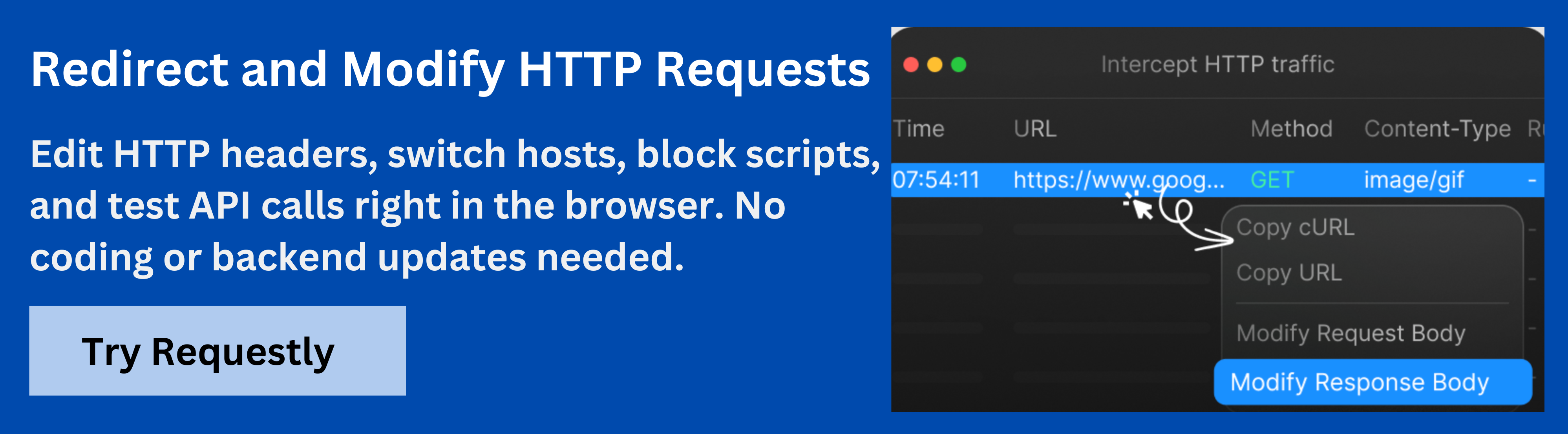
How Requestly Helps Test X-Content-Type-Options
Requestly is a browser extension and web debugging tool that allows developers to modify HTTP requests and responses in real time. It enables testing, debugging, and validating web applications without changing server-side code.
Requestly helps developers test X-Content-Type-Options by letting them simulate headers on any resource and observe how browsers respond. This allows quick verification that scripts, stylesheets, images, and other content are handled correctly under strict content-type enforcement.
Here are some key features of Requestly for testing X-Content-Type-Options:
- Modify Headers in Real Time: Add or override X-Content-Type-Options on requests to test browser behavior.
- Simulate Browser Behavior: Observe how different browsers interpret content when nosniff is applied or removed.
- Validate Resource Security: Confirm that scripts, images, and stylesheets are blocked or executed correctly based on declared content types.
- Test Dynamic and Third-Party Content: Apply header rules to external or dynamically generated resources to ensure consistent enforcement.
- Quickly Iterate Changes: Adjust header rules instantly without redeploying the application to verify potential misconfigurations or improvements.
Conclusion
X-Content-Type-Options is a critical HTTP header that improves web security by enforcing strict content-type handling. It prevents browsers from misinterpreting resources, reducing risks like cross-site scripting and ensuring consistent behavior across scripts, stylesheets, images, and other content.
Requestly make it easier to test and validate X-Content-Type-Options in real time. Developers can simulate header behavior, verify browser responses, and quickly identify misconfigurations or vulnerabilities, ensuring that strict content-type enforcement works as intended across all resources.