API keys are small pieces of information that allow applications to interact with APIs securely. They act as unique identifiers that help APIs recognize the calling application and control its access.
Overview
What is an API Key?
An API key is a unique code assigned to an application or developer. It is sent with API requests to verify identity and determine which resources or actions the caller can access.
Why Are API Keys Used?
- Authentication: Confirms the identity of the application or developer making the request.
- Access Control: Specifies which endpoints or data the caller is permitted to use.
- Usage Monitoring: Tracks how the API is being used and detects unusual activity.
- Billing and Quotas: Associates usage with accounts to manage charges and enforce limits.
How API Keys Work
- Request Identification: The API key identifies the application or developer sending the request.
- Validation: The server checks whether the key is valid and active.
- Permission Enforcement: Access is granted or denied based on the key’s assigned permissions.
- Monitoring: All activity with the key is logged for auditing, tracking, and enforcing usage limits.
Key Aspects of API Keys
- Security: API keys are sensitive credentials. Exposing them publicly can allow unauthorized access or unexpected charges. They should be stored securely and rotated regularly.
- Uniqueness: Each key is unique and serves as a digital identifier for the specific application or developer.
- Access Rights: Keys can be linked to specific permissions, allowing access only to the resources or functions the key holder is authorized to use.
This article covers the meaning, purpose, functioning, and best practices of API keys, along with how to manage them securely.
What Is an API Key?
An API key is a code used to identify and authenticate an application or developer when making requests to an API. It acts as a gatekeeper, telling the API who is making the request and whether they are allowed to access the requested resources.
API keys are usually long alphanumeric strings. They are unique to each application or developer and are issued by the API provider. While simple in concept, they form the first layer of security for API access and help track usage patterns for monitoring and billing purposes.
Below are the core points that define what an API key is:
- Identifier: Serves as a digital ID that distinguishes one application or developer from another.
- Credential: Functions as a secret token that must be kept secure, similar to a password for applications.
- Access Enabler: Grants permission to use specific endpoints or services provided by the API.
- Tracking Tool: Helps API providers monitor usage, enforce quotas, and link activity to specific accounts.
Also Read: Top 15 API Testing Tools
Why Are API Keys Essential?
API keys provide control, security, and visibility when applications interact with APIs. Proper use of API keys ensures that only authorized requests are processed, usage is monitored, and resources are protected.
Here are the key reasons API keys are essential:
- Authentication: API keys confirm the identity of the caller at the request level. Unlike user credentials, they identify the application or service rather than individual users. This is crucial for server-to-server communication or automated systems.
- Access Control: Keys can be scoped to specific endpoints, actions, or data sets. For example, one key may allow reading data but not writing, preventing accidental or malicious modifications.
- Usage Monitoring and Analytics: API providers can track each key’s activity in detail. This helps detect abnormal patterns such as sudden spikes, repeated failures, or unauthorized attempts, enabling proactive security and operational management.
- Quota and Billing Enforcement: Keys are tied to accounts and can enforce limits per user or per application. This prevents overuse, ensures fair allocation of resources, and supports accurate billing for paid APIs.
- Security Layer in Automation: While not a replacement for advanced authentication like OAuth, API keys provide a lightweight first layer of security. They protect internal or third-party APIs from anonymous access and serve as a foundation for auditing and monitoring.
Read More: What Is API Automation Testing?
- Environment Segmentation: Different keys can be issued for development, testing, staging, and production environments. This ensures that testing activity does not interfere with live data or services.
- Integration Control: API keys make it easier to manage third-party integrations. Providers can revoke or rotate keys without impacting other applications, limiting exposure in case of a compromised key.
Key Aspects of API Keys
API keys have specific properties that determine how they are used, secured, and managed. These characteristics influence both how APIs operate and how developers and testers handle access and permissions.
Below are the main aspects of API keys:
- Security: API keys are sensitive credentials. Public exposure can lead to unauthorized access, data breaches, or unexpected costs. They should be stored in environment variables, secret managers, or encrypted storage. Regular rotation and immediate revocation of compromised keys reduce risk.
- Uniqueness: Each API key is assigned to a specific application, developer, or environment. This allows accurate tracking of requests, usage, and permissions.
- Access Rights: Keys can be restricted to particular endpoints, actions, or resources. This limits the scope of access and reduces potential impact if a key is exposed.
- Traceability: Each key is linked to an application or developer, enabling detailed logging, monitoring, and accountability for API activity.
- Environment Management: Separate keys can be issued for development, testing, staging, and production environments. This prevents test activity from affecting live systems and allows safe experimentation.
- Revocation and Rotation: Keys can be revoked instantly if compromised or rotated periodically to maintain security without disrupting other integrations.
- Integration with Monitoring and Alerts: API key activity can trigger alerts for unusual usage, failed requests, or quota violations, supporting operational reliability and security oversight.
How Do API Keys Work?
API keys let an API know which application or developer is making a request. They also control what the caller can do. Here’s how they work step by step:
- Included in Requests: Each request to the API carries the key, usually in the header, query string, or body. This tells the API who is calling.
- Validation: The API checks if the key is valid and active. Invalid or revoked keys are rejected immediately.
- Permission Check: The API looks at what the key is allowed to do. It only lets the caller access permitted endpoints or data.
- Rate Limits: The API tracks how much the key is used. If usage exceeds allowed limits, requests may be blocked or delayed.
- Logging: Every request with a key is recorded. This helps monitor activity, find errors, and maintain accountability.
- Environment Separation: Keys can be set for development, testing, or production environments. This prevents test requests from affecting live data.
- Revocation and Rotation: Keys can be revoked if compromised or rotated periodically for security.
- Works with Other Security Measures: API keys can be combined with TLS, IP restrictions, or OAuth tokens for added protection.
Common Use Cases of API Keys
API keys provide controlled access to APIs while enabling monitoring, security, and accountability. They are widely used across applications to manage interactions safely and efficiently. Below are common scenarios:
- Third-Party Integrations: External applications use API keys to access services without sharing user credentials. Each key identifies the app individually, allowing providers to track usage, revoke access if needed, and prevent abuse.
- Server-to-Server Communication: Internal services or microservices include API keys in requests to authenticate themselves. This ensures that only authorized services can access specific endpoints and helps trace activity across systems.
- Monitoring and Analytics: Providers track API usage per key. Unusual patterns, such as spikes in requests or repeated failures, are detected early, helping prevent outages or security incidents.
- Mobile and Web Applications: Client applications include API keys in requests to access data or services securely. This protects end-user credentials and allows the API to enforce limits and track app-specific activity.
- Environment Management: Different keys can be issued for development, testing, staging, and production. This prevents test activity from affecting live systems and allows independent monitoring for each environment.
- Billing and Quotas: API keys tie usage to specific accounts, enabling accurate billing and consumption control. Providers can enforce limits, prevent overuse, and track application-level usage.
- Temporary or Scoped Access: Keys can be restricted to certain actions, datasets, or time periods. This allows safe, temporary access for partners or contractors without exposing full functionality.
Also Read: A Comprehensive Guide to Different API Types
Security Risks of API Keys and How to Mitigate Them
API keys provide controlled access to APIs, but mishandling them can introduce serious security vulnerabilities. Understanding common risks and addressing them proactively is critical for developers and testers.
1. Exposure of API Keys
API keys can be accidentally exposed if they are stored in client-side code, public repositories, or shared logs. Once exposed, anyone can use the key to access the API, potentially causing data breaches or unauthorized actions.
To prevent this, keys should always be stored in secure locations, such as environment variables, encrypted secret managers, or server-side storage. Avoid embedding keys directly in code or exposing them in front-end applications.
2. Compromised or Stolen Keys
A key that falls into the wrong hands allows an attacker to access APIs with the same privileges as the legitimate application. This risk is particularly high for applications that use long-lived keys or share keys across multiple environments.
To reduce exposure, organizations should implement key rotation policies, issue short-lived keys for temporary access, and revoke any compromised keys immediately.
3. Excessive Permissions
Keys with broad access increase the potential impact if they are misused. For example, a key that can read and write data across multiple services can be exploited for malicious activity or accidental errors.
Assigning scoped permissions to each key ensures that applications can access only what they need. Limiting permissions reduces the potential consequences of a compromised key.
4. Unmonitored Usage
Without monitoring, unusual activity can go undetected. Sudden spikes in requests, repeated failures, or attempts to access restricted endpoints may indicate abuse or an attack.
Logging every request and analyzing patterns is critical. Alerts should be set up to notify teams of abnormal behavior, helping prevent service disruption or security incidents.
5. Hard-Coded Keys in Client Applications
Embedding keys in mobile or web applications exposes them to end users who can extract and misuse them. Even obfuscation techniques offer limited protection.
Moving key usage to server-side processes ensures that keys are never exposed in distributed applications. For cases where client-side usage is unavoidable, keys should be restricted, short-lived, or combined with IP whitelisting to limit risk.
6. Lack of Expiration or Rotation
Keys that never expire remain valid indefinitely, giving attackers a long window to exploit them if compromised. Implementing expiration dates and regular rotation reduces the time any leaked key can be used. Temporary keys can also be issued for specific projects or partners to further minimize long-term exposure.
Best Practices for Managing API Keys
Proper management of API keys ensures secure, controlled, and reliable access to APIs. Implementing structured practices reduces the risk of misuse and operational issues. Below are the key practices to follow:
- Store Keys Securely: Keep API keys in environment variables, encrypted secret managers, or server-side storage. Avoid hard-coding them in applications or exposing them in client-side code.
- Use Scoped Permissions: Limit each key to the specific endpoints or actions the application requires. Apply the principle of least privilege to reduce potential impact if a key is compromised.
- Rotate Keys Regularly: Periodically rotate keys to minimize the risk from leaks. Use short-lived keys for temporary access whenever possible.
- Revoke Compromised Keys: Immediately revoke keys that are exposed or misused, and issue replacements to maintain operational stability.
- Separate Keys by Environment: Use distinct keys for development, testing, staging, and production. This prevents accidental interference with live systems.
- Enable Logging and Monitoring: Track all activity per key and set alerts for unusual usage, failed requests, or quota violations. This helps identify security issues or operational problems quickly.
- Avoid Sharing Keys: Assign keys to specific applications or developers. Sharing keys increases risk and makes it difficult to trace activity.
- Combine with Other Security Measures: Use TLS encryption, IP whitelisting, or OAuth alongside API keys for added protection.
Alternatives to API Keys
API keys provide basic authentication and access control, but they have several limitations. They offer minimal security, lack fine-grained permission management, and cannot easily represent user-specific access. Modern applications often require alternatives that provide stronger authentication, better control, and improved monitoring.
The main alternatives include:
1. OAuth 2.0
OAuth 2.0 is an authorization framework designed to allow applications to access resources on behalf of a user without requiring their credentials. It issues access tokens that are scoped to specific permissions, making it possible to grant limited access to APIs. Refresh tokens extend access without repeatedly asking users to log in.
OAuth 2.0 is widely used in social logins, third-party integrations, and any scenario where user-level authorization is needed. By separating authentication from authorization, OAuth 2.0 reduces the risk of exposing sensitive credentials while allowing precise access control.
2. JSON Web Tokens (JWT)
JWTs are self-contained tokens that carry encoded claims about a user or application. They are signed, and optionally encrypted, allowing the API server to verify the token’s authenticity without querying a central database.
JWTs are ideal for stateless authentication, particularly in web and mobile applications, as the server does not need to store session information. JWTs can include metadata, such as roles or expiration, enabling fine-grained authorization decisions while reducing overhead.
3. OpenID Connect (OIDC)
OIDC extends OAuth 2.0 by providing user authentication alongside authorization. It allows applications to verify a user’s identity and obtain profile information, such as name, email, or roles.
OIDC is commonly used for single sign-on (SSO) across multiple services, federated identity management, and scenarios where both authentication and authorization are required. Unlike simple API keys, OIDC tokens carry signed identity information, reducing the risk of impersonation.
4. Mutual TLS (mTLS)
Mutual TLS requires both client and server to present certificates during the TLS handshake, establishing two-way trust. This approach ensures that only authorized clients can communicate with the API and that the server is legitimate.
mTLS is highly secure and often used in server-to-server communication, banking APIs, and enterprise environments where cryptographic verification is necessary. It addresses risks inherent to static tokens like API keys, such as interception or misuse.
5. HMAC (Hash-based Message Authentication Code)
HMAC combines a shared secret with the API request data to generate a unique signature. The server recalculates the signature to verify the request’s authenticity and integrity. HMAC ensures that requests are not tampered with and come from a trusted source.
HMAC is commonly used in financial, payment, or high-security APIs where every request must be verified cryptographically. Unlike API keys, HMAC provides data integrity in addition to authentication.
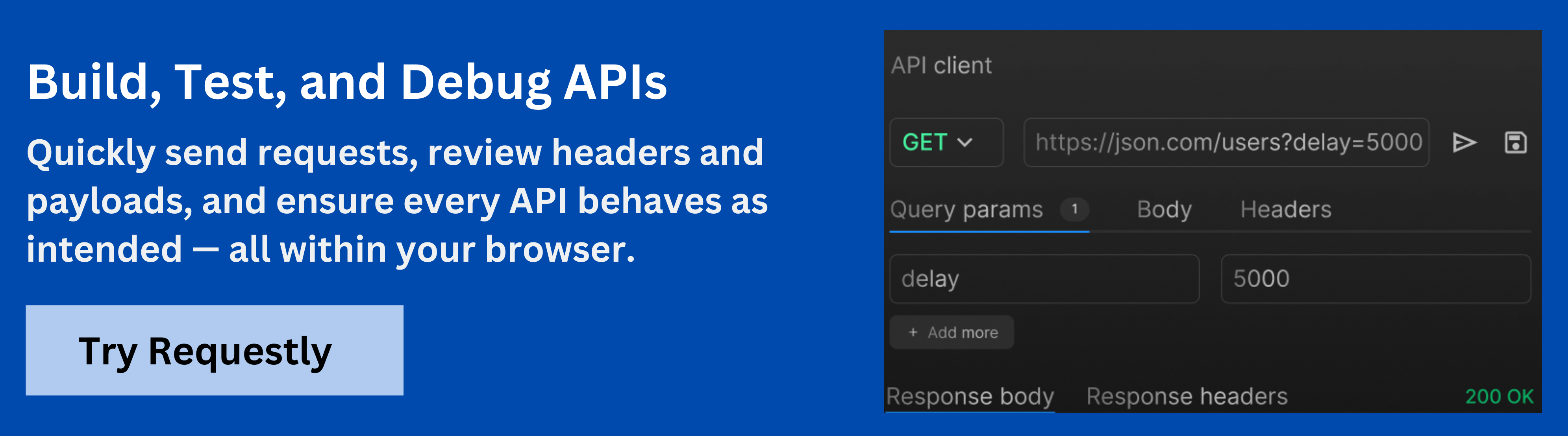
How Requestly Helps Test API Keys
Requestly by BrowserStack is an open-source, local-first API client and HTTP interceptor designed to streamline API testing and debugging. Unlike cloud-based tools, Requestly operates directly on your machine to ensure that sensitive information like API keys remains secure and private.
Here are several ways Requestly facilitates effective API key testing:
- Simulate API Responses Without Hitting the Server: Utilize Requestly’s Modify API Response rule to intercept requests and return predefined responses. This allows you to test how your application handles various scenarios, such as expired or invalid API keys, without making actual API calls.
- Inject Authorization Headers Dynamically: Configure the Authorization tab in Requestly to dynamically inject API keys or tokens into your requests. It supports various authorization methods, including API Key, Bearer Token, and Basic Auth, ensuring that your requests are properly authenticated during testing.
- Automate API Key Validity Tests: Write pre-request or post-response scripts using JavaScript to automate the validation of API keys. For instance, you can check if the API key is present, correctly formatted, and authorized to access specific endpoints.
- Create and Manage Multiple Environments: Set up different environments (e.g., development, staging, production) in Requestly, each with its own set of API keys. This allows you to test how your application interacts with various API versions and ensures that the correct API keys are used in the appropriate contexts.
- Monitor API Key Usage and Performance: Use Requestly’s built-in analytics to monitor the performance and usage of API keys. Track metrics such as response times, error rates, and request counts to assess the effectiveness of your API key management strategies and identify potential issues.
Conclusion
API keys control who can access APIs, but improper handling can lead to security breaches, unauthorized access, and operational issues. Testing API keys in different scenarios, such as expired or invalid keys, ensures applications respond correctly under all conditions.
Requestly provides a comprehensive environment for testing and managing API keys. It allows developers to simulate API responses without hitting the server, dynamically inject authorization headers, automate validation scripts, and manage multiple environments.