The first time a Playwright test stalled on a CAPTCHA, it looked like a one-off failure. The second time, it broke an entire CI run. By the third time, it became clear that CAPTCHA was not just another flaky UI element-it was a system designed to detect and stop automation.
I tried the usual fixes. Headless tweaks, user-agent overrides, stealth scripts. Some worked once, others passed locally and failed in CI. This led to the question: if CAPTCHA exists to block bots, why are test suites still expected to flow through it?
CAPTCHAs score behavior, browser signals, and interaction patterns long before a challenge appears. The more automation tries to outsmart them, the more brittle tests become.
Overview
Common CAPTCHA Bypass Approaches with Playwright
- Running browsers in headed mode to avoid basic headless checks
- Modifying user-agent strings, viewport size, timezone, and locale
- Injecting stealth scripts to hide automation-related browser APIs
- Reusing cookies or sessions captured from manual browser runs
- Using third-party CAPTCHA solvers or external APIs
- Stubbing CAPTCHA-related network requests
Playwright Limitations When Dealing with CAPTCHA
- No visibility into server-side risk models
- No control over IP reputation or ASN classification
- Limited influence over third-party security decisions
- Increased script complexity does not reduce detection confidence
Security Risks of CAPTCHA Bypass in Automation Pipelines
- Potential violations of terms of service
- Weakening of internal security controls
- Increased audit and compliance exposure
- Long-term maintenance overhead
This article breaks down what bypassing CAPTCHA with Playwright really means today, which techniques actually work, where they fail, and why safer alternatives often outperform direct bypass attempts.
What Is CAPTCHA and Why Websites Use It
CAPTCHA is a security mechanism designed to distinguish human users from automated programs. The term stands for Completely Automated Public Turing test to tell Computers and Humans Apart. Its primary purpose is to prevent automated abuse of web applications at scale.
Websites deploy CAPTCHA to protect sensitive or high-risk actions such as account registration, login attempts, password resets, checkout flows, and form submissions. These endpoints are common targets for bots that brute-force credentials, scrape proprietary data, generate fake accounts, or overwhelm backend systems with automated traffic.
Early CAPTCHA systems relied on explicit challenges like distorted text or image selection, assuming visual reasoning was difficult for machines. That assumption no longer holds. Advances in automation and machine learning forced CAPTCHA systems to evolve beyond simple puzzles.
Modern CAPTCHA implementations focus on risk reduction rather than user verification alone. They aim to introduce friction only when traffic appears suspicious, allowing legitimate users to proceed uninterrupted while slowing down or blocking automated behavior.
Read More: Captcha Test Case
How CAPTCHA Detection Works in Modern Browsers
Modern CAPTCHA systems operate largely behind the scenes. Instead of immediately presenting a challenge, they assess risk by collecting and correlating multiple browser and behavior signals in real time.
Detection typically begins as soon as a page loads or a request is made. The browser environment is evaluated for indicators that suggest automation, such as inconsistent feature support, abnormal rendering behavior, or known automation APIs. These signals are combined with interaction data collected as the user navigates the page.
Common detection signals include:
- Browser fingerprint consistency, including canvas rendering, WebGL output, fonts, and feature availability
- Interaction timing patterns such as mouse movement cadence, scrolling behavior, focus changes, and keystroke intervals
- Execution environment indicators like headless mode, sandboxed runtimes, or automation hooks
- Network-level signals including IP reputation, ASN patterns, proxy usage, and request frequency
Each signal contributes to a risk score. If the score stays below a threshold, the user sees no CAPTCHA at all. If it exceeds the threshold, a visible challenge may appear or requests may be throttled or blocked entirely.
This layered approach makes CAPTCHA difficult to predict and harder to “solve,” because detection often occurs before any visible UI element is rendered.
Read More: Why is Captcha not showing in Chrome?
Why CAPTCHAs Break Playwright Automation
Playwright tests behave like bots by design. They execute scripted actions, run in controlled environments, and often originate from cloud infrastructure. These characteristics overlap directly with the signals CAPTCHA systems are trained to detect.
Automation commonly breaks when tests run in headless mode, reuse identical interaction patterns across runs, or execute faster and more consistently than human users. Even when tests simulate user actions correctly at the UI level, underlying browser signals can still flag automation.
Additional factors that increase detection risk include:
- Running tests from shared CI IP ranges associated with automation traffic
- Executing tests in parallel at high volume
- Using default browser configurations without variability
- Skipping natural interaction delays or human-like input patterns
As a result, tests may pass locally and fail in CI, or pass intermittently without any application changes. CAPTCHA is not reacting to UI behavior alone; it is responding to the broader execution context.
This is why treating CAPTCHA as a flaky UI component leads to unstable test suites. The failure is systemic, not incidental.
Read More: How to handle Captcha in Selenium
Is Bypassing CAPTCHA Legal and Ethical in 2026?
Bypassing CAPTCHA raises both legal and ethical concerns, especially as CAPTCHA systems are explicitly designed as security controls. In many jurisdictions, intentionally circumventing protective measures can violate terms of service, contractual agreements, or anti-abuse regulations.
From a legal standpoint, automated CAPTCHA bypass may be considered unauthorized access if it circumvents safeguards put in place to restrict automated usage. This risk increases when bypass techniques involve reverse engineering, third-party solvers, or manipulation of security mechanisms without explicit permission.
Ethically, CAPTCHA bypass introduces additional concerns. It can expose systems to abuse, undermine user trust, and blur the line between legitimate testing and malicious automation. In regulated industries, bypassing CAPTCHA may also conflict with compliance requirements around data protection and access control.
Because of these risks, most teams avoid direct CAPTCHA bypass in production-like environments. Instead, they rely on safer alternatives such as disabling CAPTCHA in test environments, using allowlisted test keys, or designing test flows that validate functionality without triggering CAPTCHA checks.
Read More: Get Element Text with Playwright
Types of CAPTCHAs Commonly Encountered in Web Apps
Web applications typically encounter several categories of CAPTCHA, each with different implications for automation and testing.
- reCAPTCHA v2 and similar checkbox-based systems: These present visible challenges such as image selection or checkboxes. While familiar, they are often backed by behavior analysis and are rarely as simple as they appear.
- Score-based CAPTCHAs (reCAPTCHA v3 and equivalents): These do not display a challenge by default. Instead, they assign a risk score based on observed behavior and only block or challenge traffic when the score is low. These systems are especially disruptive to automation because failures occur without visible cues.
- Image-based and puzzle CAPTCHAs: These require users to solve visual or logic-based tasks. While increasingly rare, they are still used in high-risk flows and are intentionally difficult for automation to handle reliably.
- Behavioral and invisible CAPTCHAs: These rely entirely on interaction analysis and environmental signals. No explicit challenge is shown, making failures harder to diagnose and reproduce in tests.
Understanding which type of CAPTCHA is in use is essential. The testing strategy that works for a visible challenge often fails entirely against invisible or behavior-based systems, especially in automated Playwright environments.
Can Playwright Truly Bypass CAPTCHA in 2026?
Playwright cannot reliably bypass CAPTCHA in 2026 in a way that is stable, scalable, and compliant. CAPTCHA systems are engineered to detect automation across browser behavior, execution environment, and network signals, many of which sit outside Playwright’s control. Any technique that appears to work is usually exploiting a temporary detection gap rather than addressing the underlying mechanism.
- CAPTCHA detection often happens before a visible challenge is rendered
- Playwright can control browser actions but not backend risk scoring
- Techniques that pass locally tend to fail in CI and parallel runs
- Detection logic continuously evolves, shrinking the lifespan of bypass workarounds
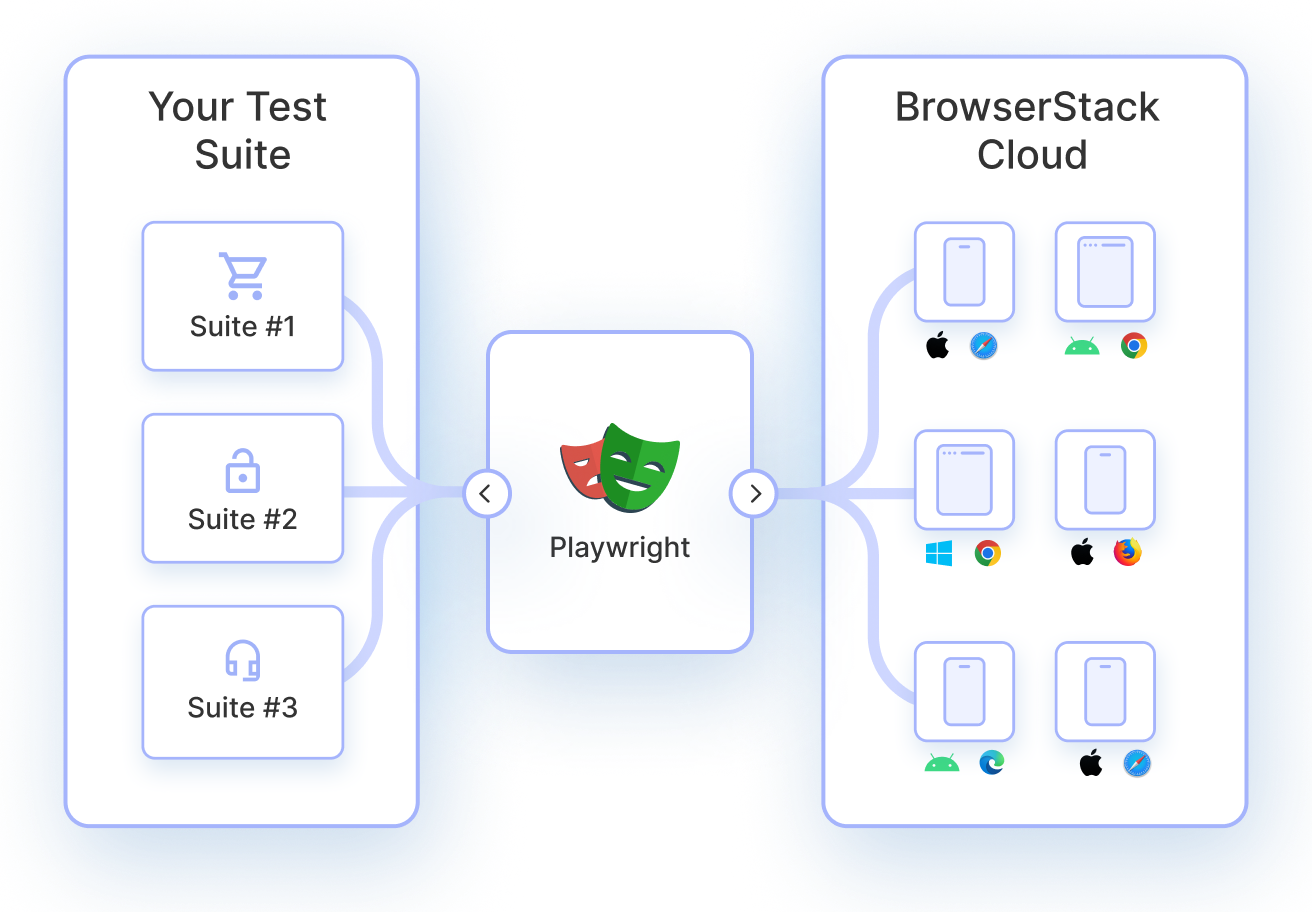
Direct CAPTCHA bypass is unreliable because automation-heavy environments trigger detection before Playwright ever interacts with the UI. With BrowserStack Automate, Playwright tests run on real browsers and operating systems, producing user-like signals that help validate CAPTCHA-safe flows without relying on brittle bypass techniques.
Common CAPTCHA Bypass Approaches with Playwright
Most CAPTCHA bypass attempts fall into predictable categories. These approaches focus on masking automation signals instead of eliminating detection.
- Running browsers in headed mode to avoid basic headless checks
- Modifying user-agent strings, viewport size, timezone, and locale
- Injecting stealth scripts to hide automation-related browser APIs
- Reusing cookies or sessions captured from manual browser runs
- Using third-party CAPTCHA solvers or external APIs
- Stubbing CAPTCHA-related network requests
Example of attempting to override browser context signals:
const context = await browser.newContext({ userAgent: ‘Mozilla/5.0 (Windows NT 10.0; Win64; x64)’,
viewport: { width: 1280, height: 720 },
locale: ‘en-US’,
timezoneId: ‘America/New_York’,
});These tactics may reduce basic detection but do not address behavior scoring or infrastructure signals.
Why Most CAPTCHA Bypass Techniques Fail in CI Environments?
CI environments amplify automation signals that CAPTCHA systems are trained to detect. Even realistic Playwright scripts cannot mask the execution context.
- Tests run from cloud IP ranges with poor reputation
- Parallel execution creates repeatable interaction patterns
- Machine-speed execution removes natural human variance
- Identical browser fingerprints appear across workers
This is why CAPTCHA failures often surface only after tests move into pipelines.
Safer Alternatives to CAPTCHA Bypass for Test Automation
Stable automation avoids CAPTCHA rather than attempting to defeat it. Safer approaches separate security validation from functional testing.
- Disable CAPTCHA in non-production environments
- Validate CAPTCHA behavior independently from core flows
- Test business logic without triggering security gates
- Assert outcomes before and after CAPTCHA checkpoints
These approaches reduce flakiness while preserving intent.
Read More: Web Scraping with Playwright
How Teams Handle CAPTCHA in Test and Staging Environments
Most teams treat CAPTCHA as environment-specific infrastructure, not application logic.
- Production retains full CAPTCHA enforcement
- Test and staging environments bypass CAPTCHA deterministically
- QA environments simulate pass or fail outcomes
- Automation avoids solving CAPTCHA challenges
This separation keeps security intact without destabilizing test suites.
Using Feature Flags and Test Keys to Disable CAPTCHA
Feature flags and test keys provide controlled mechanisms for managing CAPTCHA behavior.
- CAPTCHA providers support allowlisted domains or keys
- Feature flags toggle CAPTCHA by environment or user role
- Configuration remains auditable and reversible
- Application logic remains unchanged
Example using an environment flag:
if (process.env.DISABLE_CAPTCHA === ‘true’) { app.use(disableCaptchaMiddleware());
}Testing CAPTCHA-Protected Flows Without Solving CAPTCHA
CAPTCHA-protected flows can be tested effectively without attempting to solve or bypass the CAPTCHA itself. The goal is to validate application behavior around the security checkpoint, not to defeat the security mechanism.
- Assert CAPTCHA rendering and placement: Verify that CAPTCHA appears on the correct pages and is tied to the intended actions, such as form submission or login attempts. This confirms that CAPTCHA is wired correctly without interacting with the challenge.
await expect(page.locator(‘#captcha-container’)).toBeVisible();
- Validate blocking behavior when CAPTCHA is not completed: Ensure that protected actions are blocked if CAPTCHA verification is missing or fails. This confirms enforcement logic without requiring a successful solve.
await page.click(‘button.submit’);await expect(page.locator(‘.error-message’)).toContainText(‘Verification required’);
- Simulate successful verification in test environments:In non-production environments, configure the application or backend to treat CAPTCHA as passed using test keys or feature flags. This allows tests to continue through protected flows deterministically.
- Verify downstream behavior after CAPTCHA clearance: Once CAPTCHA is marked as successful, validate redirects, state changes, API calls, and UI updates that follow the protected action.
- Separate CAPTCHA validation from business logic tests: Keep CAPTCHA-specific checks isolated. Functional tests should focus on business outcomes, not security challenges, to avoid brittle and slow automation.
This approach preserves coverage, avoids insecure bypass techniques, and keeps Playwright test suites stable as CAPTCHA detection evolves.
Testing CAPTCHA-protected flows does not require solving CAPTCHA challenges. With BrowserStack Automate, Playwright tests can run on real browsers to validate pre- and post-CAPTCHA behavior under production-like conditions, ensuring protected flows work as expected without introducing insecure bypass logic.
How Browser Fingerprinting Impacts CAPTCHA in Automation
Browser fingerprinting is a primary detection mechanism used by modern CAPTCHA systems.
- Canvas and WebGL rendering differences expose automation
- Feature availability reveals headless or scripted environments
- Timing consistency signals non-human interaction
- Identical fingerprints across runs increase confidence
Automation scripts often produce clean, repeatable fingerprints that are easy to classify.
Playwright Limitations When Dealing with CAPTCHA
Playwright is a browser automation framework, not a security evasion tool. Its architecture and design impose clear limits when interacting with CAPTCHA systems, which operate largely outside the browser automation layer.
- No visibility into server-side risk scoring: CAPTCHA decisions are made by backend systems that evaluate behavior, reputation, and historical signals. Playwright has no access to these models or the criteria used to classify traffic as human or automated.
- No control over IP reputation or infrastructure signals: Tests typically run from cloud or CI infrastructure with IP ranges commonly associated with automation. Playwright cannot influence ASN reputation, proxy classification, or network trust signals used by CAPTCHA providers.
- Limited influence over browser fingerprinting: While Playwright can adjust surface-level settings like user agent or viewport, deeper fingerprint signals such as canvas rendering, WebGL output, font availability, and feature consistency remain largely deterministic and detectable at scale.
- Behavioral realism is constrained: Playwright scripts execute with consistent timing and interaction patterns. Even when delays are added, the overall behavior lacks the natural variance seen in human interactions, which CAPTCHA systems use as a strong detection signal.
- Third-party CAPTCHA logic is opaque: CAPTCHA providers continuously update detection heuristics without notice. Playwright tests cannot anticipate or adapt to these changes, making any workaround brittle by default.
- Increased complexity does not reduce detection: Adding stealth scripts, overrides, or conditional logic increases test complexity without addressing the root causes of detection. This often leads to fragile tests that are harder to debug and maintain.
These limitations explain why CAPTCHA-related failures are systemic rather than incidental. Treating CAPTCHA as a UI problem to solve with Playwright scripts leads to unstable automation, especially in CI and large-scale test environments.
Security Risks of CAPTCHA Bypass in Automation Pipelines
Bypassing CAPTCHA in automation pipelines introduces risks that extend beyond test stability. CAPTCHA is a security control, and deliberately circumventing it can create legal, operational, and compliance exposure for engineering teams.
- Circumventing active security controls: CAPTCHA is explicitly designed to restrict automated access. Bypass logic treats a security boundary as a test obstacle, which can normalize behavior that closely resembles malicious automation.
- Potential violations of terms of service: Many CAPTCHA providers and platforms prohibit automated circumvention. Embedding bypass techniques or third-party solvers in pipelines can violate contractual agreements or usage policies.
- Increased attack surface in CI environments: Introducing bypass scripts, solver integrations, or request manipulation increases the complexity of CI pipelines. This expands the surface area for misconfiguration, credential leaks, or unintended exposure.
- Audit and compliance risks: In regulated industries, intentionally disabling or circumventing security mechanisms can raise audit flags. Automation pipelines that bypass CAPTCHA may conflict with internal security standards or external compliance requirements.
- Encouraging insecure testing patterns: Once bypass logic exists in test code, it often spreads to other flows. This makes it harder to reason about which environments enforce real security controls and which do not.
- Long-term maintenance and liability: CAPTCHA detection evolves continuously. Maintaining bypass logic requires constant updates and creates technical debt with potential legal implications if misused or misinterpreted.
Because of these risks, most teams avoid CAPTCHA bypass in automation pipelines altogether. Treating CAPTCHA as an environment-level concern rather than a test problem keeps security boundaries clear and reduces both technical and organizational risk.
How BrowserStack Automate Helps Test CAPTCHA-Safe Flows
BrowserStack Automate allows Playwright tests to run in environments that closely resemble real user traffic, reducing false positives triggered by automation-heavy CI setups.
Why real browsers matter for CAPTCHA scenarios
- Real browsers produce natural rendering and interaction behavior
- Environment signals align more closely with human usage
- Detection confidence drops when fingerprints resemble real users
Key capabilities of Automate for CAPTCHA-aware testing
- Real desktop and mobile browsers across OS combinations
- Stable infrastructure with user-like traffic patterns
- Parallel execution without shared fingerprint artifacts
- Native CI integration for scalable test runs
Best Practices for CAPTCHA-Friendly Test Design
CAPTCHA-friendly automation focuses on predictability and separation of concerns.
- Avoid CAPTCHA-triggering paths in functional tests
- Disable CAPTCHA using approved configuration
- Validate CAPTCHA behavior separately from business logic
- Prefer real-browser execution for production-like signals
- Keep test code free of solver or bypass logic
Conclusion
CAPTCHA bypass is not a sustainable automation strategy in 2026. Detection systems operate at behavioral, environmental, and infrastructure layers that Playwright cannot fully control.
Reliable automation comes from respecting CAPTCHA as a security boundary, isolating it by environment, and running tests in real browser conditions. Teams that adopt this approach build test suites that scale without flakiness, risk, or compliance exposure.